Hi Community,
new user, first serious question re security…
Got my Nextcloud instance set up as Docker container running in a VM, https access via Nginx Proxy Manager (NPM) within a subdomain of my main, let’s call it “mynextcloud.mypersonaldomain.com”. I set up 2FA and monitoring of login requests via fail2ban.
All working fine, however:
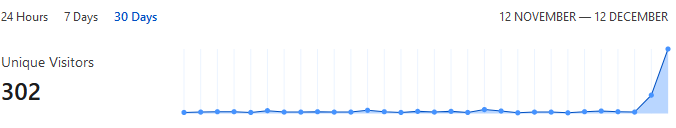
as soon as I set up my subdomain “mynextcloud” using a new CName entry, immediately, I got several intrusion attempts from various IPs.
I understand that my cloud instance can be accessed from the Internet and could therefore be targeted by criminal parties to get unauthorized access, but right away and using my personal, arbitrarily chosen subdomain ? Highly unlikely.
So I changed my subdomain from “mynextcloud.mypersonaldomain.com” to “nc.mypersonaldomain.com” and the same result - again right away several intrusion events, all caught by fail2ban.
I have several other subdomains running within NPM, and none of those have been attacked ever, so I don’t think that there are leaks within NPM, Let’sEncrypt or my DynDNS provider (where I’m registering the CNames).
The only possible leak I can think of is within NextCloud - maybe the new instances are being registered within NC, and this registration is being traced ? Honestly, I don’t have another explanation.
Can you please share your experiences and opinion from a security point of view. How is it possible that my NC instance using my private subdomain is immediately targeted by login requests ? Did I do something wrong ? Is there a central public NextCloud registry, storing all instances, which can be publicly accessed ?
Thank you for your support in this matter. I’m really worried - not because of intrusion attempts themselves, but because of the short timeframe between making my instance public and third parties trying to login.
SP
{"reqId":"GnONyakTw93Lfdu5sEHy","level":2,"time":"2023-11-30T17:20:49+00:00","remoteAddr":"2a01:6340:2:501::20","user":"--","app":"no app in context","method":"POST","url":"/login","message":"Login failed: sven99@devaza.id (Remote IP: 2a01:6340:2:501::20)","userAgent":"Mozilla/5.0 (Android 14; Mobile; rv:120.0) Gecko/120.0 Firefox/120.0","version":"27.1.4.1","data":[]}
{"reqId":"nP9leM7IVlbo9o2BbcdQ","level":2,"time":"2023-11-30T17:21:00+00:00","remoteAddr":"2a01:6340:2:501::20","user":"--","app":"no app in context","method":"POST","url":"/login","message":"Login failed: sven99@devaza.id (Remote IP: 2a01:6340:2:501::20)","userAgent":"Mozilla/5.0 (Android 14; Mobile; rv:120.0) Gecko/120.0 Firefox/120.0","version":"27.1.4.1","data":[]}
{"reqId":"hwqLZjqtzYeA3aJ0h3fw","level":2,"time":"2023-11-30T17:21:11+00:00","remoteAddr":"2a01:6340:2:501::20","user":"--","app":"no app in context","method":"POST","url":"/login","message":"Login failed: hugolehmann92@outlook.com (Remote IP: 2a01:6340:2:501::20)","userAgent":"Mozilla/5.0 (Android 14; Mobile; rv:120.0) Gecko/120.0 Firefox/120.0","version":"27.1.4.1","data":[]}
{"reqId":"J10JBzEXiEbHoLoTAOzt","level":2,"time":"2023-11-30T17:22:45+00:00","remoteAddr":"2a12:5940:13e2::2","user":"--","app":"no app in context","method":"POST","url":"/login","message":"Login failed: predovicalexandria138@gmail.com (Remote IP: 2a12:5940:13e2::2)","userAgent":"Mozilla/5.0 (Android 14; Mobile; rv:120.0) Gecko/120.0 Firefox/120.0","version":"27.1.4.1","data":[]}
