I have been trying to setup my Nextcloud behind the Traefik Reverse Proxy with Let’s Encrypt enabled. It worked fine with the nginx proxy of the LinuxServer/SWAG container.
At this point the Nextcloud site gives me a “404 page not found” message. I’ll share what I think are the relevant bits of my configuration.
docker-compose.yml
# Traefik
Traefik:
container_name: traefik
image: traefik:v2.2
restart: always
volumes:
- /var/run/docker.sock:/var/run/docker.sock
- ${APPDATA}/Traefik/traefik.toml:/traefik.toml
- ${APPDATA}/Traefik/traefik_dynamic.toml:/traefik_dynamic.toml
- ${APPDATA}/Traefik/acme.json:/acme.json
- ${APPDATA}/Traefik/traefik.log:/traefik.log
ports:
- 82:80
- 446:443
- 9999:9999
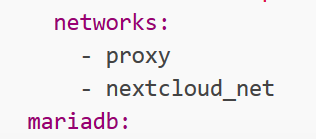
networks:
- web
# Nextcloud
nextcloud:
container_name: nextcloud
image: linuxserver/nextcloud
restart: always
environment:
- PUID=${PUID}
- PGID=${PGID}
- TZ=${TZ}
volumes:
- ${APPDATA}/Nextcloud:/config
- ${NEXTCLOUD}:/data
- ${DOWNLOADS}:/extern/downloads
- ${MEDIA}:/extern/mediabieb
- ${PERSOONLIJK}:/extern/persoonlijk
- ${UPLOADMAP}:/extern/uploadmap
- ${WATCHED}:/extern/watched
depends_on:
- mariadb
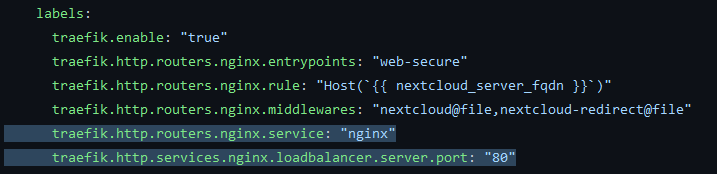
labels:
- "traefik.enable=true"
- "traefik.port=80"
- "traefik.docker.network=webproxy"
# Entrypoint and TLS
- "traefik.http.routers.cloud.entrypoints=websecure"
- "traefik.http.routers.cloud.rule=Host(`[REDACTED]`)"
- "traefik.http.routers.cloud.tls.certresolver=lets-encrypt"
# Middlewares:
- "traefik.http.routers.cloud.middlewares=cloud@docker,cloud-dav@docker"
# Middleware cloud adds additional headers:
- "traefik.http.middlewares.cloud.headers.customFrameOptionsValue=SAMEORIGIN"
- "traefik.http.middlewares.cloud.headers.framedeny=true"
- "traefik.http.middlewares.cloud.headers.sslredirect=true"
- "traefik.http.middlewares.cloud.headers.stsIncludeSubdomains=true"
- "traefik.http.middlewares.cloud.headers.stsPreload=true"
- "traefik.http.middlewares.cloud.headers.stsSeconds=15552000"
# Middleware cloud-dav replaces .well-known paths for caldav and carddav with proper nextcloud path
- "traefik.http.middlewares.cloud-dav.replacepathregex.regex=^/.well-known/ca(l|rd)dav"
- "traefik.http.middlewares.cloud-dav.replacepathregex.replacement=/remote.php/dav/"
networks:
- web
- internal
mariadb:
container_name: nextclouddb
image: linuxserver/mariadb
restart: always
environment:
- PUID=${PUID}
- PGID=${PGID}
- TZ=${TZ}
- MYSQL_ROOT_PASSWORD=${NCDBROOTPASS}
- MYSQL_DATABASE=${NCDBNAME}
- MYSQL_USER=${NCDBUSER}
- MYSQL_PASSWORD=${NCDBPASS}
volumes:
- ${APPDATA}/Nextclouddb:/config
networks:
- internal
networks:
web:
driver: bridge
external: true
internal:
external: false
traefik.toml
[log]
level = "ERROR"
filePath = "/traefik.log"
[api]
dashboard = true
[providers]
[providers.docker]
watch = true
network = "web"
exposedbydefault = false
[providers.file]
filename = "traefik_dynamic.toml"
[certificatesResolvers.lets-encrypt.acme]
email = "[REDACTED]"
storage = "acme.json"
[certificatesResolvers.lets-encrypt.acme.tlsChallenge]
[entryPoints]
[entryPoints.web]
address = ":80"
[entryPoints.web.http.redirections.entryPoint]
to = "websecure"
scheme = "https"
[entryPoints.websecure]
address = ":443"
traefik_dynamic.toml
[http.middlewares.simpleAuth.basicAuth]
users = [
"[REDACTED]"
]
[http.routers.api]
rule = "Host(`[REDACTED]`)"
entrypoints = ["websecure"]
middlewares = ["simpleAuth"]
service = "api@internal"
[http.routers.api.tls]
certResolver = "lets-encrypt"
[http.services]
[http.services.jellyfin-svc]
[[http.services.jellyfin-svc.loadBalancer.servers]]
