Originally published at: https://nextcloud.com/blog/nitrokey-and-nextcloud-collaborate-on-securing-private-clouds/
Nitrokey develops fully open and auditable security USB keys for two-factor authentication, cryptographic key storage and much more. Their devices are developed and produced in Germany, primarily in Berlin. No overseas manufacturing is used to ensure quality and avoid hardware security breaches. The installed firmware can even be exported and verified, preventing attackers from inserting backdoors into products during shipping. Nitrokey has many other unique features, like hidden encrypted storage for plausible deniability at border checks. Learn about their offering on their website.
Self-hosting a Nextcloud gives users 100% control over their data, protecting their privacy. But privacy doesn’t exist without security and Nextcloud offers many security features like two-factor authentication (2FA), brute force protection, server and client side encryption and much more. Nitrokey’s security and encryption devices are a perfect match.
Second-Factor Keys
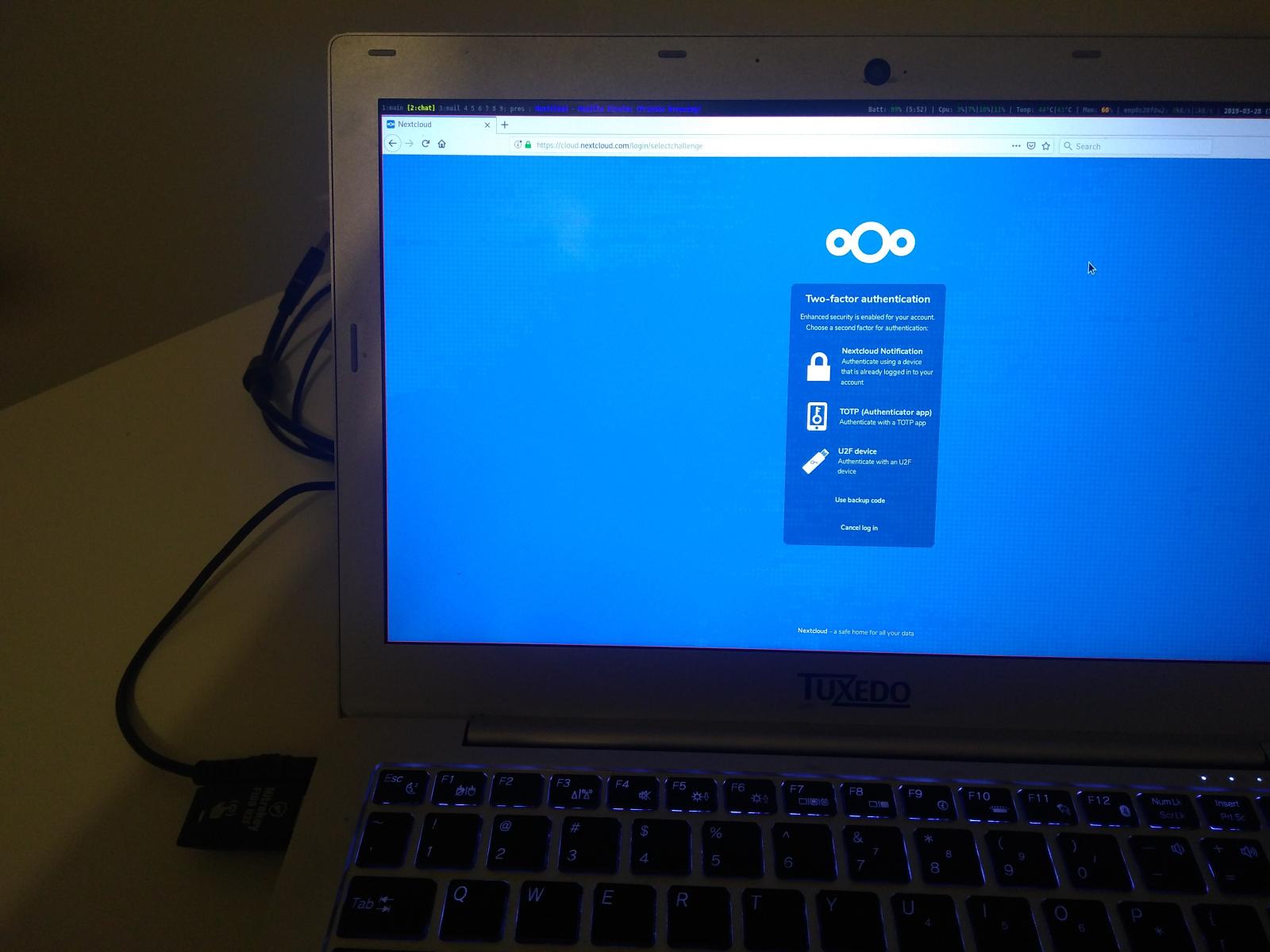
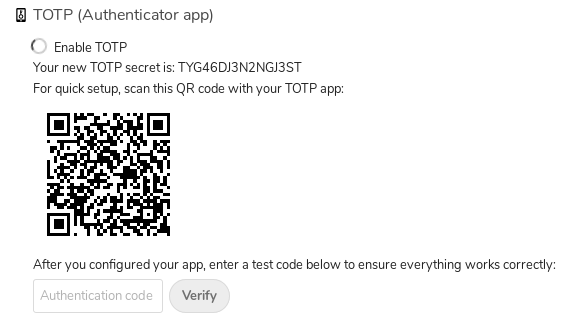
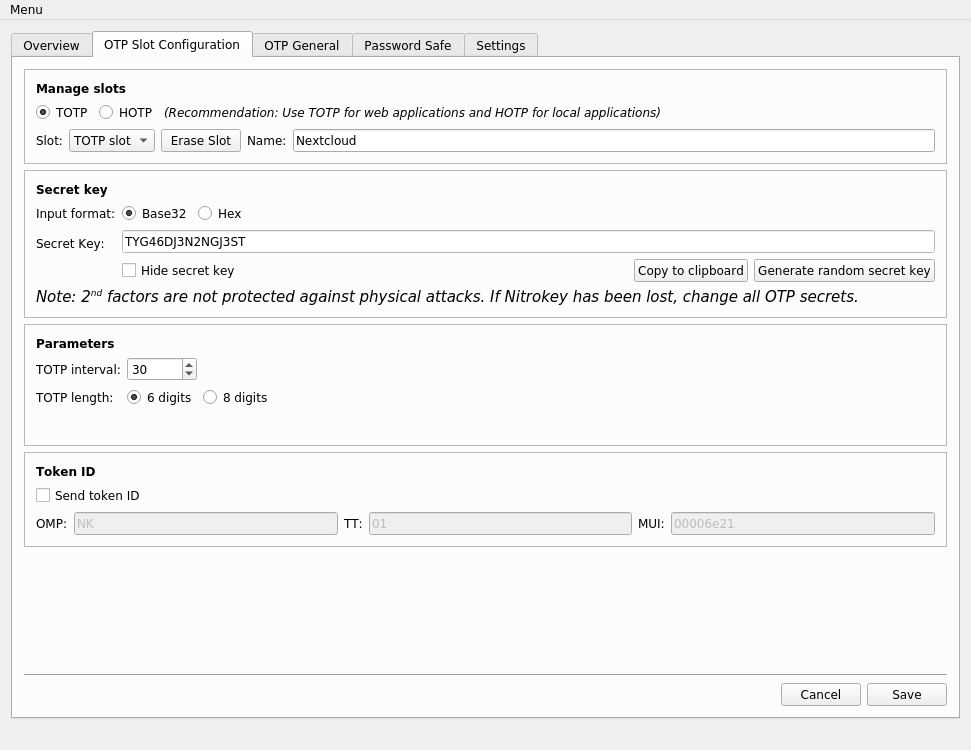
The Nitrokey Pro 2 and Nitrokey Storage 2 devices have been verified to work correctly with Nextcloud’s one-time passwords for secure two-factor authentication (2FA). This protects users’ accounts in the event of compromised passwords. Furthermore the USB keys feature a password manager, a cryptographic key store for email encryption and SSH administration. In addition the Nitrokey Storage 2 contains an encryption mass storage drive with the option of hidden volumes.
