I encountered a similar situation to this with a company wanting Nextcloud. You will have to consider a couple things:
- which files do you want accessible over the Internet via Nextcloud?
- Are you keeping samba local only for security reasons, or because you have files you absolutely do not want on the Internet?
With point 1: you’ll want to have separate shares, one being internal only and the other external only, and share the external share with Nextcloud, and then you’ll have to create a clear policy within the company of what can/can’t go on the public server.
With point 2: If you just keep samba local-only for security and don’t care if all your docs are accessible via Nextcloud on the Internet, why not then just move everything to a Nextcloud server? But my impression is you don’t want all your docs to be on a public-facing server, so an option like I state with point 1 would be a wise approach.
If you split your files up into 2 shares (local-only & Internet access allowed), then you could (and should) have a separate server running Nextcloud, and access that share with the external storage app. One thing I faced though is changes made on the samba server without knowledge of Nextcloud means Nextcloud will not see those changes and assume the changes didn’t happen. There is a configuration you can add so Nextcloud regularly checks for non-Nextcloud changes, but it is supposedly experimental.
You more than likely don’t want to have duplicates of your files (recent vs. current) because that will just cause chaos and confusion among end users and you when you can’t tell which version you’re using.
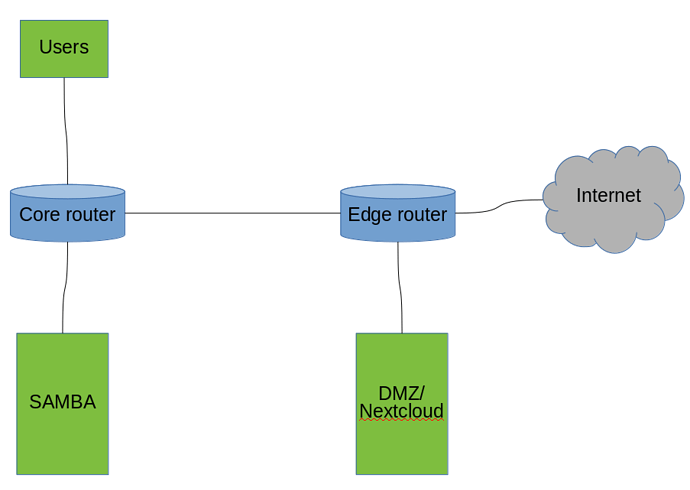
Like what @jakobssystems says, you will want to do some firewalling in this case for security, like this:
You could do some additional advanced security like VPN between the servers and the like, and then set up proper firewall rules to block unwanted communications (such as Internet cannot access samba or users, users can access samba, nextcloud can’t access users, etc.). I hope this gives you a good idea. Definitely keep in mind when you start exposing things to the internet you really want to take this security into consideration even more so. I have hundreds of SSH attempts on my server daily, and that’s just my personal server
Bonus: you could also set up your edge router or some other machine inside to be a VPN and say internal users and remote VPN users only can access Nextcloud, that way you don’t have Nextcloud web facing and people can still access files via a web interface and sync client by using the VPN to your network