High Performance Backend for Talk on Nextcloud with Docker
Talk:HPB
- Nextcloud Talk documentation
- How to install and configure Talk:HPB for Nextcloud with docker
- How to install and configure Talk:HPB from source by sunweaver, by C. Rieger or by decatec
A High Performance Backend (HPB) requires a signalling service and consists of three components working hand in hand;
- STUN service (Session Traversal Utilities for NAT) for discovering NATed/firewalled external IP’s. Nextcloud provides a default STUN server but can be replaced with your own.
- Examples:
stun.nextcloud.com:443orstun.yourdomain.tld:3478or both
- Examples:
- TURN service (Traversal Using Relays around NAT) like “coturn” or “eturnal” for connecting NATed/firewalled external IP’s and controlling WebRTC streams. Its main role is to help WebRTC clients behind routers to communicate and relays the audio and video data through firewalls and port restrictions.
- Examples:
turn.yourdomain.tld:3478oryourdomain.tld:3478 - Encryption is optional for TURN & STUN and will be handled by encrypted Nextcloud
- Examples:
- WebRTC Signalling service like “Janus WebRTC server” or “Spreed WebRTC server” is required for calls and conversations with multiple participants. The signaling server is used to establish a WebSocket connection between the participants in the call. Without it, all participants would have to upload their own audio/video individually for each other participant causing connectivity issues.
- Example:
https://signal.yourdomain.tld
- Example:
Self-hosting all three services is not as daunting as it seems and thanks to the folks at Nextcloud AIO is easily accomplished using their docker image.
This example will require Docker and a reverse proxy for forwarding and encrypting HTTP & WSS for port 8181 to https://signal.yourdomain.tld
Prepare router/firewall & reverse proxy
- Allow inbound bypass for TURN & STUN on port 3478 tcp/udp which must be internet facing in router/firewall (i.e your.domain.tld:3478)
- encryption is optional for TURN & STUN as it will be handled by encrypted Nextcloud
- Set reverse proxy host for signal domain to forward and encrypt HTTP & WSS (Websockets Support) for port 8181 to
https://signal.yourdomain.tld
TIP: create
secretpasswordkeyMake sure you create a long
secretpasswordkey(min. 24 chars, better 32 chars) for each service! Note down thesecretpasswordkeysas you will need them for creating the Docker stack and for configuring HPB in Nextcloud talk.
- issue command in host shell and repeat for each service:
openssl rand -hex 32
1. TURN_SECRET
- create a long random
secretpasswordkey, issue command in host shell:openssl rand -hex 322. SIGNALING_SECRET
- create a long random
secretpasswordkey, issue command in host shell:openssl rand -hex 323. INTERNAL_SECRET
- create a long random
secretpasswordkey, issue command in host shell:openssl rand -hex 32
Create and run Docker Stack
- or create a
docker-compose.yamlin place and execute in docker
name: 'hpb'
services:
nc-talk:
container_name: talk_hpb
image: ghcr.io/nextcloud-releases/aio-talk:latest
init: true
ports:
- 3478:3478/tcp
- 3478:3478/udp
- 8181:8081/tcp
environment:
- NC_DOMAIN=cloud.yourdomain.tld
- TALK_HOST=signal.yourdomain.tld
- TURN_SECRET=secretpassword #this must be a long secretpasswordkey
- SIGNALING_SECRET=secretpassword #this must be a long secretpasswordkey
- TZ=Europe/Berlin
- TALK_PORT=3478
- INTERNAL_SECRET=secretpassword #this must be a long secretpasswordkey
restart: unless-stopped
Upgrade Talk:HPB Docker image
- stop docker container see Docker stop
- remove image see Docker rm
- start docker stack see Docker compose start
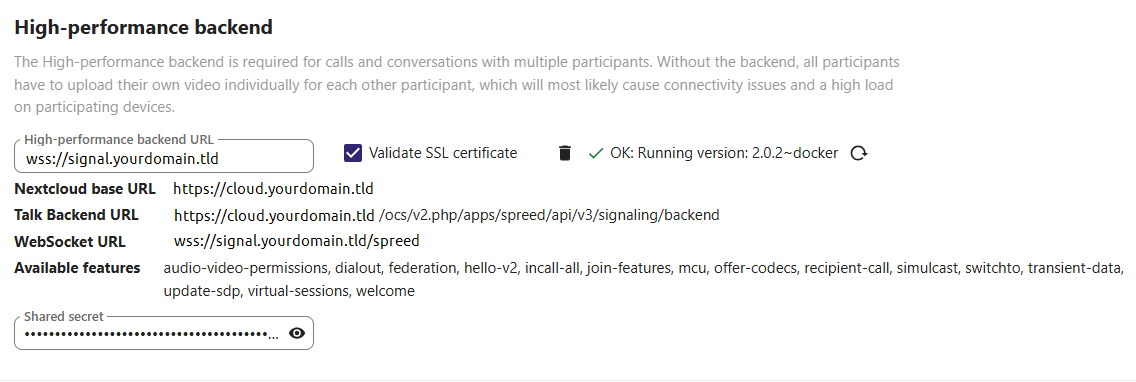
Configure Nextcloud Talk
Example Nextcloud STUN configuration,
Example Nextcloud TURN configuration
Examples Nextcloud HPB configuration
Example 1
Example 2
Reverse proxy documentation
Example NPM reverse proxy manager configuration"
Example Apache reverse proxy configuration"
for websocket upgrade (2.4.47 and later) in apache version
set
ProxyPass / http://192.168.2.xx:8181/ upgrade=websocket
and:
RequestHeader set X-Forwarded-Proto expr=%{REQUEST_SCHEME}
RequestHeader set X-Real-IP expr=%{REMOTE_ADDR}
as mentioned strukturag/nextcloud-spreed-signaling: Standalone signaling server for Nextcloud Talk.
or mod_proxy_wstunnel - Apache HTTP Server Version 2.4 and mod_proxy - Apache HTTP Server Version 2.4
Troubleshooting
connection errors
403 forbidden
TIP
make sure you have a long
secretpasswordkey(min. 24 chars, better 32 chars) for each service!