Password-Less Login Experience
FIDO2 authentication makes it possible to replace insecure and complicated password logins with secure and fast login experiences across websites and apps. FIDO2 uses the W3C’s Web Authentication specification (WebAuthn) and FIDO’s Client-to-Authenticator Protocol (CTAP2), which together let users use a device to easily authenticate to online services — in both mobile and desktop environments.
In simpler terms, to log in to your Nextcloud (or another webservice) you just insert your Nitrokey and click a button or two to approve the login.
Nitrokey and Nextcloud are both starting to work on FIDO2 support and have agreed to collaborate on this, making sure Nitrokeys can be used to seamlessly log in to Nextcloud systems. More news is likely to come during the Nextcloud Conference in Berlin later this year.
Enterprise key management
Nitrokey and Nextcloud will explore further collaboration, seeking ways to provide enterprises and private users with even better, more advanced security measures in the future. One of these areas are Nextcloud installations in enterprises providing end-to-end encryption and demanding a secure way to store cryptographic keys. This is where Nitrokey HSM can provide a central key store to securely store keys and at the same time enable the organization protected access to their keys. Here Nitrokey HSM’s m-of-n access scheme allows to define a group of authorized administrators and to protect the keys against a single malicious administrator. Also, encrypted key backups are essential in order to fulfill compliance and availability requirements.