Support intro
Sorry to hear you’re facing problems 
help.nextcloud.com is for home/non-enterprise users. If you’re running a business, paid support can be accessed via portal.nextcloud.com where we can ensure your business keeps running smoothly.
In order to help you as quickly as possible, before clicking Create Topic please provide as much of the below as you can. Feel free to use a pastebin service for logs, otherwise either indent short log examples with four spaces:
example
Or for longer, use three backticks above and below the code snippet:
longer
example
here
Some or all of the below information will be requested if it isn’t supplied; for fastest response please provide as much as you can 
Nextcloud version (eg, 20.0.5): 21.0.4
Operating system and version (eg, Ubuntu 20.04): Raspbian GNU/Linux 10 (buster)
Apache or nginx version (eg, Apache 2.4.25): Apache/2.4.38 (Raspbian)
PHP version (eg, 7.4): PHP 7.3.29-1~deb10u1 (cli)
The issue you are facing:
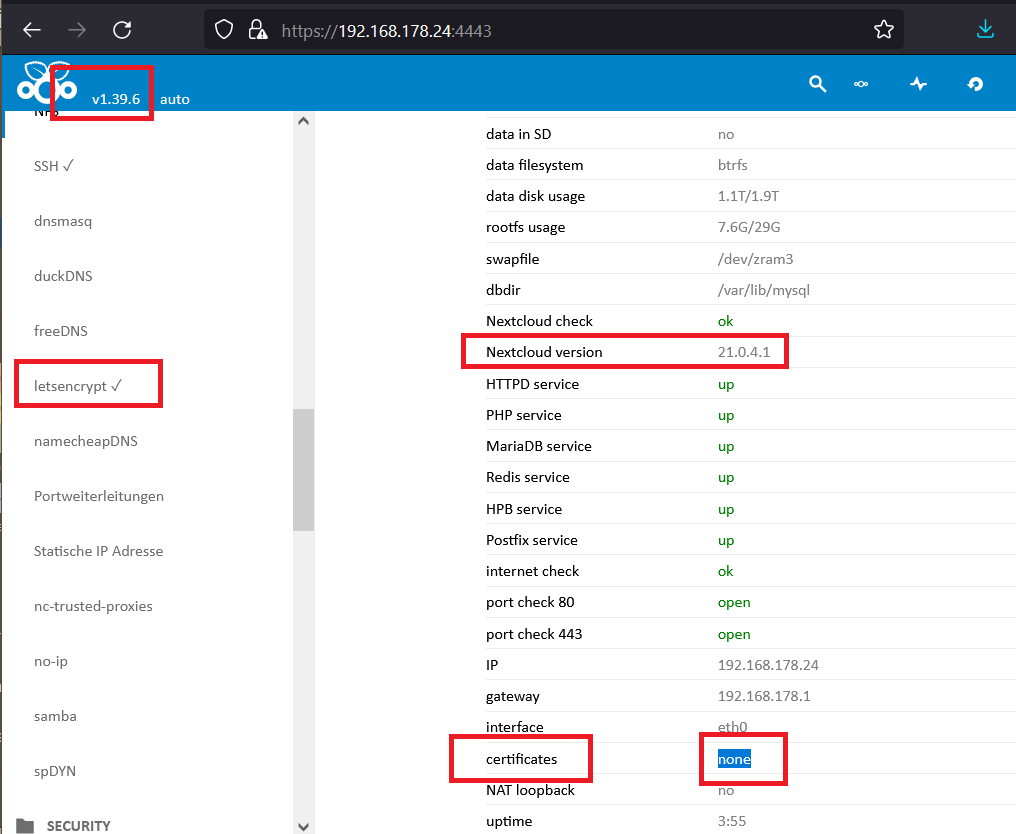
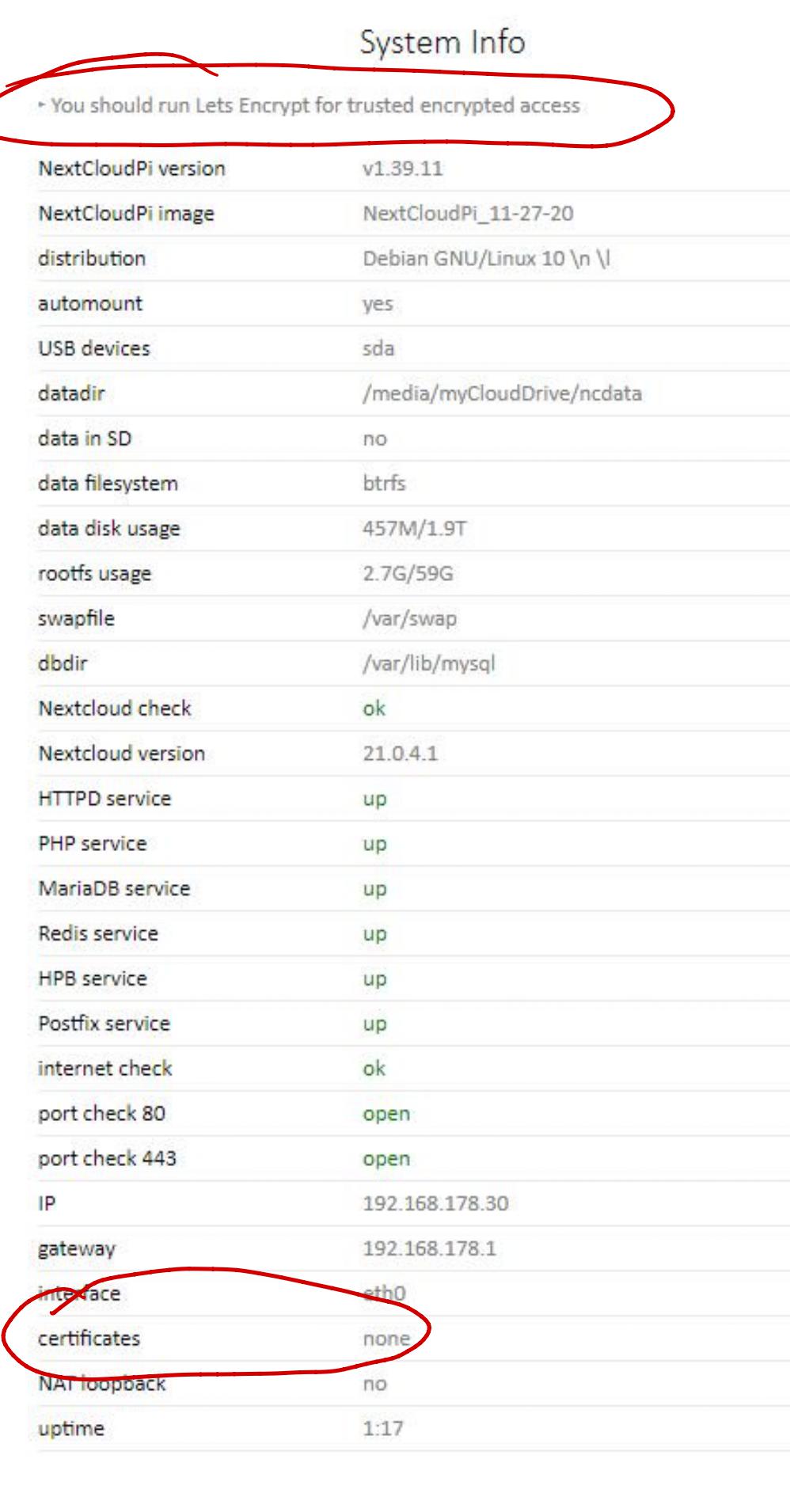
After NCP Update to 1.39.6 it was possible to Upgrade NC to 21.04.
Upgrade was succesfully but after reboot i can not access via internet domain, only lan access is possible with bypassing security hint.
Is this the first time you’ve seen this error? (Y/N):Y
Steps to replicate it:
- update NCP
- Upgrade NC
- access NC
The output of your Nextcloud log in Admin > Logging:
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"no app in context","method":"","url":"--","message":"Deprecated event type for \\OC\\Repair::info: Symfony\\Component\\EventDispatcher\\GenericEvent is used","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Repair::info: Repair info: JS cache cleared","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"no app in context","method":"","url":"--","message":"Deprecated event type for \\OC\\Repair::step: Symfony\\Component\\EventDispatcher\\GenericEvent is used","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Repair::step: Repair step: Clear every generated avatar on major updates","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"no app in context","method":"","url":"--","message":"Deprecated event type for \\OC\\Repair::step: Symfony\\Component\\EventDispatcher\\GenericEvent is used","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Repair::step: Repair step: Add preview background cleanup job","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"no app in context","method":"","url":"--","message":"Deprecated event type for \\OC\\Repair::step: Symfony\\Component\\EventDispatcher\\GenericEvent is used","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Repair::step: Repair step: Queue a one-time job to cleanup old backups