Nextcloud version (eg, 20.0.5): 28.0.2, AIO 7.13.1
Operating system and version (eg, Ubuntu 20.04): Docker 25.0.3 on AlmaLinux 9.3
The issue you are facing: We are planning on using Nextcloud in my organization as a place for our clients to access their account documents, and as a chat platform for people who don’t use our primary chat system. We want to be able to share their individual folders with them before they have logged into NC for the first time, and if I’m understanding the documentation correctly, this should be possible. We have NC’s login disabled, and are using an OAuth/OpenID Connect provider (user_oidc) to handle our authentication, which is working fine. All of our clients also have accounts in our OAuth system. I know OAuth doesn’t allow for retrieving a user listing, but our authentication system provides an LDAP server that can be used to query for any existing user. I have set this up using the LDAP/Active Directory integration, and NC is able to see and search the users.
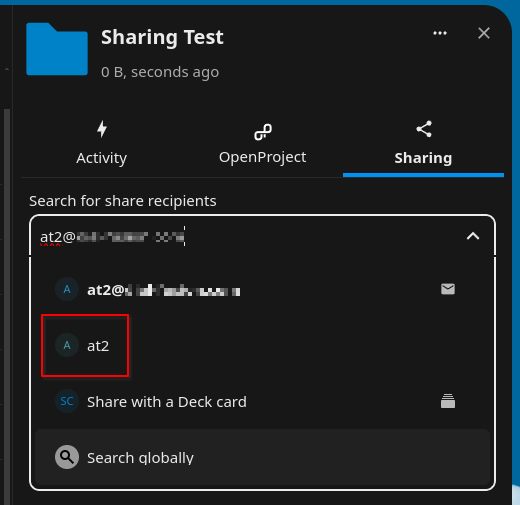
The issue appears when going to initiate a share to a user who has not yet signed into NC, so they don’t have an account entry in the Users screen. I am able to search for them using the standard Share interface, proving LDAP lookup is working correctly, but upon saving the share, I get an error
Is this the first time you’ve seen this error? (Y/N): Y
Steps to replicate it:
-
Visit the Files app
-
Click “Share” on a folder
-
Enter the full email address of the user I’m trying to share to (autocomplete is off for privacy reasons)
-
Select the “User” entry (the option that does not have the envelope next to it)
-
Click Save share
I then receive an error: Error creating the share: Sharing Sharing Test failed, could not find at2@xxx.xxx, maybe the server is currently unreachable or uses a self-signed certificate.
The output of your Nextcloud log in Admin > Logging:
{"reqId":"nwB7ZvZjykhvhMVz4ONe","level":2,"time":"2024-03-14T18:43:46+00:00","remoteAddr":"172.19.0.2","user":"admin","app":"no app in context","method":"POST","url":"/ocs/v2.php/apps/files_sharing/api/v1/shares","message":"error while discovering ocm provider","userAgent":"Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36","version":"28.0.2.5","exception":{"Exception":"GuzzleHttp\\Exception\\ClientException","Message":"Client error: `GET https://xxx.xxx/ocm-provider/` resulted in a `404 Not Found` response:\n\t\t<!DOCTYPE html>\r\n\t\t<html>\r\n\r\n\t\t<head>\r\n\t\t\t<meta charset=\"utf-8\">\r\n\t\t\t<title>XXXX</title>\r\n\t\t\t<meta name=\"viewpo (truncated...)\n","Code":404,"Trace":[{"file":"/var/www/html/3rdparty/guzzlehttp/guzzle/src/Middleware.php","line":69,"function":"create","class":"GuzzleHttp\\Exception\\RequestException","type":"::","args":["*** sensitive parameters replaced ***"]},{"file":"/var/www/html/3rdparty/guzzlehttp/promises/src/Promise.php","line":204,"function":"GuzzleHttp\\{closure}","class":"GuzzleHttp\\Middleware","type":"::","args":["*** sensitive parameters replaced ***"]},{"file":"/var/www/html/3rdparty/guzzlehttp/promises/src/Promise.php","line":153,"function":"callHandler","class":"GuzzleHttp\\Promise\\Promise","type":"::","args":[1,"*** sensitive parameters replaced ***","*** sensitive parameters replaced ***"]},{"file":"/var/www/html/3rdparty/guzzlehttp/promises/src/TaskQueue.php","line":48,"function":"GuzzleHttp\\Promise\\{closure}","class":"GuzzleHttp\\Promise\\Promise","type":"::","args":["*** sensitive parameters replaced ***"]},{"file":"/var/www/html/3rdparty/guzzlehttp/promises/src/Promise.php","line":248,"function":"run","class":"GuzzleHttp\\Promise\\TaskQueue","type":"->","args":[true]},{"file":"/var/www/html/3rdparty/guzzlehttp/promises/src/Promise.php","line":224,"function":"invokeWaitFn","class":"GuzzleHttp\\Promise\\Promise","type":"->","args":[]},{"file":"/var/www/html/3rdparty/guzzlehttp/promises/src/Promise.php","line":269,"function":"waitIfPending","class":"GuzzleHttp\\Promise\\Promise","type":"->","args":[]},{"file":"/var/www/html/3rdparty/guzzlehttp/promises/src/Promise.php","line":226,"function":"invokeWaitList","class":"GuzzleHttp\\Promise\\Promise","type":"->","args":[]},{"file":"/var/www/html/3rdparty/guzzlehttp/promises/src/Promise.php","line":62,"function":"waitIfPending","class":"GuzzleHttp\\Promise\\Promise","type":"->","args":[]},{"file":"/var/www/html/3rdparty/guzzlehttp/guzzle/src/Client.php","line":187,"function":"wait","class":"GuzzleHttp\\Promise\\Promise","type":"->","args":[]},{"file":"/var/www/html/lib/private/Http/Client/Client.php","line":230,"function":"request","class":"GuzzleHttp\\Client","type":"->","args":["get","https://xxx.xxx/ocm-provider/",[true,10,10,[true],["Nextcloud Server Crawler","gzip"],"And 1 more entries, set log level to debug to see all entries"]]},{"file":"/var/www/html/lib/private/OCM/OCMDiscoveryService.php","line":91,"function":"get","class":"OC\\Http\\Client\\Client","type":"->","args":["https://xxx.xxx/ocm-provider/",[10,true,10]]},{"file":"/var/www/html/lib/private/Federation/CloudFederationProviderManager.php","line":117,"function":"discover","class":"OC\\OCM\\OCMDiscoveryService","type":"->","args":["https://xxx.xxx"]},{"file":"/var/www/html/apps/federatedfilesharing/lib/Notifications.php","line":395,"function":"sendShare","class":"OC\\Federation\\CloudFederationProviderManager","type":"->","args":[["OC\\Federation\\CloudFederationShare"]]},{"file":"/var/www/html/apps/federatedfilesharing/lib/Notifications.php","line":320,"function":"tryOCMEndPoint","class":"OCA\\FederatedFileSharing\\Notifications","type":"->","args":["https://xxx.xxx",["at2","EHP6Xq60aL6YqOO","Sharing Test",13,"admin","And 5 more entries, set log level to debug to see all entries"],"share"]},{"file":"/var/www/html/apps/federatedfilesharing/lib/Notifications.php","line":90,"function":"tryHttpPostToShareEndpoint","class":"OCA\\FederatedFileSharing\\Notifications","type":"->","args":["https://xxx.xxx","*** sensitive parameters replaced ***",["at2","EHP6Xq60aL6YqOO","Sharing Test",13,"admin","And 5 more entries, set log level to debug to see all entries"]]},{"file":"/var/www/html/apps/federatedfilesharing/lib/FederatedShareProvider.php","line":238,"function":"sendRemoteShare","class":"OCA\\FederatedFileSharing\\Notifications","type":"->","args":["EHP6Xq60aL6YqOO","*** sensitive parameters replaced ***","Sharing Test",13,"admin","admin@https://cloud.xxx.xxx/","admin","admin@https://cloud.xxx.xxx/","*** sensitive parameters replaced ***"]},{"file":"/var/www/html/apps/federatedfilesharing/lib/FederatedShareProvider.php","line":191,"function":"createFederatedShare","class":"OCA\\FederatedFileSharing\\FederatedShareProvider","type":"->","args":["*** sensitive parameters replaced ***"]},{"file":"/var/www/html/lib/private/Share20/Manager.php","line":815,"function":"create","class":"OCA\\FederatedFileSharing\\FederatedShareProvider","type":"->","args":["*** sensitive parameters replaced ***"]},{"file":"/var/www/html/apps/files_sharing/lib/Controller/ShareAPIController.php","line":851,"function":"createShare","class":"OC\\Share20\\Manager","type":"->","args":["*** sensitive parameters replaced ***"]},{"file":"/var/www/html/lib/private/AppFramework/Http/Dispatcher.php","line":230,"function":"createShare","class":"OCA\\Files_Sharing\\Controller\\ShareAPIController","type":"->","args":["*** sensitive