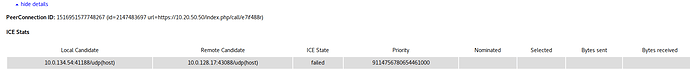
I have now setup a TURN server (coturn) which both clients connects to - I see this when running tcpdump - but it’s still completely black.
Where 10.20.50.50 is the Nextcloud and TURN server (port 3478 for TURN).
10.0.128.17 is client 1
10.0.134.49 is client 2
13:54:39.210367 IP 10.0.134.49.36562 > 10.20.50.50.https: Flags [P.], seq 671:1362, ack 728, win 340, options [nop,nop,TS val 1389793 ecr 252632], length 691
13:54:39.210376 IP 10.20.50.50.https > 10.0.134.49.36562: Flags [.], ack 1362, win 535, options [nop,nop,TS val 252644 ecr 1389793], length 0
13:54:39.214851 IP 10.20.50.50.https > 10.0.134.49.36563: Flags [.], ack 569, win 470, options [nop,nop,TS val 252646 ecr 1389790], length 0
13:54:39.245402 IP 10.0.134.49.36563 > 10.20.50.50.https: Flags [P.], seq 569:1262, ack 153, win 329, options [nop,nop,TS val 1389797 ecr 252646], length 693
13:54:39.245417 IP 10.20.50.50.https > 10.0.134.49.36563: Flags [.], ack 1262, win 491, options [nop,nop,TS val 252653 ecr 1389797], length 0
13:54:39.263858 IP 10.20.50.50.https > 10.0.134.49.36562: Flags [P.], seq 728:1455, ack 1362, win 535, options [nop,nop,TS val 252658 ecr 1389793], length 727
13:54:39.284196 IP 10.20.50.50.https > 10.0.134.49.36563: Flags [P.], seq 153:893, ack 1262, win 491, options [nop,nop,TS val 252663 ecr 1389797], length 740
13:54:39.327374 IP 10.0.134.49.36562 > 10.20.50.50.https: Flags [.], ack 1455, win 346, options [nop,nop,TS val 1389806 ecr 252658], length 0
13:54:39.340416 IP 10.0.134.49.36562 > 10.20.50.50.https: Flags [P.], seq 1362:2055, ack 1455, win 346, options [nop,nop,TS val 1389806 ecr 252658], length 693
13:54:39.340423 IP 10.20.50.50.https > 10.0.134.49.36562: Flags [.], ack 2055, win 556, options [nop,nop,TS val 252677 ecr 1389806], length 0
13:54:39.342317 IP 10.0.134.49.36563 > 10.20.50.50.https: Flags [.], ack 893, win 334, options [nop,nop,TS val 1389808 ecr 252663], length 0
13:54:39.368732 IP 10.20.50.50.https > 10.0.134.49.36562: Flags [P.], seq 1455:2194, ack 2055, win 556, options [nop,nop,TS val 252684 ecr 1389806], length 739
13:54:39.392474 IP 10.0.134.49.36562 > 10.20.50.50.https: Flags [.], ack 2194, win 351, options [nop,nop,TS val 1389812 ecr 252684], length 0
13:54:39.430476 IP 10.0.134.49.36562 > 10.20.50.50.https: Flags [P.], seq 2055:2748, ack 2194, win 351, options [nop,nop,TS val 1389815 ecr 252684], length 693
13:54:39.460639 IP 10.20.50.50.https > 10.0.128.17.45446: Flags [P.], seq 948199420:948200192, ack 2962451123, win 513, options [nop,nop,TS val 252707 ecr 3949126], length 772
13:54:39.461014 IP 10.20.50.50.https > 10.0.134.49.36562: Flags [P.], seq 2194:2933, ack 2748, win 578, options [nop,nop,TS val 252707 ecr 1389815], length 739
13:54:39.469021 IP 10.0.128.17.45446 > 10.20.50.50.https: Flags [.], ack 772, win 340, options [nop,nop,TS val 3949932 ecr 252707], length 0
