Hello, currently I am trying to set up Collabora Online for document editing but I am running into a wall. I run a dockerized instance of nextcloud and Collabora. For this, I referenced this awesome guide: Collabora integration guide
I went through the troubleshooting checklist and I can’t get my containers to see each other, ie verify access to collabora via nextcloud and vice versa is not available. From my host machine I can access them both.
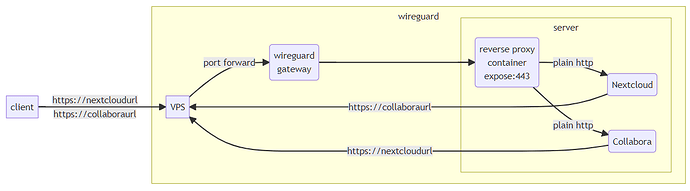
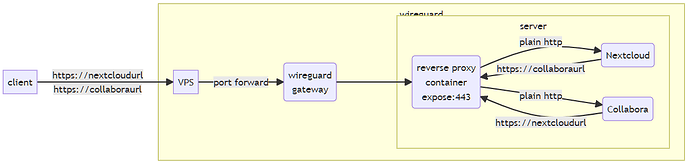
My ISP does not grant me a static IP and I am behind a carrier-grade-NAT (CG-NAT). Therefore I rented a virtual private server (VPS) which hosts an Ubuntu VM with wireguard. My home server runs debian with openmediavault and docker. I connected my home-server and vps via a wireguard tunnel (forwarding all traffic exept ssh to my home-server). On my home server I use Nginx-Proxy-Manager to manage certificates and forwarding.
My nextcloud instance is forwarded to https://cloud.server.de
My Collabora instance is forwarded to https://office.server.de
From my separate computer I get all the results I exspect to be there. Ping works. Curl gives the outputs the guide sais it should.
From my homeserver I can ping the relevant urls, but curl throws an error. From each docker container same result.
That is why I believe it either has something to do with DNS, with firewall or wireguard. I’ve thrown my head against the wall but I don’t have the knowledge on how to further diagnose this issue.
root@nextcloud:/# ping -c2 office.server.de
PING office.server.de (212.xxx.xxx.xxx): 56 data bytes
64 bytes from 212.xxx.xxx.xxx: seq=0 ttl=63 time=14.913 ms
64 bytes from 212.xxx.xxx.xxx: seq=1 ttl=63 time=14.808 ms
--- office.server.de ping statistics ---
2 packets transmitted, 2 packets received, 0% packet loss
round-trip min/avg/max = 14.808/14.860/14.913 ms
root@nextcloud:/# curl https://office.server.de/hosting/discovery
curl: (7) Failed to connect to office.server.de port 443 after 22 ms: Couldn't connect to server
If relevant, here would be my respective docker-compose files:
collabora
---
version: "2"
services:
collabora:
image: collabora/code:latest
container_name: collabora
cap_add:
- MKNOD
ports:
- "9980:9980"
environment:
- aliasgroup1=https://nextcloud.server.de
- username=admin
- password=admin
- "extra_params=--o:ssl.enable=false --o:ssl.termination=true"
volumes:
- /etc/localtime:/etc/localtime:ro
nextcloud
version: "2"
services:
nextcloud:
image: lscr.io/linuxserver/nextcloud:27.1.1
container_name: nextcloud
environment:
- PUID=1000
- PGID=1000
- TZ=Europe/Berlin
volumes:
- ./nextcloud-config/nextcloud:/config
- ./nextcloud-data/data:/data
ports:
- 42351:443
restart: unless-stopped
depends_on:
- nextcloud_db
nextcloud_db:
image: linuxserver/mariadb:latest
container_name: nextcloud_db
environment:
- PUID=1000
- PGID=1000
- MYSQL_ROOT_PASSWORD=root_pw
- TZ=Europe/Berlin
- MYSQL_DATABASE=nextcloud_db
- MYSQL_USER=nextcloud
- MYSQL_PASSWORD=db_pass
volumes:
- ./nextcloud-config/db:/config
restart: unless-stopped
wireguard config - vps
[Interface]
PrivateKey = somethingsomethingsomethingprivate
ListenPort = 51280
Address = 10.0.0.1/24
MTU = 1500
PostUp = iptables -t nat -A PREROUTING -p tcp -i ens192 '!' --dport 22 -j DNAT --to-destination 10.0.0.2; iptables -t nat -A POSTROUTING -o ens192 -j SNAT --to-source 212.xxx.xxx.xxx
PostUp = iptables -t nat -A PREROUTING -p udp -i ens192 '!' --dport 51280 -j DNAT --to-destination 10.0.0.2;
PostDown = iptables -t nat -D PREROUTING -p tcp -i ens192 '!' --dport 22 -j DNAT --to-destination 10.0.0.2; iptables -t nat -D POSTROUTING -o ens192 -j SNAT --to-source 212.xxx.xxx.xxx
PostDown = iptables -t nat -D PREROUTING -p udp -i ens192 '!' --dport 51280 -j DNAT --to-destination 10.0.0.2;
#NAS
[Peer]
PublicKey = somethingsomethingsomethingpublic
AllowedIPs = 10.0.0.2/32
wireguard config - homeserver
[Interface]
PrivateKey = privatekey
Address = 10.0.0.2/24
MTU = 1500
DNS = fritz.box
[Peer]
PublicKey = publickey
AllowedIPs = 0.0.0.0/0
Endpoint = server.de:51280
PersistentKeepalive = 25