Nextcloud version (eg, 20.0.5): 23
Operating system and version (eg, Ubuntu 20.04): unraid
Apache or nginx version (eg, Apache 2.4.25): nginx reverse proxy v2.9.12
PHP version (eg, 7.4): replace me
The issue you are facing:
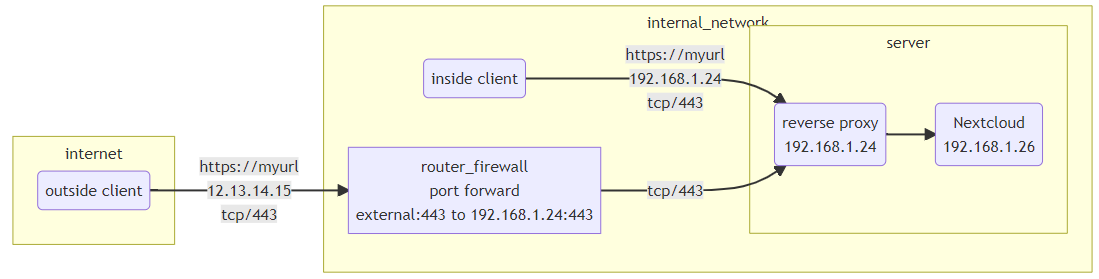
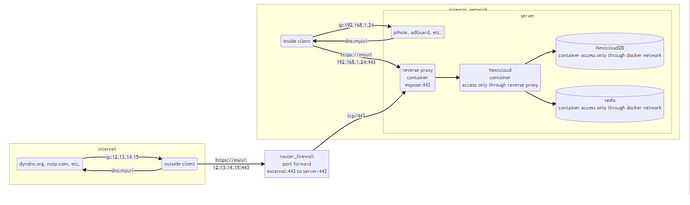
Can acces from outside but not from LAN
Is this the first time you’ve seen this error? Y
Steps to replicate it:
- Install mariadb docker
- Install nextcloud docker
- Config nextcloud to point mariadb and create admin user
- All works (only inside lan)
- Modify config.php so can use nginx reverse proxy
- From WAN works OK, from lan stops working. Inside lan redirects to mynextcloud.duckdns.org but nothing or error on browser.
The output of your Nextcloud log in Admin > Logging:
PASTE HERE
The output of your config.php file in /path/to/nextcloud (make sure you remove any identifiable information!):
GNU nano 5.3 config.php
<?php
$CONFIG = array (
'memcache.local' => '\\OC\\Memcache\\APCu',
'datadirectory' => '/data',
'instanceid' => 'XXXXXXXXXX',
'passwordsalt' => 'XXXXXXXXXXXXXXXXXXXXXXXXXXXXXX',
'secret' => 'XXXXXXXXXXXXXXXXXXXXXXX',
'trusted_domains' =>
array (
0 => '192.168.1.20',
1 => 'mynextcloud.duckdns.org',
),
'trusted_proxies' =>
array (
0 => '192.168.2.2',
),
'dbtype' => 'mysql',
'version' => '23.0.0.10',
'overwrite.cli.url' => 'https://mynextcloud.duckdns.org',
'overwritehost' => 'mynextcloud.duckdns.org',
'overwriteprotocol' => 'https',
'dbname' => 'nextcloud',
'dbhost' => '192.168.2.10:3306',
'dbport' => '',
'dbtableprefix' => 'oc_',
'mysql.utf8mb4' => true,
'dbuser' => 'nextcloud',
'dbpassword' => 'XXXXXXXXXXXX',
'installed' => true,
);
The output of your Apache/nginx/system log in /var/log/____:
Don't find it on my unraid server