This is not a perfect formula by any means, but suggestions follow.
The best security is to never put sensitive data online.
" We have an illusion of security, we don’t have security, but we can still have best practices. "
Please consider helping out to expand these sections, you can contact the wiki team at Matrix or Telegram
These steps are merely a couple of good measures to take if you intend to expose your NextcloudPi instance to the internet, please keep in mind that it would be quite a feat of accomplishent if anyone could cover everything related to security in one article or even a couple, and as we all know, no one person can know everything.
All things considered, a VPN is the recommended way if you need to access your system from outside your home and don’t want to or have the time to consider and go through all the security implications that comes with opening up your network directly to the internet via port forwarding.
Why is that?
To that I will say, in my experience, it’s simply because you need to maintain a certain level of familiarity and knowledge/understanding of your system/network and to keep up with the times, learning of new exploits, vulnerabilities and weaknesses as they are discovered, because sometimes, the patches for these require action on the part of the system/network administrator, which in this case would be you.
Understandably not everyone has the time to keep up with this ![]() and using a VPN is a good way of keeping the things you need to be mindful of to a minimum in the long-run while still having good security by not exposing your home network to direct access from the internet.
and using a VPN is a good way of keeping the things you need to be mindful of to a minimum in the long-run while still having good security by not exposing your home network to direct access from the internet.
Create a new admin user for your NCP instance.
ncpis the username for the default admin user on the NextcloudPi instance when initiated.
Please change this to something else by creating a new admin user and delete the default one.
It is always best to delete if possible, else disable or deny access to default admin users as much as possible. This is due to the simple fact that they are very well known and is the equivalent of compromised information.
The new admin-user should preferably only be used for maintenance, installation or configuration of new apps & monitoring tasks or things like that.
It should not be your every day-to-day user.
Create a new user for daily use
On the same page where you are creating your new admin user you can also create your new daily user. Your daily user account should not have administrative access to your device. This is a good security practice, plus you can still allow your user to receive administrative notifications under Settings.
Add your new daily user to the Users group (or whatever name you choose to call it)
Create a new sudo-user & delete pi user
See the steps in the following article to create a new sudo user & delete pi user
SSH & public-key authentication
This article will help you with creating a public-key pair for public-key (or pubkey) authentication on SSH connections to your device with the NCP instance.
NextcloudPi Settings
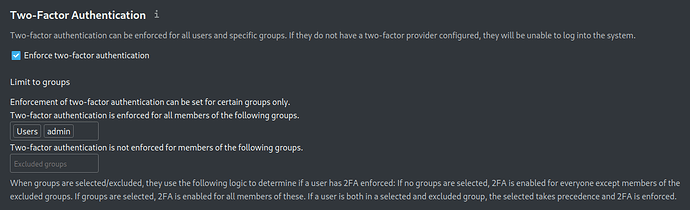
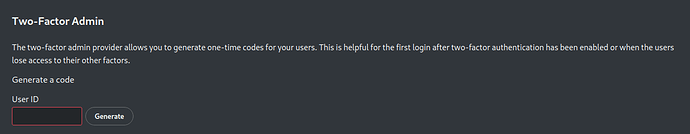
Force 2FA for all users & enable 2FA Admin Support
2FA Admin Support allows admins to generate a one-time code for users to login to a 2FA protected account. This is helpful in situations where users have lost access to their other 2FA methods or mandatory 2FA without any previously enabled 2FA provider. And 2FA TOTP is a 2FA provider enabling users to use their authenticator apps to generate one-time codes to login to their Nextcloud account.
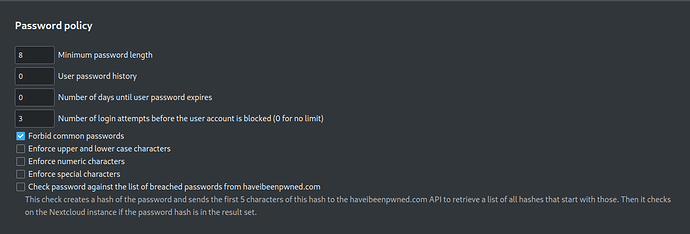
Enable Password Policy app
The password policy app enables admins to set password policies for their Nextcloud users.
Enable HSTS-header
HTTP Strict Transport Security is a policy mechanism that helps to protect websites against man-in-the-middle attacks such as protocol downgrade attacks [1] and cookie hijacking.
It allows web servers to declare that web browsers (or other complying user agents) should automatically interact with it using only HTTPS connections, which provide Transport Layer Security (TLS/SSL), unlike the insecure HTTP used alone. HSTS is an IETF standards track protocol and is specified in RFC 6797.
The HSTS Policy is communicated by the server to the user agent via an HTTP response header field named “Strict-Transport-Security”. [1]
HSTS Policy specifies a period of time during which the user agent should only access the server in a secure fashion. [2]
Websites using HSTS often do not accept clear text HTTP, either by rejecting connections over HTTP or systematically redirecting users to HTTPS (though this is not required by the specification). The consequence of this is that a user-agent not capable of doing TLS will not be able to connect to the site.
The protection only applies after a user has visited the site at least once, relying on the principle of Trust on first use. The way this protection works is that a user entering or selecting a URL to the site that specifies HTTP, will automatically upgrade to HTTPS, without making an HTTP request, which prevents the HTTP man-in-the-middle attack from occurring.
Enable E2E Encryption & App passwords for sync clients (Mobile & Desktop)
You can also use the QR code for the mobile client which automatically generates a token or an app password for the device.
Disable the Web-UI.