13:54:39.469805 IP 10.0.128.17.45446 > 10.20.50.50.https: Flags [P.], seq 1:671, ack 772, win 340, options [nop,nop,TS val 3949932 ecr 252707], length 670
13:54:39.469812 IP 10.20.50.50.https > 10.0.128.17.45446: Flags [.], ack 671, win 534, options [nop,nop,TS val 252709 ecr 3949932], length 0
13:54:39.497622 IP 10.20.50.50.https > 10.0.128.17.45446: Flags [P.], seq 772:1544, ack 671, win 534, options [nop,nop,TS val 252716 ecr 3949932], length 772
13:54:39.505977 IP 10.0.134.49.36562 > 10.20.50.50.https: Flags [P.], seq 2748:3441, ack 2933, win 357, options [nop,nop,TS val 1389823 ecr 252707], length 693
13:54:39.509982 IP 10.0.128.17.45446 > 10.20.50.50.https: Flags [P.], seq 671:1341, ack 1544, win 346, options [nop,nop,TS val 3949936 ecr 252716], length 670
13:54:39.542848 IP 10.20.50.50.https > 10.0.134.49.36562: Flags [.], ack 3441, win 600, options [nop,nop,TS val 252728 ecr 1389823], length 0
13:54:39.546843 IP 10.20.50.50.https > 10.0.128.17.45446: Flags [.], ack 1341, win 555, options [nop,nop,TS val 252729 ecr 3949936], length 0
13:54:39.560425 IP 10.20.50.50.https > 10.0.134.49.36562: Flags [P.], seq 2933:3672, ack 3441, win 600, options [nop,nop,TS val 252732 ecr 1389823], length 739
13:54:39.561017 IP 10.20.50.50.https > 10.0.128.17.45446: Flags [P.], seq 1544:2316, ack 1341, win 555, options [nop,nop,TS val 252732 ecr 3949936], length 772
13:54:39.566375 IP 10.20.50.50.https > 10.0.134.49.36561: Flags [P.], seq 2828750114:2828750886, ack 2044698794, win 513, options [nop,nop,TS val 252733 ecr 1389125], length 772
13:54:39.591935 IP 10.0.134.49.36561 > 10.20.50.50.https: Flags [.], ack 772, win 340, options [nop,nop,TS val 1389832 ecr 252733], length 0
13:54:39.601381 IP 10.0.128.17.45446 > 10.20.50.50.https: Flags [.], ack 2316, win 352, options [nop,nop,TS val 3949946 ecr 252732], length 0
13:54:39.611038 IP 10.0.134.49.36561 > 10.20.50.50.https: Flags [P.], seq 1:665, ack 772, win 340, options [nop,nop,TS val 1389833 ecr 252733], length 664
13:54:39.611049 IP 10.20.50.50.https > 10.0.134.49.36561: Flags [.], ack 665, win 534, options [nop,nop,TS val 252745 ecr 1389833], length 0
13:54:39.616898 IP 10.0.134.49.36562 > 10.20.50.50.https: Flags [.], ack 3672, win 363, options [nop,nop,TS val 1389835 ecr 252732], length 0
13:54:39.639374 IP 10.20.50.50.https > 10.0.134.49.36561: Flags [P.], seq 772:1544, ack 665, win 534, options [nop,nop,TS val 252752 ecr 1389833], length 772
13:54:39.696070 IP 10.0.134.49.36561 > 10.20.50.50.https: Flags [P.], seq 665:1329, ack 1544, win 346, options [nop,nop,TS val 1389842 ecr 252752], length 664
13:54:39.723880 IP 10.20.50.50.https > 10.0.134.49.36561: Flags [P.], seq 1544:2316, ack 1329, win 555, options [nop,nop,TS val 252773 ecr 1389842], length 772
13:54:39.787042 IP 10.20.50.50.57588 > 10.20.56.10.domain: 62059+ PTR? 49.134.0.10.in-addr.arpa. (42)