parameters replaced ***"]},{"file":"/var/www/html/lib/private/AppFramework/Http/Dispatcher.php","line":137,"function":"executeController","class":"OC\\AppFramework\\Http\\Dispatcher","type":"->","args":[["OCA\\Files_Sharing\\Controller\\ShareAPIController"],"createShare"]},{"file":"/var/www/html/lib/private/AppFramework/App.php","line":184,"function":"dispatch","class":"OC\\AppFramework\\Http\\Dispatcher","type":"->","args":[["OCA\\Files_Sharing\\Controller\\ShareAPIController"],"createShare"]},{"file":"/var/www/html/lib/private/Route/Router.php","line":315,"function":"main","class":"OC\\AppFramework\\App","type":"::","args":["OCA\\Files_Sharing\\Controller\\ShareAPIController","createShare",["OC\\AppFramework\\DependencyInjection\\DIContainer"],["ocs.files_sharing.ShareAPI.createShare"]]},{"file":"/var/www/html/ocs/v1.php","line":65,"function":"match","class":"OC\\Route\\Router","type":"->","args":["/ocsapp/apps/files_sharing/api/v1/shares"]},{"file":"/var/www/html/ocs/v2.php","line":23,"args":["/var/www/html/ocs/v1.php"],"function":"require_once"}],"File":"/var/www/html/3rdparty/guzzlehttp/guzzle/src/Exception/RequestException.php","Line":113,"message":"error while discovering ocm provider","exception":{},"remote":"https://xxx.xxx","CustomMessage":"error while discovering ocm provider"}}
{"reqId":"nwB7ZvZjykhvhMVz4ONe","level":3,"time":"2024-03-14T18:43:47+00:00","remoteAddr":"172.19.0.2","user":"admin","app":"no app in context","method":"POST","url":"/ocs/v2.php/apps/files_sharing/api/v1/shares","message":"Exception thrown: Exception","userAgent":"Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/122.0.0.0 Safari/537.36","version":"28.0.2.5","exception":{"Exception":"Exception","Message":"Sharing Sharing Test failed, could not find at2@xxx.xxx, maybe the server is currently unreachable or uses a self-signed certificate.","Code":0,"Trace":[{"file":"/var/www/html/apps/federatedfilesharing/lib/FederatedShareProvider.php","line":191,"function":"createFederatedShare","class":"OCA\\FederatedFileSharing\\FederatedShareProvider","type":"->","args":["*** sensitive parameters replaced ***"]},{"file":"/var/www/html/lib/private/Share20/Manager.php","line":815,"function":"create","class":"OCA\\FederatedFileSharing\\FederatedShareProvider","type":"->","args":["*** sensitive parameters replaced ***"]},{"file":"/var/www/html/apps/files_sharing/lib/Controller/ShareAPIController.php","line":851,"function":"createShare","class":"OC\\Share20\\Manager","type":"->","args":["*** sensitive parameters replaced ***"]},{"file":"/var/www/html/lib/private/AppFramework/Http/Dispatcher.php","line":230,"function":"createShare","class":"OCA\\Files_Sharing\\Controller\\ShareAPIController","type":"->","args":["*** sensitive parameters replaced ***"]},{"file":"/var/www/html/lib/private/AppFramework/Http/Dispatcher.php","line":137,"function":"executeController","class":"OC\\AppFramework\\Http\\Dispatcher","type":"->","args":[["OCA\\Files_Sharing\\Controller\\ShareAPIController"],"createShare"]},{"file":"/var/www/html/lib/private/AppFramework/App.php","line":184,"function":"dispatch","class":"OC\\AppFramework\\Http\\Dispatcher","type":"->","args":[["OCA\\Files_Sharing\\Controller\\ShareAPIController"],"createShare"]},{"file":"/var/www/html/lib/private/Route/Router.php","line":315,"function":"main","class":"OC\\AppFramework\\App","type":"::","args":["OCA\\Files_Sharing\\Controller\\ShareAPIController","createShare",["OC\\AppFramework\\DependencyInjection\\DIContainer"],["ocs.files_sharing.ShareAPI.createShare"]]},{"file":"/var/www/html/ocs/v1.php","line":65,"function":"match","class":"OC\\Route\\Router","type":"->","args":["/ocsapp/apps/files_sharing/api/v1/shares"]},{"file":"/var/www/html/ocs/v2.php","line":23,"args":["/var/www/html/ocs/v1.php"],"function":"require_once"}],"File":"/var/www/html/apps/federatedfilesharing/lib/FederatedShareProvider.php","Line":256,"CustomMessage":"Exception thrown: Exception"}}
