Originally published at: Nextcloud Introducing Native Integrated End-to-end Encryption - Nextcloud
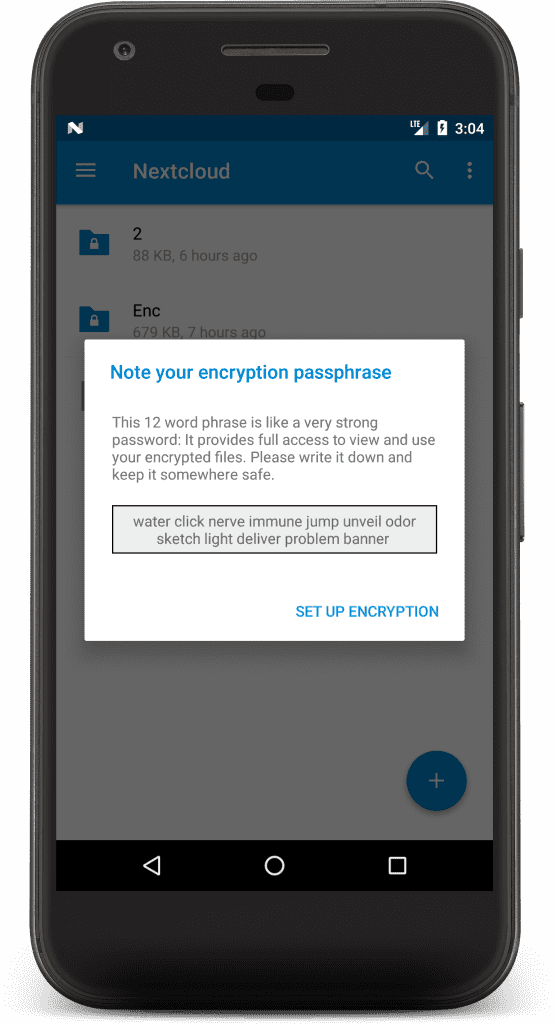
Android client encryption in action
We are excited to announce what is probably the all-time most requested feature in the 7-year history of our open source file sync and share work: End-to-end Encryption, also called Client Side Encryption. We designed it to work in a modern, real enterprise. Nextcloud End-to-end Encryption keeps the server from ever seeing the data while still facilitating syncing between devices and sharing with other users. It does not compromise security by using browser-based decryption, features secure key management so users don’t have to swap passwords, does not require re-encrypting large files to add or remove access privileges and it has important enterprise capabilities like an offline recovery key and Hardware Security Module (HSM) support. Rather than requiring users to create and manage (and never forget!) passwords, we use a device-generated passcode which can be recovered from any device the user owns or, of course, from a piece of paper.
Today we release a proof of concept with a working Android client and server-side key handling code as well as work-in-progress code for the desktop and iOS clients. We invite the wider security community to have a look at our design and implementation, provide feedback and help us fine-tune the design and code to provide the optimal balance between ease of use and protecting data. End-to-end encryption will be final as a feature of the upcoming Nextcloud 13.
What is different
End-to-end encryption with file sync and share right now it is a game of compromises. Web interfaces are either unavailable or security-compromised with browser-side decryption done with untrusted code coming from the server; or users have share a large, encrypted volume with each other that gets up and downloaded each time a change is made to authorization or files. Other solutions require users to simply share a password to enable sharing (without any way to manage and especially revoke user access rights) or rely on third-party tools which require re-encrypting and re-uploading files all the time.
Nextcloud is the first vendor to introduce an enterprise-grade, seamlessly integrated solution for end-to-end encryption in a file sync and share product.
The Nextcloud solution works on a per-folder level and features an easy to use, server-assisted but fully secure key management with Cryptographic Identity Protection, our method of securely signing and handling user certificates. Users can easily access their data on any of their devices using the clients and share with other users knowing their data can not be compromised by the server. The Nextcloud End-to-end Encryption design is unique in delivering on enterprise demands like a complete audit log, an optional offline administrator recovery key and support for a secure Hardware Security Module to be able to issue new identities to users.
