Hi Talk users & developers,
I’ve finally succeeded in installing the HPB on a separate machine. So far, everything looks fine: Janus, NATS and nextcloud-signaling services are running and listening to the right ports. coTURN is still installed on my NC machine and working fine as well. Ports are open and checking coTURN and the external signaling server via NC admin GUI in “Settings - Talk” returns OK.
So good so far.
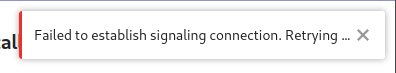
The problem is: everytime I want to start a call using the NC Talk GUI in my web browser (Firefox 84 or Chrome 87), NC returns a “Failed to establish signaling connection. Retrying…” and nothing happens.
Then when I use my mobile phone’s Talk app (latest version) it works pretty well (with some of the usual hiccups like poor stability and poor connectivity). But basically, it works and it works equally well in both my local network and in my mobile carriers network.
But why doesn’t Talk connect when I use it via NC Hub’s browser based GUI?
To give an overview, here’s what I’ve observed:
Desktop Windows Firefox via local network: Failed to establish signaling connection.
Desktop Windows Edge via local network: Failed to establish signaling connection.
Desktop Ubuntu Firefox via local network: Failed to establish signaling connection.
Desktop Windows Firefox via remote (mobile carrier) network: Failed to establish signaling connection.
Desktop Windows Edge via remote (mobile carrier) network: Failed to establish signaling connection.
Mobile Android App via local network: working
Mobile Android App via remote (mobile carrier) network: working
Mobile Webbrowser Firefox Android via local network: Failed to establish signaling connection.
Mobile Webbrowser Chrome Android via local network: Failed to establish signaling connection.
Mobile Webbrowser Firefox Android via remote (mobile carrier) network: Failed to establish signaling connection.
Mobile Webbrowser Chrome Android via remote (mobile carrier) network: Failed to establish signaling connection.
Logs do not look suspicious and there aren’t any error messages. It’s just the NC GUI which returns this “Failed to establish signaling connection” notification in Talk and then keeps waiting forever.
I use the latest versions of NC, Firefox, Edge, Chrome, Windows 10 and Ubuntu. Android version is 10.
The signaling server is setup on a 64-bit-ARM-Ubuntu machine using Janus 10.5 and the spreed standalone signaling server 0.2.0. NATS is also the latest version and is set up as a docker container.
Thanks in advance for your thoughts and hints!
Niklas