- Use
sudo ncp-configfrom the command line usingSSHor a TTL serial USB cable instead for admin tasks.
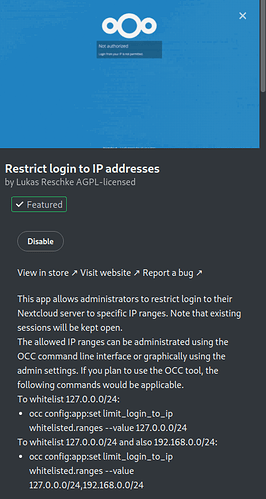
Restrict Login by IP (app)
Can be used to only allow specified IP addresses to login.
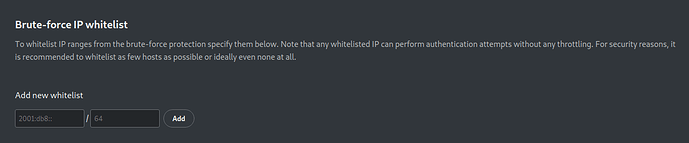
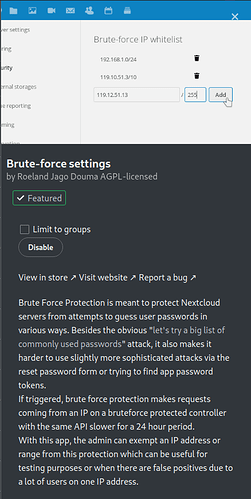
Brute Force (app)
Blocks users with multiple failed login attempts and adds them to a ban list
Monitor apps/tools
This article holds a list of some locations for various logs on NCP.

Enable Ransomware Protection (Optional)
This one can be good if you have multiple users or worried about being injected with malicious code through file uploads however, if you are a Developer using the nextcloudpi instance, this tool will block several .lock, .yaml and such types files from uploading and so if you backup your code this way you will need to disable this tool.
GeoBlocker (app)
Disable login access by IP Address location and define allow/block lists by country of origin
Enable fail2ban – included in curl script.
Fail2Ban scans log files like
/var/log/auth.logand bans IP addresses conducting too many failed login attempts. It does this by updating system firewall rules to reject new connections from those IP addresses, for a configurable amount of time. Fail2Ban comes out-of-the-box ready to read many standard log files, such as those for sshd and Apache, and is easily configured to read any log file of your choosing, for any error you wish.
Though Fail2Ban is able to reduce the rate of incorrect authentication attempts, it cannot eliminate the risk presented by weak authentication. Set up services to use only two factor, or public/private authentication mechanisms if you really want to protect services.
Must be manually configured in Docker
user@hostname:~ $ sudo fail2ban-client status
Status
|- Number of jail: 9
`- Jail list: apache-auth, apache-botsearch, apache-fakegooglebot, apache-modsecurity, nc-error, nextcloud, script, sshd, ufwban
user@hostname:~ $ sudo fail2ban-client status sshd
Status for the jail: sshd
|- Filter
| |- Currently failed: 1
| |- Total failed: 17
| `- File list: /var/log/auth.log
`- Actions
|- Currently banned: 10
|- Total banned: 10
`- Banned IP list: 94.232.43.63 94.232.45.178 137.184.56.35 87.251.67.98 87.251.75.89 94.232.47.130 45.9.20.71 87.251.64.186 185.219.52.171 185.217.1.122
Suspicious Login
See this article about the Suspicious Login app.
Read Nextcloud Documentation - Hardening and security guidance
IMPORTANT
Updating Nextcloud causes incompatibility within the appstore, which will sometimes disable apps entirely as part of the update process. Any app from the Nextcloud appstore can break or be automatically disabled during updates if it is not compatible with the version you are installing. Therefore it’s recommended to disable all apps before a major version update, enable them one by one afterwards, checking for incompatibility when the upgrade is done & complete rather than during.
If NextcloudPi is intended to be used locally without external access
Place NextcloudPi on a subnet
Isolate your device from other traffic on your network via your router, this will stop guests from accessing it on your local area network.
Add Two Factor Authentication to your literal device, not just the NCP instance.
Here is guide for adding 2FA to a Raspberry Pi device.
Armbian 2FA is added using sudo armbian-config
You’ll need to use an Authenticator app to store your codes or within a Password Manager as One-Time-Passwords (OTP).
Disable SSH
If device is physically accessible and you own a TTL serial USB cable, around $5 – $10, to physically login to your device. This cable simulates a keyboard interface using GPIO pins. Do not disable SSH until you have a different method in place for interacting with your device.
Extra’s
-
Encrypt
/ncdatadirectory using Full Disk Encryption, eg. LUKS
Easiest to do pre-installation -
Route all traffic through Wireguard or OpenVPN using PiVPN
- Negates the need for port forwarding.
- Securely share any number of services from your local area network.
- Breaks all sharing and guest functionality since all access will require your explicit OpenVPN certificates or Wireguard authentication before gaining Nextcloud access.
Keep your device localhost only
Simply don’t bother to port forward or enable direct external access to your Nextcloud, stick to only accessing it from your local area network. Or join a hosted Nextcloud service provider for external access and federate that to your localhost instance. This way you can always tell what data you’ve made public because it is kept on an entirely different Nextcloud instance.
We hope this doc was helpful, if you encounter any issues please reach out to the community. These docs are written by volunteers, please consider becoming one of them, you can contact the wiki team at Matrix or Telegram
About the Author
This article was originally written by @anon75456558. It was expanded by @ZendaiOwl. Thank you so much for all you do! You may write your own articles by joining our wiki and documentation team on the forum.