Nextcloud version (eg, 29.0.5): 30.0.0
Operating system and version (eg, Ubuntu 24.04): kubernetes 1.31
Apache or nginx version (eg, Apache 2.4.25): from latest docker image
PHP version (eg, 8.3): from latest docker image
The issue you are facing:
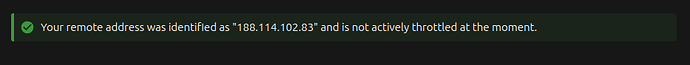
I only see Cloudflare’s IPs instead of my real IP in the logs and in the Admin/Security settings page, for example:
Is this the first time you’ve seen this error? (Y/N): Y
Steps to replicate it:
- Install Nextcloud behind Traefik
- Set Cloudflare to orange proxy the domain
The output of your Nextcloud log in Admin > Logging:
Clear
The output of your config.php file in /path/to/nextcloud (make sure you remove any identifiable information!):
<?php
$CONFIG = array (
'htaccess.RewriteBase' => '/',
'memcache.local' => '\\OC\\Memcache\\APCu',
'apps_paths' =>
array (
0 =>
array (
'path' => '/var/www/html/apps',
'url' => '/apps',
'writable' => false,
),
1 =>
array (
'path' => '/var/www/html/custom_apps',
'url' => '/custom_apps',
'writable' => true,
),
),
'memcache.distributed' => '\\OC\\Memcache\\Redis',
'memcache.locking' => '\\OC\\Memcache\\Redis',
'redis' =>
array (
'host' => 'redis-master.redis.svc.cluster.local',
'password' => 'password',
'port' => 6379,
),
'overwritehost' => 'nextcloud.domain.com',
'overwriteprotocol' => 'https',
'overwrite.cli.url' => 'https://nextcloud.domain.com',
'trusted_proxies' =>
array (
0 => '10.0.100.200',
1 => '173.245.48.0/20',
2 => '103.21.244.0/22',
3 => '103.22.200.0/22',
4 => '103.31.4.0/22',
5 => '141.101.64.0/18',
6 => '108.162.192.0/18',
7 => '190.93.240.0/20',
8 => '188.114.96.0/20',
9 => '197.234.240.0/22',
10 => '198.41.128.0/17',
11 => '162.158.0.0/15',
12 => '104.16.0.0/13',
13 => '104.24.0.0/14',
14 => '172.64.0.0/13',
15 => '131.0.72.0/22',
),
'forwarded_for_headers' =>
array (
0 => 'HTTP_CF_CONNECTING_IP',
1 => 'HTTP_X_FORWARDED_FOR',
),
'upgrade.disable-web' => true,
'passwordsalt' => '<<redacted by wwe>>',
'secret' => '<<redacted by wwe>>',
'trusted_domains' =>
array (
0 => 'localhost',
1 => 'domain.com',
),
'datadirectory' => '/var/www/html/data',
'dbtype' => 'mysql',
'version' => '30.0.0.14',
'dbname' => 'nextcloud',
'dbhost' => 'mariadb.mariadb.svc.cluster.local',
'dbport' => '',
'dbtableprefix' => 'oc_',
'mysql.utf8mb4' => true,
'dbuser' => 'nextcloud',
'dbpassword' => 'password',
'installed' => true,
'instanceid' => 'ocl33p15dt2n',
'mail_smtpmode' => 'smtp',
'mail_sendmailmode' => 'smtp',
'mail_from_address' => 'nextcloud',
'mail_domain' => 'domain.com',
'mail_smtpauth' => 1,
'mail_smtphost' => 'smtp.domain.com',
'mail_smtpport' => '465',
'mail_smtpname' => 'nextcloud@domain.com',
'mail_smtppassword' => 'password',
'mail_smtpsecure' => 'ssl',
'mail_smtpstreamoptions' =>
array (
'ssl' =>
array (
'allow_self_signed' => true,
'verify_peer' => false,
'verify_peer_name' => false,
),
),
'maintenance_window_start' => 1,
'maintenance' => false,
'logtimezone' => 'Europe/Rome',
'default_phone_region' => 'IT',
);
The output of your Apache/nginx/system log in /var/log/____:
PASTE HERE
Output errors in nextcloud.log in /var/www/ or as admin user in top right menu, filtering for errors. Use a pastebin service if necessary.
PASTE HERE