Nextcloud version: 28.0.1 AIO-Docker Image
Operating system and version: Ubuntu 22.04.3 LTS
Apache or nginx version: latest release as reverse proxy
PHP version (eg, 7.4): nextcloud-aio docker
The issue you are facing:
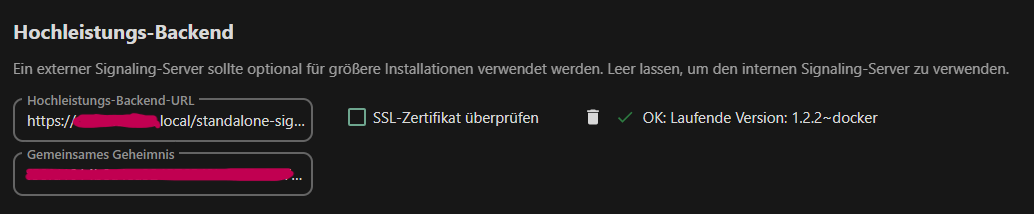
Hello everyone, unfortunately I got a certificate error with the HPB from Talk. The check mark for checking the certificate is disabled, but I still get this error message. I am using the env NEXTCLOUD_TRUSTED_CACERTS_DIR.
Collabora is working fine. I hope someone can help me! Thanks!
Is this the first time you’ve seen this error? (Y/N): yes
Steps to replicate it:
- Setup Nextcloud behind reverse proxy
- Certificate from company CA requested for cloud.company.local
What i have done:
- recreated nextcloud-aio-talk container
- checked firewall and network connectivity
- checked date/time on client, r-proxy, docker host, docker containers
The company Root-CA is a Windows Server 2019.
The output of aio-webinterface TALK log:
client.go:283: Client from 192.168.105.190 has RTT of 3 ms (3.513869ms)
capabilities.go:151: Capabilities expired for https://cloud.company.local/ocs/v2.php/cloud/capabilities, updating
capabilities.go:248: Could not get capabilities for https://cloud.company.local/ocs/v2.php/apps/spreed/api/v3/signaling/backend: Get "https://cloud.company.local/ocs/v2.php/cloud/capabilities": tls: failed to verify certificate: x509: certificate signed by unknown authority
The output of my browsers log:
Could not connect to server using backend url https://cloud.company.local/ocs/v2.php/apps/spreed/api/v3/signaling/backend {id: '1', type: 'error', error: {…}}error: {code: 'invalid_token', message: 'The passed token is invalid.'}code: "invalid_token"message: "The passed token is invalid."[[Prototype]]: Objectid: "1"type: "error"[[Prototype]]: Object
ao.Standalone.helloResponseReceived @ signaling.js:1081
(anonymous) @ signaling.js:777
my nextcloud startup command:
sudo docker run --init --sig-proxy=false --name nextcloud-aio-mastercontainer --restart always --publish 8080:8080 --env APACHE_PORT=11000 --env APACHE_IP_BINDING=0.0.0.0 --volume nextcloud_aio_mastercontainer:/mnt/docker-aio-config --volume /var/run/docker.sock:/var/run/docker.sock:ro --env SKIP_DOMAIN_VALIDATION=true --env NEXTCLOUD_TRUSTED_CACERTS_DIR=/home/ca-certs nextcloud/all-in-one:latest
my talk config:
curl output my client:
curl -vvv https://cloud.company.local:443/standalone-signaling/api/v1/welcome
* Trying 10.0.12.11:443... (this is reverse-proxy)
* Connected to cloud.company.local (10.0.12.11) port 443
* schannel: disabled automatic use of client certificate
* ALPN: curl offers http/1.1
* ALPN: server accepted http/1.1
* using HTTP/1.1
> GET /standalone-signaling/api/v1/welcome HTTP/1.1
> Host: cloud.company.local
> User-Agent: curl/8.4.0
> Accept: */*
>
* schannel: remote party requests renegotiation
* schannel: renegotiating SSL/TLS connection
* schannel: SSL/TLS connection renegotiated
* schannel: remote party requests renegotiation
* schannel: renegotiating SSL/TLS connection
* schannel: SSL/TLS connection renegotiated
< HTTP/1.1 200 OK
< Server: nginx/1.18.0 (Ubuntu)
< Date: Wed, 24 Jan 2024 06:04:51 GMT
< Content-Type: application/json; charset=utf-8
< Content-Length: 66
< Connection: keep-alive
< X-Spreed-Signaling-Features: audio-video-permissions, dialout, hello-v2, incall-all, mcu, simulcast, switchto, transient-data, update-sdp, welcome
< Alt-Svc: h3=":443"; ma=86400
<
{"nextcloud-spreed-signaling":"Welcome","version":"1.2.2~docker"}
* Connection #0 to host cloud.company.local left intact
curl output inside nextcloud container and same on docker host:
curl -vvv https://cloud.company.local:443/standalone-signaling/api/v1/welcome
* Host cloud.company.local:443 was resolved.
* IPv6: (none)
* IPv4: 10.0.12.11
* Trying 10.0.12.11:443...
* Connected to cloud.company.local (10.0.12.11) port 443
* ALPN: curl offers h2,http/1.1
* TLSv1.3 (OUT), TLS handshake, Client hello (1):
* CAfile: /etc/ssl/certs/ca-certificates.crt
* CApath: /etc/ssl/certs
* TLSv1.3 (IN), TLS handshake, Server hello (2):
* TLSv1.3 (IN), TLS handshake, Encrypted Extensions (8):
* TLSv1.3 (IN), TLS handshake, Certificate (11):
* TLSv1.3 (OUT), TLS alert, unknown CA (560):
* SSL certificate problem: unable to get local issuer certificate
* Closing connection
curl: (60) SSL certificate problem: unable to get local issuer certificate
More details here: https://curl.se/docs/sslcerts.html
curl failed to verify the legitimacy of the server and therefore could not
establish a secure connection to it. To learn more about this situation and
how to fix it, please visit the web page mentioned above.
reverse proxy config - created with the documentation:
map $http_upgrade $connection_upgrade {
default upgrade;
'' close;
}
server {
listen 10.0.12.11:443 ssl;
server_name cloud.company.local
http2 on;
add_header Alt-Svc 'h3=":443"; ma=86400';
location / {
proxy_pass http://10.0.12.9:11000$request_uri;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Port $server_port;
proxy_set_header X-Forwarded-Scheme $scheme;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header Accept-Encoding "";
proxy_set_header Host $host;
client_body_buffer_size 512k;
proxy_read_timeout 86400s;
client_max_body_size 0;
# Websocket
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection $connection_upgrade;
}
ssl_certificate /etc/ssl/intern_cloud.company.local_PUBLIC.crt;
ssl_certificate_key /etc/ssl/intern_cloud.company.local_PRIVATE.key;
ssl_session_timeout 1d;
ssl_session_cache shared:MozSSL:10m; # about 40000 sessions
ssl_session_tickets off;
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-CHACHA20-POLY1305;
ssl_prefer_server_ciphers on;
}