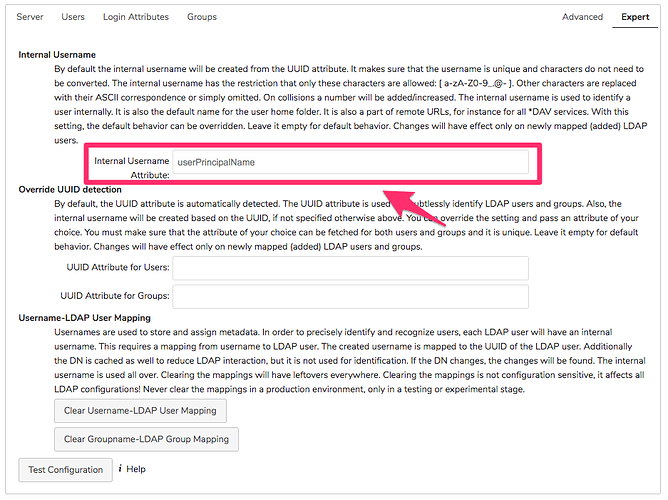
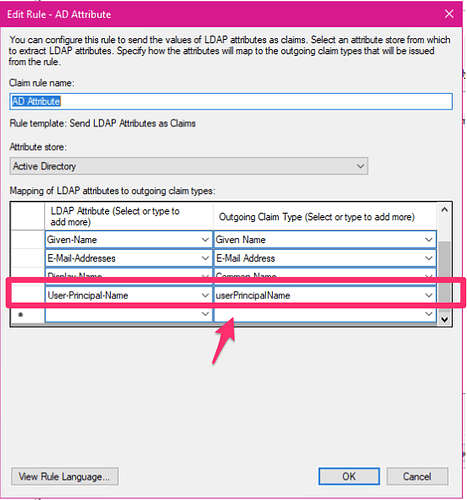
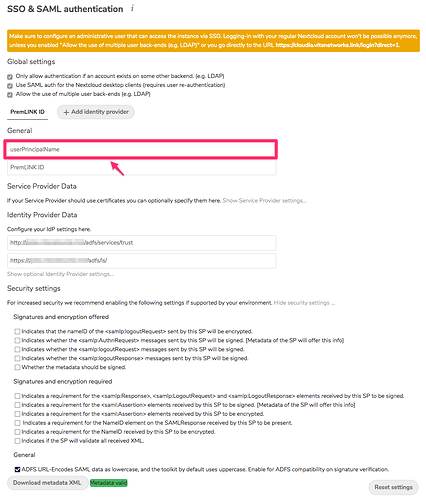
I do not have changes for the authentik side and I saw such errors in NC logging,
{“reqId”:“bvPuSB4j9bW59jl1r9xU”,“level”:4,“time”:“2023-07-20T23:06:28+00:00”,“remoteAddr”:“121.7.56.39”,“user”:“–”,“app”:“user_saml”,“method”:“POST”,“url”:“/apps/user_saml/saml/acs”,“message”:“Invalid SAML Response. Not match the saml-schema-protocol-2.0.xsd”,“userAgent”:“Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0”,“version”:“27.0.1.2”,“data”:{“app”:“user_saml”},“id”:“64b9be7f0d58d”}
{“reqId”:“bvPuSB4j9bW59jl1r9xU”,“level”:4,“time”:“2023-07-20T23:06:28+00:00”,“remoteAddr”:“121.7.56.39”,“user”:“–”,“app”:“user_saml”,“method”:“POST”,“url”:“/apps/user_saml/saml/acs”,“message”:“invalid_response”,“userAgent”:“Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0”,“version”:“27.0.1.2”,“data”:{“app”:“user_saml”},“id”:“64b9be7f0d5a5”}
{“reqId”:“bvPuSB4j9bW59jl1r9xU”,“level”:3,“time”:“2023-07-20T23:06:28+00:00”,“remoteAddr”:“121.7.56.39”,“user”:“–”,“app”:“PHP”,“method”:“POST”,“url”:“/apps/user_saml/saml/acs”,“message”:“DOMDocument::schemaValidate(): Invalid Schema at /var/www/html/custom_apps/user_saml/3rdparty/vendor/onelogin/php-saml/src/Saml2/Utils.php#153”,“userAgent”:“Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0”,“version”:“27.0.1.2”,“data”:{“app”:“PHP”},“id”:“64b9be7f0d5b4”}
{“reqId”:“EUvoyCCKojn9LV8X9zzi”,“level”:3,“time”:“2023-07-20T23:05:56+00:00”,“remoteAddr”:“121.7.56.39”,“user”:“admin”,“app”:“index”,“method”:“GET”,“url”:“/apps/user_saml/saml/metadata?idp=1”,“message”:“Invalid SP metadata: invalid_xml”,“userAgent”:“Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0”,“version”:“27.0.1.2”,“exception”:{“Exception”:“OneLogin\Saml2\Error”,“Message”:“Invalid SP metadata: invalid_xml”,“Code”:3,“Trace”:[{“file”:“/var/www/html/lib/private/AppFramework/Http/Dispatcher.php”,“line”:230,“function”:“getMetadata”,“class”:“OCA\User_SAML\Controller\SAMLController”,“type”:“->”,“args”:[1]},{“file”:“/var/www/html/lib/private/AppFramework/Http/Dispatcher.php”,“line”:137,“function”:“executeController”,“class”:“OC\AppFramework\Http\Dispatcher”,“type”:“->”,“args”:[[“OCA\User_SAML\Controller\SAMLController”],“getMetadata”]},{“file”:“/var/www/html/lib/private/AppFramework/App.php”,“line”:183,“function”:“dispatch”,“class”:“OC\AppFramework\Http\Dispatcher”,“type”:“->”,“args”:[[“OCA\User_SAML\Controller\SAMLController”],“getMetadata”]},{“file”:“/var/www/html/lib/private/Route/Router.php”,“line”:315,“function”:“main”,“class”:“OC\AppFramework\App”,“type”:“::”,“args”:[“OCA\User_SAML\Controller\SAMLController”,“getMetadata”,[“OC\AppFramework\DependencyInjection\DIContainer”],[“user_saml.SAML.getMetadata”]]},{“file”:“/var/www/html/lib/base.php”,“line”:1071,“function”:“match”,“class”:“OC\Route\Router”,“type”:“->”,“args”:[“/apps/user_saml/saml/metadata”]},{“file”:“/var/www/html/index.php”,“line”:36,“function”:“handleRequest”,“class”:“OC”,“type”:“::”,“args”:}],“File”:“/var/www/html/custom_apps/user_saml/lib/Controller/SAMLController.php”,“Line”:297,“CustomMessage”:“–”},“id”:“64b9be7f0d5ea”}
