Hello.
Thank you for your answers and even more, your questions.
I consider them very important.
I agree that pointing somewhat to the distro is indeed speculative. And maybe unrelated.
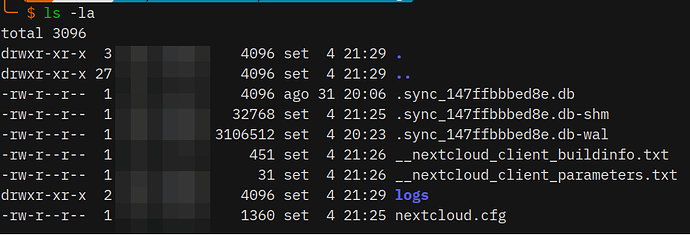
Yet I remember, that is from memory indeed, I hadn’t turned on the desktop for a while. Some weeks (?). I’ll get the proper information later on if I can. That is the actual dates of the previous logins.
I noticed, nevertheless, that when issuing the update commands that, not only it didn’t actually update all the packages that were previously installed by yay package manager, but that it took quite a while to finish that incomplete update.
The system, the desktop, that is, actually became unresponsive, several times during that incomplete update.
And yes this is still speculative, of course.
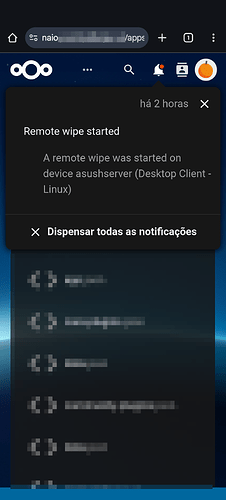
Also, and I am almost certain of this that I am stating right now, the remote wipe trigger (I’ll call it that way), happened, more or less, again from memory, during the time the system was having its updates, and having its hiccups, hangings, whatnot.
About your specific questions, I’ll be able to answer them soon, when sitting at a desk with an easier interface to gather the important information you were pointing at.
Yet:
0.1. The server, although, is an all-in-one NEXTCLOUD docker instance, deployed (migrated) to a proxmox vm, by myself, from a previous docker infrastructure running inside an Arch Linux, desktop+server, running at the same Intel NUC hardware that the proxmox server is running on presently.
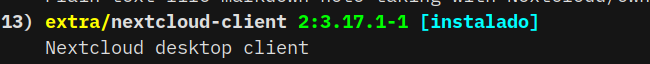
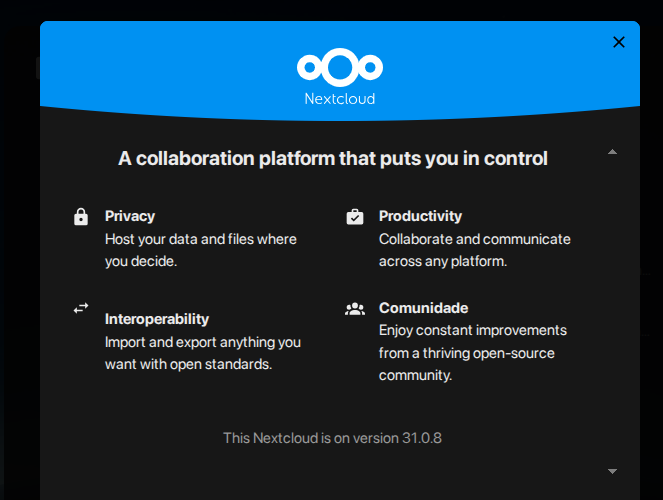
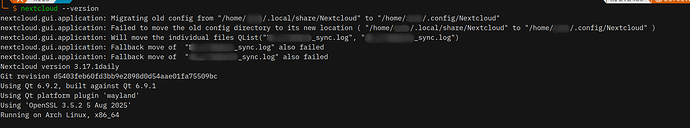
0.2. The nextcloud desktop version? (… Later on…)
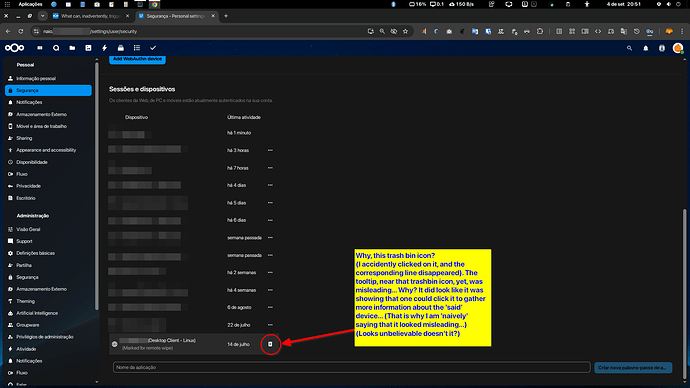
0.3. I am positive that I didn’t specify any policies about remote wiping any of the clients that currently connect to the server. Not ever. I was even surprised (the first time it happened) a while ago, that is, some weeks ago, on an Arch Linux laptop client, as well… Either those wiping policies were deployed by default, or, if I did actually change any of those rules, I must apologize for taking your time.
About this latest paragraph, if that would be the case, of myself having misconfigured the server to that devastating extent, I would suggest, if I may, that a more explicit warning would show up everytime that policy or rule would be engaged.
That is, if I had inadvertently configured such a drastic measure, I must say, I did not realize I was doing it.
Which brings me, for now, to my last thought:
Which is the default policy about this procedure?
Can you @vawaver please answer?
Thank you.
See you soon.