url = "http://192.168.1.100:8096"
[tls.options]
[tls.options.default]
sniStrict = true
minVersion = "VersionTLS12"
curvePreferences = [
"secp521r1",
"secp384r1"
]
cipherSuites = [
"TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384",
"TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384",
"TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305",
"TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305",
"TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256",
"TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256",
"TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256",
"TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256"
]
[tls.options.mintls13]
minVersion = "VersionTLS13"
Nextcloud/nginx/nginx.conf
## Version 2018/08/16 - Changelog: https://github.com/linuxserver/docker-baseimage-alpine-nginx/commits/master/root/defaults/nginx.conf
user abc;
worker_processes 4;
pid /run/nginx.pid;
include /etc/nginx/modules/*.conf;
events {
worker_connections 768;
# multi_accept on;
}
http {
##
# Basic Settings
##
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 65;
types_hash_max_size 2048;
# server_tokens off;
# server_names_hash_bucket_size 64;
# server_name_in_redirect off;
client_max_body_size 0;
include /etc/nginx/mime.types;
default_type application/octet-stream;
##
# Logging Settings
##
access_log /config/log/nginx/access.log;
error_log /config/log/nginx/error.log;
##
# Gzip Settings
##
gzip on;
gzip_disable "msie6";
# gzip_vary on;
# gzip_proxied any;
# gzip_comp_level 6;
# gzip_buffers 16 8k;
# gzip_http_version 1.1;
# gzip_types text/plain text/css application/json application/x-javascript text/xml application/xml application/xml+rss text/javascript;
##
# nginx-naxsi config
##
# Uncomment it if you installed nginx-naxsi
##
#include /etc/nginx/naxsi_core.rules;
##
# nginx-passenger config
##
# Uncomment it if you installed nginx-passenger
##
#passenger_root /usr;
#passenger_ruby /usr/bin/ruby;
##
# Virtual Host Configs
##
include /etc/nginx/conf.d/*.conf;
include /config/nginx/site-confs/*;
}
#mail {
# # See sample authentication script at:
# # http://wiki.nginx.org/ImapAuthenticateWithApachePhpScript
#
# # auth_http localhost/auth.php;
# # pop3_capabilities "TOP" "USER";
# # imap_capabilities "IMAP4rev1" "UIDPLUS";
#
# server {
# listen localhost:110;
# protocol pop3;
# proxy on;
# }
#
# server {
# listen localhost:143;
# protocol imap;
# proxy on;
# }
#}
daemon off;
Two other relevant files I have edited along the way.
In this file I removed basically everything referencing 443:
Nextcloud/nginx/site-confs/default
server {
listen 80;
add_header X-Content-Type-Options nosniff;
add_header X-XSS-Protection "1; mode=block";
add_header X-Robots-Tag none;
add_header X-Download-Options noopen;
add_header X-Permitted-Cross-Domain-Policies none;
add_header Referrer-Policy no-referrer;
add_header Feature-Policy "geolocation 'self'";
root /var/www/html;
location = /robots.txt {
allow all;
log_not_found off;
access_log off;
}
}
Here I changed the trusted proxy from letsencrypt to traefik.
Just the relevant parts from: Nextcloud/www/nextcloud/config/config.php
'memcache.local' => '\\OC\\Memcache\\APCu',
'datadirectory' => '/data',
'instanceid' => '[REDACTED]',
'trusted_proxies' =>
array (
0 => 'traefik',
),
'overwrite.cli.url' => 'https://[REDACTED]',
'overwritehost' => '[REDACTED]',
'overwriteprotocol' => 'https',
'trusted_domains' =>
array (
0 => '[REDACTED]',
),
Please someone! Spot my mistake! @Reiner_Nippes seems to be an expert on this so I’ll just boldly tag you here (:
All the best,