{“reqId”:“EUvoyCCKojn9LV8X9zzi”,“level”:3,“time”:“2023-07-20T23:05:56+00:00”,“remoteAddr”:“121.7.56.39”,“user”:“admin”,“app”:“PHP”,“method”:“GET”,“url”:“/apps/user_saml/saml/metadata?idp=1”,“message”:“DOMDocument::schemaValidate(): Invalid Schema at /var/www/html/custom_apps/user_saml/3rdparty/vendor/onelogin/php-saml/src/Saml2/Utils.php#153”,“userAgent”:“Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0”,“version”:“27.0.1.2”,“data”:{“app”:“PHP”},“id”:“64b9be7f0d5f8”}
{“reqId”:“EUvoyCCKojn9LV8X9zzi”,“level”:3,“time”:“2023-07-20T23:05:56+00:00”,“remoteAddr”:“121.7.56.39”,“user”:“admin”,“app”:“PHP”,“method”:“GET”,“url”:“/apps/user_saml/saml/metadata?idp=1”,“message”:“DOMDocument::schemaValidate(): Invalid Schema at /var/www/html/custom_apps/user_saml/3rdparty/vendor/onelogin/php-saml/src/Saml2/Utils.php#153”,“userAgent”:“Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0”,“version”:“27.0.1.2”,“data”:{“app”:“PHP”},“id”:“64b9be7f0d5f8”}
{“reqId”:“YKOfySZtVuOYdRbDq0DG”,“level”:3,“time”:“2023-07-20T23:05:47+00:00”,“remoteAddr”:“121.7.56.39”,“user”:“admin”,“app”:“index”,“method”:“GET”,“url”:“/apps/user_saml/saml/metadata?idp=1”,“message”:“Invalid SP metadata: invalid_xml”,“userAgent”:“Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0”,“version”:“27.0.1.2”,“exception”:{“Exception”:“OneLogin\Saml2\Error”,“Message”:“Invalid SP metadata: invalid_xml”,“Code”:3,“Trace”:[{“file”:“/var/www/html/lib/private/AppFramework/Http/Dispatcher.php”,“line”:230,“function”:“getMetadata”,“class”:“OCA\User_SAML\Controller\SAMLController”,“type”:“->”,“args”:[1]},{“file”:“/var/www/html/lib/private/AppFramework/Http/Dispatcher.php”,“line”:137,“function”:“executeController”,“class”:“OC\AppFramework\Http\Dispatcher”,“type”:“->”,“args”:[[“OCA\User_SAML\Controller\SAMLController”],“getMetadata”]},{“file”:“/var/www/html/lib/private/AppFramework/App.php”,“line”:183,“function”:“dispatch”,“class”:“OC\AppFramework\Http\Dispatcher”,“type”:“->”,“args”:[[“OCA\User_SAML\Controller\SAMLController”],“getMetadata”]},{“file”:“/var/www/html/lib/private/Route/Router.php”,“line”:315,“function”:“main”,“class”:“OC\AppFramework\App”,“type”:“::”,“args”:[“OCA\User_SAML\Controller\SAMLController”,“getMetadata”,[“OC\AppFramework\DependencyInjection\DIContainer”],[“user_saml.SAML.getMetadata”]]},{“file”:“/var/www/html/lib/base.php”,“line”:1071,“function”:“match”,“class”:“OC\Route\Router”,“type”:“->”,“args”:[“/apps/user_saml/saml/metadata”]},{“file”:“/var/www/html/index.php”,“line”:36,“function”:“handleRequest”,“class”:“OC”,“type”:“::”,“args”:}],“File”:“/var/www/html/custom_apps/user_saml/lib/Controller/SAMLController.php”,“Line”:297,“CustomMessage”:“–”},“id”:“64b9be7f0d62f”}
{“reqId”:“YKOfySZtVuOYdRbDq0DG”,“level”:3,“time”:“2023-07-20T23:05:47+00:00”,“remoteAddr”:“121.7.56.39”,“user”:“admin”,“app”:“PHP”,“method”:“GET”,“url”:“/apps/user_saml/saml/metadata?idp=1”,“message”:“DOMDocument::schemaValidate(): Invalid Schema at /var/www/html/custom_apps/user_saml/3rdparty/vendor/onelogin/php-saml/src/Saml2/Utils.php#153”,“userAgent”:“Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0”,“version”:“27.0.1.2”,“data”:{“app”:“PHP”},“id”:“64b9be7f0d63f”}