13:54:39.787467 IP 10.20.56.10.domain > 10.20.50.50.57588: 62059 NXDomain* 0/1/0 (92)
13:54:39.792574 IP 10.0.134.49.36561 > 10.20.50.50.https: Flags [.], ack 2316, win 352, options [nop,nop,TS val 1389852 ecr 252773], length 0
13:54:40.790884 ARP, Request who-has 10.20.56.10 tell 10.20.50.50, length 28
13:54:40.791130 ARP, Reply 10.20.56.10 is-at 8a:16:8f:85:70:30 (oui Unknown), length 46
13:54:42.136808 IP 10.0.134.49.54590 > 10.20.50.50.3478: Flags [F.], seq 3415617292, ack 3490395854, win 324, options [nop,nop,TS val 1390086 ecr 242189], length 0
13:54:42.136945 IP 10.20.50.50.3478 > 10.0.134.49.54590: Flags [R.], seq 1, ack 1, win 453, options [nop,nop,TS val 253376 ecr 1390086], length 0
13:54:42.138770 IP 10.0.134.49.40905 > 10.20.50.50.3478: Flags [F.], seq 2316692247, ack 1825295247, win 324, options [nop,nop,TS val 1390086 ecr 242190], length 0
13:54:42.138843 IP 10.20.50.50.3478 > 10.0.134.49.40905: Flags [.], ack 1, win 453, options [nop,nop,TS val 253377 ecr 1390086], length 0
13:54:42.138978 IP 10.20.50.50.3478 > 10.0.134.49.40905: Flags [R.], seq 1, ack 1, win 453, options [nop,nop,TS val 253377 ecr 1390086], length 0
13:54:42.552963 IP 10.0.128.17.45446 > 10.20.50.50.https: Flags [P.], seq 1341:2040, ack 2316, win 352, options [nop,nop,TS val 3950240 ecr 252732], length 699
13:54:42.552982 IP 10.20.50.50.https > 10.0.128.17.45446: Flags [.], ack 2040, win 577, options [nop,nop,TS val 253480 ecr 3950240], length 0
13:54:42.581165 IP 10.20.50.50.https > 10.0.128.17.45446: Flags [P.], seq 2316:3055, ack 2040, win 577, options [nop,nop,TS val 253487 ecr 3950240], length 739
13:54:42.584711 IP 10.0.128.17.45446 > 10.20.50.50.https: Flags [.], ack 3055, win 358, options [nop,nop,TS val 3950244 ecr 253487], length 0
13:54:42.614428 IP 10.0.128.17.45446 > 10.20.50.50.https: Flags [P.], seq 2040:2739, ack 3055, win 358, options [nop,nop,TS val 3950247 ecr 253487], length 699
13:54:42.641788 IP 10.20.50.50.https > 10.0.128.17.45446: Flags [P.], seq 3055:3794, ack 2739, win 599, options [nop,nop,TS val 253502 ecr 3950247], length 739
13:54:42.662011 IP 10.0.128.17.45446 > 10.20.50.50.https: Flags [P.], seq 2739:3438, ack 3794, win 364, options [nop,nop,TS val 3950252 ecr 253502], length 699
13:54:42.688741 IP 10.20.50.50.https > 10.0.128.17.45446: Flags [P.], seq 3794:4533, ack 3438, win 621, options [nop,nop,TS val 253514 ecr 3950252], length 739
13:54:42.712279 IP 10.0.128.17.45446 > 10.20.50.50.https: Flags [P.], seq 3438:4137, ack 4533, win 370, options [nop,nop,TS val 3950257 ecr 253514], length 699
13:54:42.739952 IP 10.20.50.50.https > 10.0.128.17.45446: Flags [P.], seq 4533:5272, ack 4137, win 643, options [nop,nop,TS val 253527 ecr 3950257], length 739
13:54:42.782887 IP 10.0.128.17.45446 > 10.20.50.50.https: Flags [.], ack 5272, win 376, options [nop,nop,TS val 3950264 ecr 253527], length 0