Hi all,
The latest beta of the desktop client (2.7 beta 3), as well as upcoming test versions of the Android and iOS client, all support version 1.1 of our End-to-end Encryption protocol, part of v v1.5.2-beta1 of our new server-side E2E app.
This protocol fixes some serious issues, but is sadly not backwards compatible with the tech preview we had before. This means data has to be backed-up and migrated when you update!
Note you 2.7 beta 3 also brings further improvements to the new menu, and we’d love feedback on this feature!
The new beta is available on our installation page, bottom-right but of course I’ll happily post direct links:
Below instructions for testing.
Step 1: backup your data!
You will really have to backup all data you have in E2EE folders, or you will lose access. Don’t forget this!
Step 2: grab the new server release
Next you will need the server-side E2EE app version 1.5.2 for Nextcloud Hub v19 or 1.6.0 for the upcoming 20. We have published this as a test version and not released it into the app store, so you will have to grab and manually install it:
https://github.com/nextcloud/end_to_end_encryption/releases
Step 3. Cleanup.
As said, you will have to start from scratch, that is, backup your E2EE data, clean keys from client and server, and start fresh. Here is how, for clients and server:
Desktop
On the desktop client side, this is about removing every entry containing “e2e” from
its name in your keyring (can’t really tell more, its not the same keyring
management app if you’re using KDE, Gnome, Windows or Mac… people have to
know how their individual platforms handle passwords).
Example on Linux/KDE:
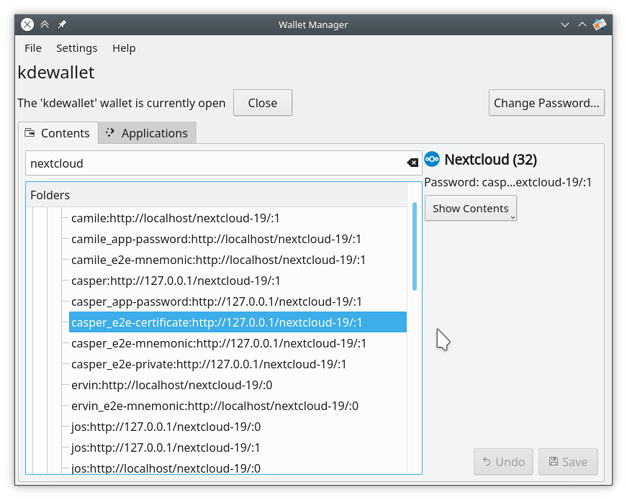
- Open KWalletManager
- Expand the Nextcloud folder
- Expand the Passwords subfolder
- Delete the _e2e-mnemonic entries
- Expand the Binary Data subfolder
- Delete the _e2e-private entries
- Delete the _e2e-certificate entries
It is possible to start fresh and delete all Nextcloud related keys from the key manager. Alternatively, just deleting the mnemnonic, e2e key and certificates would do. Here’s a screenshot of how those look on Linux/KDE/KWallet:
In KWallet, the right-click menu allows you to delete entries.
After that, you can install the new client from our installation page, bottom-right or the direct links below:
Mobile
For the Android client and iOS clients, for security reasons there is no way to manually reset the data. The user account has to be deleted and re-created on the client. To speed this process up, we recommend to use the QR code scan so you don’t have to enter any details on your phone.
How to do this:
- go to your user security settings
- create a new app password
- click “show QR code for mobile apps”
- scan the code from your mobile device while setting up the account
Note that a beta of the Android client that supports the new API is coming next week. The same goes for a Testflight version of the iOS client.
Server
Last but not least, you have to clean up the server configuration. This is also described in the release notes:
Step 1
To delete all active locks, execute the following command on the SQL server:
DELETE FROM oc_e2e_encryption_lock;
For MYSQL/Mariadb, this goes like this:
mysql -h hostname -u root -p
<--you might be able to get away with just `mysql` or `mysql -u root` depending on your setup-->
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 104
Server version: 10.4.13-MariaDB MariaDB package
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| Nextcloud |
| wordpressdatabase |
+--------------------+
5 rows in set (0.000 sec)
<--We have to find the right database and then 'USE' it-->
MariaDB [(none)]> USE Nextcloud
Database changed
<--Then we can delete all rows in the encryption lock table.-->
MariaDB [Nextcloud]> DELETE FROM oc_e2e_encryption_lock;
Query OK, 4 rows affected (0.002 sec)
MariaDB [Nextcloud]> quit
Bye
For SQLite, use sqlite3 owncloud.db in your data directory to open the sqlite command line, and then use DELETE FROM oc_e2e_encryption_lock; to delete the data from the table.
Step 2
To delete existing metadata files, existing public and private keys.
- Locate the data folder
- Open
appdata_{instanceId}/end_to_end_encryption - Delete
./meta-data,./public-keys,./private-keys. - Run
php occ files:scan-app-datain the Nextcloud folder.
Step 4
Now you’ve cleaned up and have fresh accounts. At this point, grab 2.7.0beta 3 for the desktop and/or, once released, the new mobile clients. You can now create a E2E folder and put files in it.
Tell us what you think
The desktop client team is looking forward to your feedback. Please, file issues in our github repo! The same goes for the Android and iOS issues you find. Finally, find the End-to-End encryption server repo here.
Careful!
As usual with E2EE and test releases: use with caution. That being said once properly setup, in our testing, things work quite smooth now. E2E is not very fast, but eventually will sync all data and we are currently prioritizing correctness over performance.
 Windows
Windows macOS
macOS Linux
Linux