In fact you don’t want two domains. This is complete hassle if you try to collaborate - e.g. share files with others - you need to now https://mynas.internalurl/somefile2345 is the same as https://cloud.externalurl/somefile2345. and as you move around you need to adopt your client/browser to connect with “another” system… It’s very hard or even impossible when you build more complex setup e.g. nextcloud-office or collabora-online
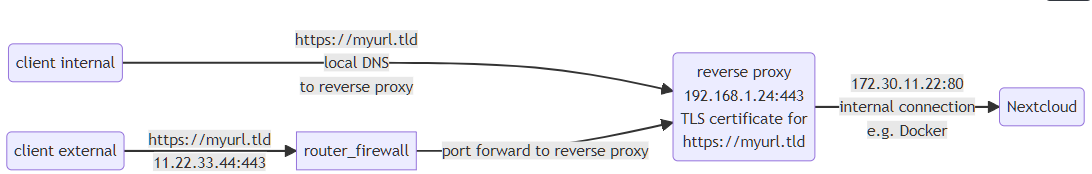
The solution for you issue is called “split brain” or “split horizon” DNS. The idea is to create a local DNS record for your public DNS inside of your network pointing to a local IP of the system (in your case reverse proxy). Then you can access your system using public DNS but local IP from your network. Everything else remains unchanged: same URLs, same TLS certificate, very similar connection path (starting with reverse proxy). splitbraindns
Simple architecture:
more detailed drawing you find here: