Originally published at: Nextcloud will check passwords against database of HaveIBeenPwned - Nextcloud
Users tend to use the same passwords in multiple locations, which poses a significant risk in case passwords are stolen. Last Thursday, Security researcher Troy Hunt, known from his site HaveIBeenPwned, expanded his existing dataset of 306 million leaked passwords with another 200 million, bringing the total to half a billion. Organizations can use this list to check passwords against, ensuring their users don’t pick a password that is known and thus likely to be tried by hackers when trying to break into a system.
Pwned Passwords
His collection of passwords, named Pwned Passwords, uses SHA1 hashes of the passwords to allow checks against it. It also offers a counter to show how often a password is used in the database, with abc123 having a count of 2.5 million according to a blog by Hunt.In this blog, Hunt also explains he gathered the 8,8GB worth of passwords from a series of public leaks and he warns strongly against using passwords part of his collection. He made them available to be collectively downloaded via a torrent and on his website he offers an API which can be used to check passwords against. It is a common practice of both attackers and defenders in computing security to built lists of commonly passwords which are in turn used in so called Rainbow Tables which are used to recover username/password combinations from encrypted, stolen databases. Or, like in this case, to ensure users don’t use previously breached passwords.
[caption id=“attachment_4789” align=“alignnone” width=“1024”] online check against haveIBeenPwned database[/caption]
online check against haveIBeenPwned database[/caption]
Password security in Nextcloud
Currently, Nextcloud allows administrators to enforce a NIST compliant password quality, which includes a check for commonly used passwords like ‘test’ and 'abcabc. The limitations are checked when a user chooses a new password, or when the admin creates a new user with password. The new test against the HaveIBeenPwned database queries its database through their public API, giving a warning if the password has been breached.
As shipping a 8.8 gb password database alongside Nextcloud would probably make the download a little to big for most users. By sending a partial hash (the first five characters), we avoid any increased risk of leaking the password as, even if intercepted, those first 5 characters of a long hash aren’t very to helpful crack the full password. Besides, the attacker wouldn’t know the user name. The administrator can enable or disable this feature - we still have to determine if we’ll enable it by default but likely not.
[caption id=“attachment_4788” align=“alignnone” width=“703”]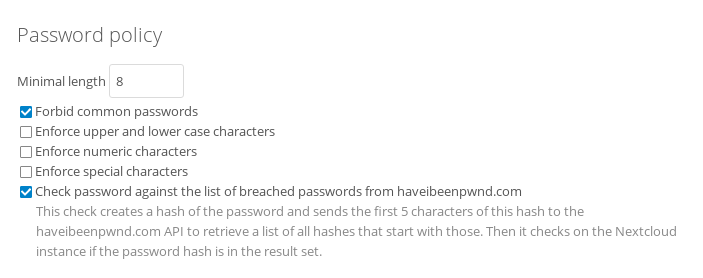 The new Password Policy settings in Nextcloud 13.0.1[/caption]
The new Password Policy settings in Nextcloud 13.0.1[/caption]
This improvement helps make passwords more secure, avoiding the use of known breached passwords and adding to our brute-force protection, two-factor authentication and existing password quality checks to ensure strong account protection.
The new check will be part of Nextcloud 14 and might also be backported to Nextcloud 13 in one of the upcoming patch releases. While this technically qualifies as a new feature (and backporting features always comes at a risk), password security is very central to keeping data under control and thus worthy of some extra testing effort. We still recommend to use the built in two-factor authentication to provide additional protection against stolen passwords!
Update: the code has been reviewed and merged and will be backported to 13.0.1. It will be disabled by default.
 and makes the API always return a match, would this effectively forbid all passwords? Or is this impossible because to match all hashes, the reply would have to be much larger?
and makes the API always return a match, would this effectively forbid all passwords? Or is this impossible because to match all hashes, the reply would have to be much larger?