{"reqId":"7xGaPRP0korP8kbcjB8Z","level":2,"time":"2023-11-30T17:22:55+00:00","remoteAddr":"2a12:5940:13e2::2","user":"--","app":"no app in context","method":"POST","url":"/login","message":"Login failed: predovicalexandria138@gmail.com (Remote IP: 2a12:5940:13e2::2)","userAgent":"Mozilla/5.0 (Android 14; Mobile; rv:120.0) Gecko/120.0 Firefox/120.0","version":"27.1.4.1","data":[]}
{"reqId":"0BG0nSH5pR7T4D9iDPJi","level":2,"time":"2023-11-30T17:23:08+00:00","remoteAddr":"2a12:5940:13e2::2","user":"--","app":"no app in context","method":"POST","url":"/login","message":"Login failed: sven99@devaza.id (Remote IP: 2a12:5940:13e2::2)","userAgent":"Mozilla/5.0 (Android 14; Mobile; rv:120.0) Gecko/120.0 Firefox/120.0","version":"27.1.4.1","data":[]}
{"reqId":"a8CzRh9NFzv68GQZVHyw","level":2,"time":"2023-11-30T17:24:46+00:00","remoteAddr":"2a04:52c0:129:c0c1::1","user":"--","app":"no app in context","method":"POST","url":"/login","message":"Login failed: predovicalexandria138@gmail.com (Remote IP: 2a04:52c0:129:c0c1::1)","userAgent":"Mozilla/5.0 (Android 14; Mobile; rv:120.0) Gecko/120.0 Firefox/120.0","version":"27.1.4.1","data":[]}
{"reqId":"sV7y0iFJX7cpuoDJr6Fc","level":2,"time":"2023-11-30T17:24:56+00:00","remoteAddr":"2a04:52c0:129:c0c1::1","user":"--","app":"no app in context","method":"POST","url":"/login","message":"Login failed: hugolehmann92@outlook.com (Remote IP: 2a04:52c0:129:c0c1::1)","userAgent":"Mozilla/5.0 (Android 14; Mobile; rv:120.0) Gecko/120.0 Firefox/120.0","version":"27.1.4.1","data":[]}
{"reqId":"uwIClVsy8WfxJRjJVrGb","level":2,"time":"2023-11-30T17:25:05+00:00","remoteAddr":"2a04:52c0:129:c0c1::1","user":"--","app":"no app in context","method":"POST","url":"/login","message":"Login failed: sven99@devaza.id (Remote IP: 2a04:52c0:129:c0c1::1)","userAgent":"Mozilla/5.0 (Android 14; Mobile; rv:120.0) Gecko/120.0 Firefox/120.0","version":"27.1.4.1","data":[]}
{"reqId":"zUMJQwaS0Mw265YIdzGf","level":2,"time":"2023-11-30T17:26:17+00:00","remoteAddr":"185.232.22.203","user":"--","app":"no app in context","method":"POST","url":"/login","message":"Login failed: anastacio.turcotte@devaza.id (Remote IP: 185.232.22.203)","userAgent":"Mozilla/5.0 (Android 14; Mobile; rv:120.0) Gecko/120.0 Firefox/120.0","version":"27.1.4.1","data":[]}
{"reqId":"TLr5FV2ZFiJ528iRhO8Y","level":2,"time":"2023-11-30T17:26:26+00:00","remoteAddr":"185.232.22.203","user":"--","app":"no app in context","method":"POST","url":"/login","message":"Login failed: anastacio.turcotte@devaza.id (Remote IP: 185.232.22.203)","userAgent":"Mozilla/5.0 (Android 14; Mobile; rv:120.0) Gecko/120.0 Firefox/120.0","version":"27.1.4.1","data":[]}
{"reqId":"OND54ps6wuFk6omO2nT4","level":2,"time":"2023-11-30T17:26:35+00:00","remoteAddr":"185.232.22.203","user":"--","app":"no app in context","method":"POST","url":"/login","message":"Login failed: hugolehmann92@outlook.com (Remote IP: 185.232.22.203)","userAgent":"Mozilla/5.0 (Android 14; Mobile; rv:120.0) Gecko/120.0 Firefox/120.0","version":"27.1.4.1","data":[]}