Nextcloud version (eg, 10.0.2): 11.0.2
Operating system and version (eg, Ubuntu 16.04): U 16.04.1
Apache or nginx version (eg, Apache 2.4.25): Apache 2.4.18
PHP version (eg, 5.6): 7.0.15
Is this the first time you’ve seen this error?: Yes
Can you reliably replicate it? (If so, please outline steps):
Yes, at any point by logging out and attempting to log in again.
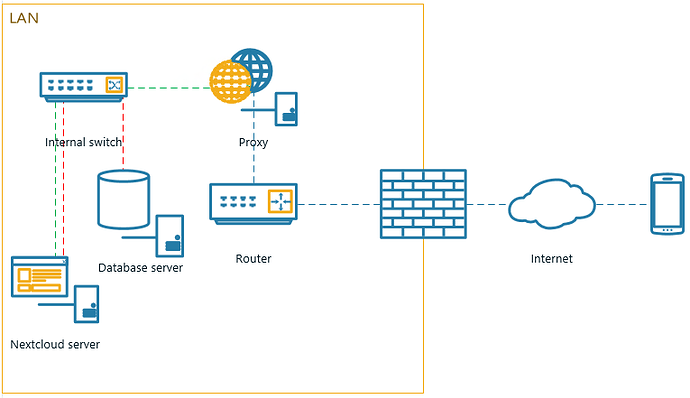
The issue you are facing:
I upgraded to 11.0.2 earlier, lovely upgrade, nothing went wrong and the logs are clean.
However, logging in from a logged out state takes upwards of 40 seconds. It is insanely slow.
Once logged in everything is fine, maybe not quite as snappy but no noticeable difference to 11.0.1.
Due to this delay, my mobile clients can’t login or upload to the server.
The output of your Nextcloud log in Admin > Logging:
Here’s what the mobile clients appear to be doing:
Info admin_audit Login successful: "jason" 2017-02-28T00:14:40+0000
Info admin_audit Login attempt: "jason" 2017-02-28T00:14:40+0000
Info admin_audit Logout occurred 2017-02-28T00:14:06+0000
Info admin_audit Login successful: "jason" 2017-02-28T00:13:12+0000
Info admin_audit Login attempt: "jason" 2017-02-28T00:13:12+0000
Info admin_audit Login successful: "jason" 2017-02-28T00:12:43+0000
Info admin_audit Login attempt: "jason" 2017-02-28T00:12:43+0000
Info admin_audit Login successful: "jason" 2017-02-28T00:09:38+0000
Info admin_audit Login attempt: "jason" 2017-02-28T00:09:38+0000
Info admin_audit Login successful: "jason" 2017-02-28T00:06:54+0000
Info admin_audit Login attempt: "jason" 2017-02-28T00:06:53+0000
Info admin_audit Login successful: "jason" 2017-02-28T00:06:51+0000
The output of your config.php file in /path/to/nextcloud (make sure you remove any identifiable information!):
N/A
The output of your Apache/nginx/system log in /var/log/____:
I’ve inspected both Apache and MariaDB logs for errors, absolutely clean as a whistle. Nothing to indicate an issue whatsoever.