I have Nextcloud setup with the Passwords app, I’m having troubles convincing Passwords its using HTTPS. What’s unusual is it works it specific scenarios and I have tried for hours many suggestions to adjust config files to get it working.
Current issues:
- Accessing from HTTP: as expected doesn’t work, no issue
- Accessing from HTTPS: external (internet) doesn’t work giving the HTTPS warning
- Accessing from HTTPS: internal network (still internet) it works
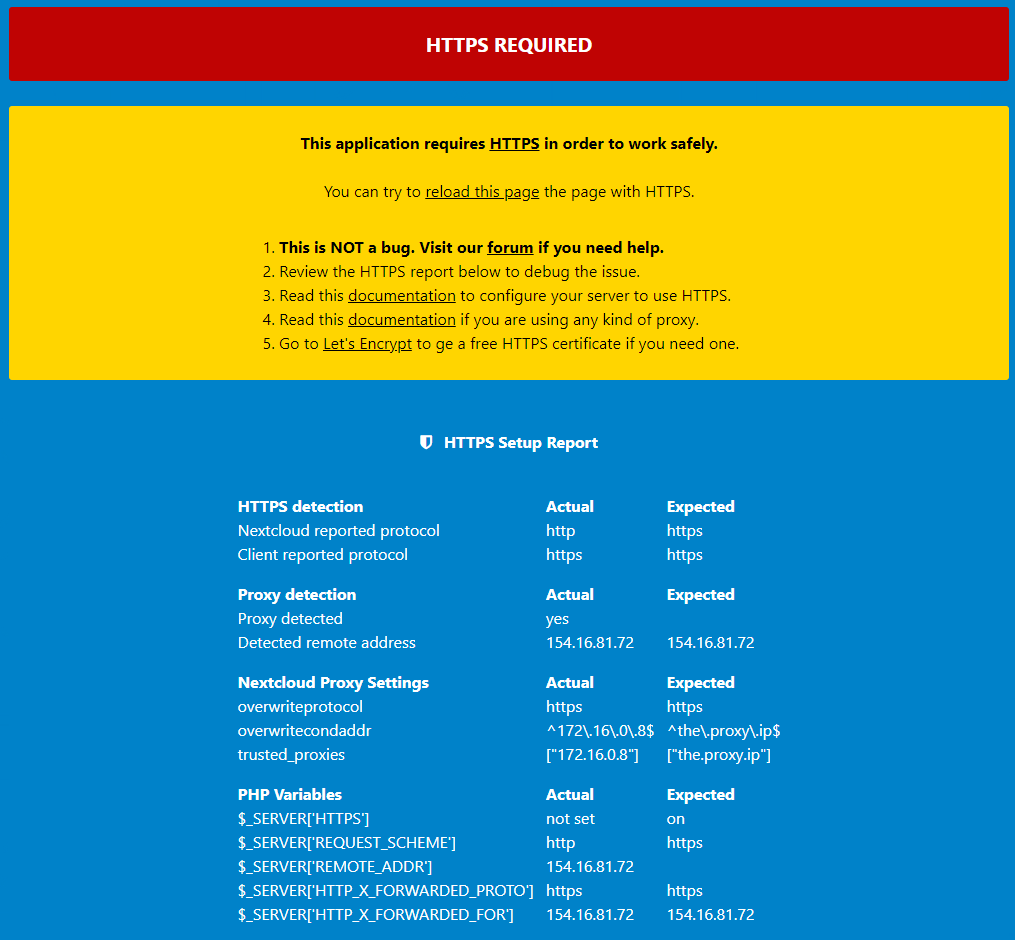
This is indicating to me reverse proxy issue but I have all the settings I think I require.
Below is the configuration settings I’m using, could I have some direction on what I’m doing wrong.
Nextcloud:
‘trusted_domains’ =>
array (
0 => ‘subdomain.domain’,
1 => ‘domain’,
2 => ‘NGINX IP’,
3 => ‘Nextcloud IP’,
),
‘trusted_proxies’ =>
array (
0 => ‘NGINX IP’,
),
‘overwriteprotocol’ => ‘https’,
‘overwritecondaddr’ => ‘NGINX IP’,
#‘overwritehost’ => ‘subdomain.domain’, <---- had this on and off and has no positive affect
#‘overwritewebroot’ => ‘/nextcloud’,
‘overwrite.cli.url’ => ‘Nextcloud IP’,
NGINX:
server {
set $forward_scheme http;
set $server “Nextcloud IP”;
set $port 80;
listen 8080;
#listen [::]:8080;
listen 4443 ssl http2;
#listen [::]:4443;
server_name subdomain.domain;
include conf.d/include/letsencrypt-acme-challenge.conf;
include conf.d/include/ssl-ciphers.conf;
ssl_certificate /etc/letsencrypt/live/npm-1/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/npm-1/privkey.pem;
include conf.d/include/block-exploits.conf;
include conf.d/include/force-ssl.conf;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection $http_connection;
proxy_http_version 1.1;
access_log /data/logs/proxy-host-7_access.log proxy;
error_log /data/logs/proxy-host-7_error.log warn;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto https;
proxy_set_header X-Forwarded-Port 443;
location / {
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection $http_connection;
proxy_http_version 1.1;
include conf.d/include/proxy.conf;
}
include /data/nginx/custom/server_proxy[.]conf;
}