of the updater","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"no app in context","method":"","url":"--","message":"Deprecated event type for \\OC\\Repair::step: Symfony\\Component\\EventDispatcher\\GenericEvent is used","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Repair::step: Repair step: Cleanup invalid photocache files for carddav","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"no app in context","method":"","url":"--","message":"Deprecated event type for \\OC\\Repair::step: Symfony\\Component\\EventDispatcher\\GenericEvent is used","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Repair::step: Repair step: Add background job to cleanup login flow v2 tokens","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"no app in context","method":"","url":"--","message":"Deprecated event type for \\OC\\Repair::step: Symfony\\Component\\EventDispatcher\\GenericEvent is used","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Repair::step: Repair step: Remove potentially over exposing share links","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"no app in context","method":"","url":"--","message":"Deprecated event type for \\OC\\Repair::info: Symfony\\Component\\EventDispatcher\\GenericEvent is used","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Repair::info: Repair info: No need to remove link shares.","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"no app in context","method":"","url":"--","message":"Deprecated event type for \\OC\\Repair::step: Symfony\\Component\\EventDispatcher\\GenericEvent is used","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Repair::step: Repair step: Clear access cache of projects","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"no app in context","method":"","url":"--","message":"Deprecated event type for \\OC\\Repair::step: Symfony\\Component\\EventDispatcher\\GenericEvent is used","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Repair::step: Repair step: Reset generated avatar flag","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"no app in context","method":"","url":"--","message":"Deprecated event type for \\OC\\Repair::step: Symfony\\Component\\EventDispatcher\\GenericEvent is used","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Repair::step: Repair step: Keep legacy encryption enabled","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"no app in context","method":"","url":"--","message":"Deprecated event type for \\OC\\Repair::step: Symfony\\Component\\EventDispatcher\\GenericEvent is used","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Repair::step: Repair step: Check encryption key format","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"no app in