The output of your config.php file in /path/to/nextcloud (make sure you remove any identifiable information!):
<?php
$CONFIG = array (
'one-click-instance' => true,
'one-click-instance.user-limit' => 100,
'memcache.local' => '\\OC\\Memcache\\APCu',
'apps_paths' =>
array (
0 =>
array (
'path' => '/var/www/html/apps',
'url' => '/apps',
'writable' => false,
),
1 =>
array (
'path' => '/var/www/html/custom_apps',
'url' => '/custom_apps',
'writable' => true,
),
),
'appsallowlist' =>
array (
),
'check_data_directory_permissions' => false,
'memcache.distributed' => '\\OC\\Memcache\\Redis',
'memcache.locking' => '\\OC\\Memcache\\Redis',
'redis' =>
array (
'host' => 'nextcloud-aio-redis',
'password' => '*** SANITIZED ***',
'port' => 6379,
),
'overwritehost' => 'cloud.xxx.xxx',
'overwriteprotocol' => 'https',
'passwordsalt' => '*** SANITIZED ***',
'secret' => '*** SANITIZED ***',
'trusted_domains' =>
array (
0 => 'localhost',
1 => 'cloud.xxx.xxx',
),
'datadirectory' => '/mnt/ncdata',
'skeletondirectory' => '',
'dbtype' => 'pgsql',
'version' => '28.0.2.5',
'overwrite.cli.url' => 'https://cloud.xxx.xxx/',
'dbname' => 'nextcloud_database',
'dbhost' => 'df-postgres',
'dbport' => '',
'dbtableprefix' => 'oc_',
'dbuser' => 'oc_nextcloud',
'dbpassword' => '*** SANITIZED ***',
'installed' => true,
'instanceid' => 'ockjdwjju13f',
'maintenance' => false,
'updatedirectory' => '/nc-updater',
'loglevel' => '2',
'app_install_overwrite' =>
array (
0 => 'nextcloud-aio',
1 => 'files_rightclick',
),
'log_type' => 'file',
'logfile' => '/var/www/html/data/nextcloud.log',
'log_rotate_size' => '10485760',
'log.condition' =>
array (
'apps' =>
array (
0 => 'admin_audit',
),
),
'preview_max_x' => '2048',
'preview_max_y' => '2048',
'jpeg_quality' => '60',
'enabledPreviewProviders' =>
array (
1 => 'OC\\Preview\\Image',
2 => 'OC\\Preview\\MarkDown',
3 => 'OC\\Preview\\MP3',
4 => 'OC\\Preview\\TXT',
5 => 'OC\\Preview\\OpenDocument',
6 => 'OC\\Preview\\Movie',
7 => 'OC\\Preview\\Krita',
0 => 'OC\\Preview\\Imaginary',
),
'enable_previews' => true,
'upgrade.disable-web' => true,
'mail_smtpmode' => 'smtp',
'trashbin_retention_obligation' => 'auto, 30',
'versions_retention_obligation' => 'auto, 30',
'activity_expire_days' => '30',
'simpleSignUpLink.shown' => false,
'share_folder' => '/Shared',
'one-click-instance.link' => 'https://nextcloud.com/all-in-one/',
'upgrade.cli-upgrade-link' => 'https://github.com/nextcloud/all-in-one/discussions/2726',
'allow_local_remote_servers' => true,
'davstorage.request_timeout' => 3600,
'htaccess.RewriteBase' => '/',
'dbpersistent' => false,
'files_external_allow_create_new_local' => false,
'trusted_proxies' =>
array (
0 => '127.0.0.1',
1 => '::1',
3 => '172.18.0.0/16',
),
'preview_imaginary_url' => 'http://nextcloud-aio-imaginary:9000',
'maintenance_window_start' => 7,
'default_phone_region' => 'US',
'mail_from_address' => 'nextcloud',
'mail_sendmailmode' => 'smtp',
'mail_domain' => 'xxx.xxx',
'mail_smtphost' => 'mail.xxx.xxx',
'mail_smtpport' => '465',
'mail_smtpauth' => 1,
'mail_smtpsecure' => 'ssl',
'mail_smtpname' => 'noreply@xxx.xxx',
'mail_smtppassword' => '*** SANITIZED ***',
'hide_login_form' => 'true',
'ldapProviderFactory' => 'OCA\\User_LDAP\\LDAPProviderFactory',
);