This tutorial shows how to install Nextcloud on Synology NAS running DMS 6. As I’m quite concerned about safety I try to make as safe as possible or at least being aware of how I could and what is the risk when I don’t do all of it.
Due to the move of the English Synology forum (Synology Forum
→ Wiki: How to setup Nextcloud with PHP7.0 and ngix (in progress).
This tutorial is not supposed to give an answer to everything neither is guaranteed that all information a fully accurate and reliable. As this is only a hobby of mine you cannot blame me if anything is wrong. I only try to share my experiences hoping to make the life of others easier who facing the same endeavour.
Feel free to give feedback on any of my statements, I’m happy to correct them.
1. Background
Probably there will be confidential data in your nextcloud you should secure wherever you can. By the time of the creation of this tutorial, I have only a simple ZyXEL NBG6616 Router and D-Link DGS-1008D 8-Port Gigabit Unmanaged Desktop switch. It is possible to install openWRT on the ZyXEL what gives me more some more additional features compared to stock firmware but first I want to get this done before I proceed to the next device. It is still on my agenda as firewall and guest wifi settings are a way more transparent in openWRT than in the stock firmware.
During my research, I came across several possibilities about how to secure my network from attacks from the inside and from the outside.
On the inside, there shall be mentioned VLAN and Radius Server but as long as the reset button is reachable by anyone in the flat, safety is limited.
On the outside, you split data and system of Nextcloud and expose as little as possible to the internet by means of firewall, proxy-server and creating dedicated user accounts for each service, what allows you to make use of Unix Domain Sockets instead of pure TCP socket based communication for data exchange between the different services on the server.
Keep in mind that in the end, only client-side encryption gives you a good level of privacy anything else makes it only harder to get there.
2. the results of my research
It isn’t little what I have learned so far but it is properly far from being complete. Nevertheless, I would like to share what I’ve learned so far allowing us to discuss security-related aspects of self-hosted Nextcloud hoping to end in a comprehensive hardening tutorial.
1. OSI and TCP/IP
First I tried to understand the architecture of the data transfer, what is described in the Transmission Control Protocol/Internet Protocol (TCP/IP), developed by the Department of Defense (DOD) to connect various devices to a common network (Internet). As well as in the OSI model, developed by ISO, the International Organization for Standardization.
The OSI is the newer protocol stack for networking. It contains a lot more layers and so more precisely defines the tasks performed by many TCP/IP layer protocols. So, if you want to develop a networking or telecommunication system, its specifications and description are more helpful to narrow down problems (Is it a physical issue or something with the application?), as well as computer programmers (when developing an application, which other layers does it need to work with?). Tech vendors selling new products will often refer to the OSI model to help customers understand which layer their products work with or whether it works “across the stack”.
With the rise of the internet, the TCP/IP stack become the de-facto standard of internet-based/related communication. Properly also supported by the fact that the TCP/IP model was focused on a smaller subset of protocols to support than OSI, the architecture is geared more specifically to its needs and its behaviours.
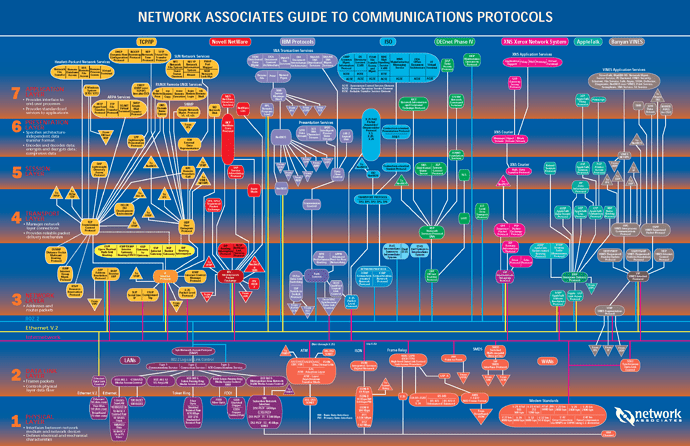
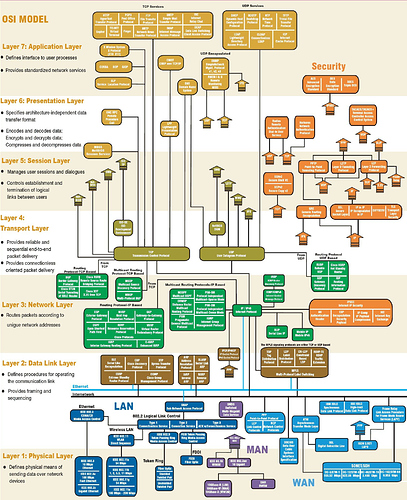
Before I continue you may have look on the following network protocols maps.
As I started my research, it made me feel that there are countless protocols ensuring that the data transfer works well at all layers of the stack understand each other, what made me feel lost.
These maps enlightened me a bit:
map one
map two
A lot of the mentioned protocols etc. are explained in Computer and network protocols; TCP / IP - OSI
Both are paradigms for discussing or describing how computers communicate with one another over a network but do not match exactly even for layers of the same name. Due to the clearness of the OSI and close relationship with TCP/IP some points in the following text are explained by expression related to OSI.
In order to avoid any confusion, when we talk about layer 2, layer 3 or layer 7 in which a network device works, we are referring to the OSI model, moreover, I will use the OSI layer names. This is reasoned that many devices or protocols, respectively act in a certain layer as defined by OSI only.
The main difference is that TCP/IP turns into usually known as the vertical technique and stands for Transmission Control Protocol/Internet Protocol. On the alternative hand, OSI Model was usually known as the flat technique whereby there are distinctive layers, as an illustration, introduction, session and utility layers. More about the difference can be found on Difference Between TCP/IP vs. OSI Model – Difference Wiki or TCP/IP Model Vs. OSI Model
Whereas OSI has distictiv layers for each function TCP/IP uses all-in-one protocols/services such as SMTP, DNS on the application layer, well explained on How Internet Work? With the OSI model and TCP/IP – Predict – Medium. Moreover you will find a good ilsuration on TCP/IP vs. OSI: What’s the Difference Between them?.
2. Ethernet
The TPC/IP protocol is based on Ethernet.
All begins that the protocol used for sending and receiving data is TCP/IP what in turn is build on ethernet. As I started my research, it made me feel that there are countless protocols ensuring that the data transfer works well at all layers of the
I started with at very bottom of the internet communication protocol
Since all techniques try to come around the natural risks of the MAC address in the Ethernet protocol, I’m going to take a trip to the basics first.
Besides the basic, you will find more information in my inquiry in the OpenWRT forum (Restrict access to a network having only an unmanaged switch).
Zusammenfassung
Dieser Text wird versteckt
[details=“1. configure network”]
That little bastard has the disadvantages that is yelling around his address what allows to be intercepted when being in the same net.
As you may wonder what the heck I’m talking about, let me explain