context","method":"","url":"--","message":"Deprecated event type for \\OC\\Repair::step: Symfony\\Component\\EventDispatcher\\GenericEvent is used","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Repair::step: Repair step: Remove old dashboard app config data","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"no app in context","method":"","url":"--","message":"Deprecated event type for \\OC\\Repair::step: Symfony\\Component\\EventDispatcher\\GenericEvent is used","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Repair::step: Repair step: Add job to cleanup the bruteforce entries","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"no app in context","method":"","url":"--","message":"Deprecated event type for \\OC\\Repair::step: Symfony\\Component\\EventDispatcher\\GenericEvent is used","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Repair::step: Repair step: Queue a one-time job to check for user uploaded certificates","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"no app in context","method":"","url":"--","message":"Deprecated event type for \\OC\\Repair::step: Symfony\\Component\\EventDispatcher\\GenericEvent is used","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Repair::step: Repair step: Repair DAV shares","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"no app in context","method":"","url":"--","message":"Deprecated event type for \\OC\\Repair::step: Symfony\\Component\\EventDispatcher\\GenericEvent is used","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Repair::step: Repair step: Add background job to set the lookup server share state for users","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:42+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Updater::startCheckCodeIntegrity: Starting code integrity check...","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:56+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Updater::finishedCheckCodeIntegrity: Finished code integrity check","userAgent":"--","version":"20.0.12.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:56+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Updater::updateEnd: Update successful","userAgent":"--","version":"21.0.4.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:56+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Updater::maintenanceDisabled: Turned off maintenance mode","userAgent":"--","version":"21.0.4.1"}
{"reqId":"BEOppt7lTzxCVrYZbOF8","level":1,"time":"2021-09-20T08:05:56+00:00","remoteAddr":"","user":"--","app":"updater","method":"","url":"--","message":"\\OC\\Updater::resetLogLevel: Reset log level to Warning(2)","userAgent":"--","version":"21.0.4.1"}