Unique features
- Any number of folders can be end-to-end encrypted
- Users can easily add new devices using a code that consists of 12 dictionary words
- Sharing and revoking shares does not require users to create or enter passwords and has no need to re-encrypt (and re-upload) files.
- We rely exclusively on client-side encryption: no possibly compromised code that comes from the server (like in a browser) is trusted. The server never has access to unencrypted keys or unencrypted data.
- Enterprise solution designed to protect users from making mistakes with long, device-generated passcode and recovery capabilities
- The design supports a Hardware Security Module for enterprise environments which enables securely issuing new keys to users
- We support creating an off-line administrator recovery key which can be kept in a physically separated location like a safe. Users get warned when this key is enabled.
- Our design supports a complete audit log without compromising end-to-end security.
Use cases
Nextcloud End-to-end Encryption offers the ultimate protection for data, making it suitable for your most private information. Use it to protect a copy of your passport, passwords, driver’s license or bank account information.
For enterprises, the Nextcloud End-to-end Encryption feature provides a crucial expansion of their arsenal of security tools. For those who have to deal with sensitive user data in Europe, end-to-end encryption can help remedy the fact that the vast majority of cloud services is still not GDPR ready. Also important business data like financial statements or strategic plans can benefit from an extra layer of protection, keeping it from potential malicious actors or even compromised system administrators. Enterprises could require their employees to keep a subset of the most confidential information client side encrypted. Research, customer information or investor reports can be guaranteed to be kept strictly confidential.
The Cryptographic Identity Protection feature
Every user gets a unique public/private key combination upon first use of the end-to-end encryption. The public key is sent to the server and signed into a certificate. This is checked by the users’ other clients and used by other users to share encrypted files with the first user. Some interesting properties of the Cryptographic Identity Protection:
- Each device of the user can aid in recovering their private key. Only if a key is lost on all devices AND the 12 secure key words are lost off-line, the user loses access to his/her data. The optional offline administrator recovery key can still be used to re-gain access.
- By default, keys can’t change, so as to protect the identity of users from hacking when the server is compromised. If the key could change, a hacker could issue a ‘new’ certificate for the user and have clients respond by re-encrypting data with the new, compromised key.
- The process enables a complete audit log, crucial for enterprise use.
- The certificate can optionally be issued by a Hardware Security Module so it is possible to issue new certificates for existing users in a secure way.
We’ve set up a page on our website covering this feature as well!
Current state
We currently release a proof of concept, a first, preliminary implementation. Right now, we have the server component as well as a working Android app, with the desktop and iOS client coming soon. The server component users have to install requires the latest Nextcloud 12.0.3. We strongly recommend users to test this on a system of which they have a recent backup or with mock data. Newer versions of our solution might not be able to decrypt the data encrypted with the preview due to changes!
We publish this following the “release early, release often” rule of open source to get feedback on both the design and implementation. Security being as hard as it is, we expect some harsh criticism but we look forward to the constructive feedback which will enable us to improve and fine tune our design and implementation.
Design document
Our github repository contains the full design documentation needed for client developers to implement the Nextcloud End-to-end Encryption. It is currently in draft state, pending review from encryption professionals as well as anyone interested in giving their feedback!
Server
The server app can be found here, feedback and review is very much welcome! Note that testing requires Nextcloud 12.0.3. You will need to install it manually as we feel that putting it already in our app store might lure unsuspecting users in trying it out, with potentially bad results.
Android
Android users who want to test out the feature have to register here for our testing program (which gives access to our Beta clients) and then join this G+ community (the link is an invitation link) to get access to the alpha. Note that the end-to-end encryption requires at least Android 4.4 (KitKat), users with older versions will get a warning.
The android sourcecode can be found in this pull request. For the Android library the pull request is here.
The Android app has all as-of-yet non-working features disabled for encrypted folders but we still recommend to not use it on live data: newer versions might not be able to decrypt the data encrypted with the current release.
Desktop
The desktop client team is finalizing the code for the first preview, but help juggling OpenSSL code is certainly welcome! You can find the code in our client repository as the very first pull request.
iOS
The iOS app is also a work in progress, find the code in this branch. You can track and discuss development in this issue.