{"reqId":"YUhB@Gs6pXPFUMKHZRTsQQAAkwA","level":2,"time":"2021-09-20T08:10:36+00:00","remoteAddr":"192.168.178.32","user":"--","app":"no app in context","method":"POST","url":"/login","message":"Login failed: ncp (Remote IP: 192.168.178.32)","userAgent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:92.0) Gecko/20100101 Firefox/92.0","version":"21.0.4.1"}
{"reqId":"YUhCZ2s6pXPFUMKHZRTs3AAAkQk","level":2,"time":"2021-09-20T08:12:23+00:00","remoteAddr":"192.168.178.32","user":"ncp","app":"no app in context","method":"GET","url":"/settings/user/privacy","message":"Invalid privacyPolicyUrl data provided to provideInitialState by privacy","userAgent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:92.0) Gecko/20100101 Firefox/92.0","version":"21.0.4.1"}
The output of your config.php file in /path/to/nextcloud (make sure you remove any identifiable information!):
<?php
$CONFIG = array (
'passwordsalt' => 'x',
'secret' => 'x',
'trusted_domains' =>
array (
0 => 'localhost',
5 => 'nextcloudpi.local',
7 => 'nextcloudpi',
8 => 'nextcloudpi.lan',
11 => '95.90.x.x',
1 => '192.168.178.x',
3 => '3k9sldxx.myfritz.net',
22 => '3k9sldxx.myfritz.net',
),
'datadirectory' => '/mnt/hd1/nextcloud/data',
'dbtype' => 'mysql',
'version' => '21.0.4.1',
'overwrite.cli.url' => 'https://3k9sldxx.myfritz.net/',
'dbname' => 'nextcloud',
'dbhost' => 'localhost',
'dbport' => '',
'dbtableprefix' => 'oc_',
'mysql.utf8mb4' => true,
'dbuser' => 'ncadmin',
'dbpassword' => 'xx',
'installed' => true,
'instanceid' => 'oclaqn5ofxx',
'memcache.local' => '\\OC\\Memcache\\Redis',
'memcache.locking' => '\\OC\\Memcache\\Redis',
'redis' =>
array (
'host' => '/var/run/redis/redis.sock',
'port' => 0,
'timeout' => 0.0,
'password' => 'xx',
),
'tempdirectory' => '/mnt/hd1/nextcloud/data/tmp',
'mail_smtpmode' => 'sendmail',
'mail_smtpauthtype' => 'LOGIN',
'preview_max_x' => '2048',
'preview_max_y' => '2048',
'jpeg_quality' => '60',
'overwriteprotocol' => 'https',
'maintenance' => false,
'logfile' => '/mnt/hd1/nextcloud/data/nextcloud.log',
'htaccess.RewriteBase' => '/',
'theme' => '',
'loglevel' => '2',
'app_install_overwrite' =>
array (
0 => 'admin_notifications',
),
'simpleSignUpLink.shown' => false,
'log_type' => 'file',
'mail_sendmailmode' => 'smtp',
'mail_smtpsecure' => 'ssl',
'mail_smtpauth' => 1,
'mail_smtphost' => 'smtp-mail.outlook.com',
'mail_smtpport' => '587',
'mail_smtpname' => 'martin.xx',
'mail_smtppassword' => 'xx',
'trusted_proxies' =>
array (
11 => '127.0.0.1',
12 => '::1',
13 => '3k9sldxx.myfritz.net',
14 => '95.90.x.x',
),
);
The output of your Apache/nginx/system log in /var/log/____:
PASTE HERE
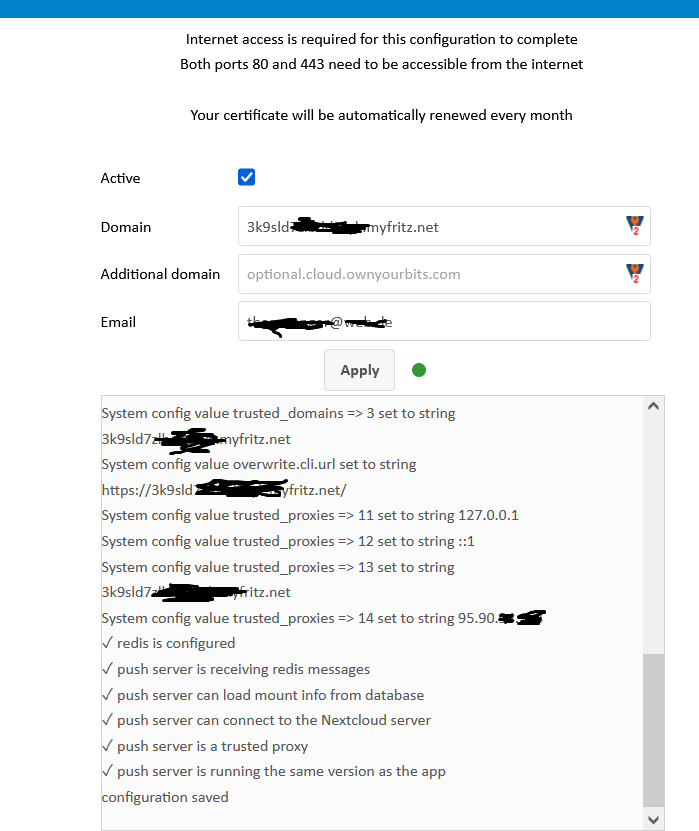
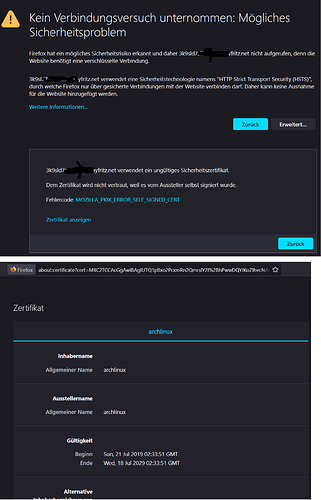
I tried to get a new lets encrpyt via NCP Menu, looks like this was successfully but browsers (even private sessions) shows the wrong cert