I’m glad that the guide has helped you. Much of it would not have been possible without wwe. wwe has also published a tutorial on Collabora, which I used in particular to configure Nextcloud. Have a look there if you have any questions about the last steps.
Of course I have also created and documented something for my Collabora. However, I haven’t yet found the time to add it to the existing concept of stacks here. The documentation is a bit more specialized because I really wanted to use Docker Secrets, so the stack uses a Dockerfile. However, it is otherwise as “easy” to use as the existing tutorial.
Zusammenfassung
The Collabora Stack: Creation of the required files
Setup a directory for our projekt:
DOCKER_PROJECT_DIR=/docker
mkdir -p ${DOCKER_PROJECT_DIR}/collabora
cd ${DOCKER_PROJECT_DIR}/collabora
.env
As in the previous stacks, the .env file is responsible for the basic configuration. Although the scope here is significantly smaller than in the other stacks.
vim ${DOCKER_PROJECT_DIR}/collabora/.env
.env
# project name is used as container name prefix (folder name if not set)
COMPOSE_PROJECT_NAME=collabora-prod
# this is the global ENV file for docker-compose
# collabora FQDN - public DNS
DOMAIN=office.example.com
DOCKER_LOGGING_MAX_SIZE=5m
DOCKER_LOGGING_MAX_FILE=3
collabora.env
collabora.env
aliasgroup1=${DOMAIN}:443
username_FILE=/run/secrets/collabora_user
password_FILE=/run/secrets/collabora_admin_password
extra_params="--o:ssl.enable=false --o:ssl.termination=true"
 By default Collabora Online enables the first WOPI host that tries to connect. You can define the allowed WOPI hosts by passing environment variables. The FQDN of the Nextcloud instance must be entered under variable aliasgroup1, e.g. for
By default Collabora Online enables the first WOPI host that tries to connect. You can define the allowed WOPI hosts by passing environment variables. The FQDN of the Nextcloud instance must be entered under variable aliasgroup1, e.g. for aliasgroup1=https://${DOMAIN}:443 the domain cloud.domain.tdl is entered. This ensures that the Collabora server can only be used by the Nextcloud instance.
Dockerfile
Unfortunately, the Collabora image does not support Docker secrets by default. I have helped myself by editing the Docker image with a Dockerfile. I add a function in the start-collabora-online.sh with sed, which translates all environment variables ending in _FILE into the corresponding environment variable. The script could be adapted so that only certain variables can be set in this way. Such as username or password. The anchor for the insertion is the line # Start coolwsd.
Dockerfile
FROM collabora/code:24.04.8.1.1
USER root
# link: https://github.com/CollaboraOnline/online/blob/master/docker/from-packages/scripts/start-collabora-online.sh
RUN sed -i 's/# Start coolwsd/# Function to read environment variables with _FILE suffix\nset_env_from_file() {\n for var in $(env | grep \x27_FILE=\x27); do\n var_name="${var%%_FILE=*}"\n file_path="${var#*=}"\n\n if [ -f "$file_path" ]; then\n export "$var_name"="$(cat "$file_path")"\n fi\n done\n}\n\n# Call the function to set environment variables from files\nset_env_from_file\n\n# Start coolwsd/g' /start-collabora-online.sh
RUN chmod 755 /start-collabora-online.sh
USER 100
The final script, that is added to start-collabora-online.sh:
# Function to read environment variables with _FILE suffix
set_env_from_file() {
for var in $(env | grep '_FILE='); do
# Extract the variable name without the _FILE suffix
var_name="${var%%_FILE=*}"
# Extract the file path
file_path="${var#*=}"
# Read the file content and export it as the environment variable
if [ -f "$file_path" ]; then
export "$var_name"="$(cat "$file_path")"
fi
done
}
# Call the function to set environment variables from files
set_env_from_file
# Start coolwsd
Collabora Stack (docker-compose.yml)
The Docker compose then looks like this:
docker-compose.yml
networks:
proxy:
external: true
secrets:
collabora_user:
file: ./secrets/collabora_user # put admin user in this file
collabora_admin_password:
file: ./secrets/collabora_admin_password # put admin password in this file
services:
collabora:
build:
context: .
restart: unless-stopped
cap_add:
- MKNOD
privileged: true
env_file:
- ./collabora.env
secrets:
- collabora_user
- collabora_admin_password
networks:
- default
- proxy
secrets
Thanks to the customizations using Dockerfile, we can use our usual concept of Docker Secrets. To do this, we create a corresponding folder and generate the password. We can then use the password for the Collabora administration area.
mkdir ${DOCKER_PROJECT_DIR}/colalbora/secrets
echo -n "admin" > ./secrets/collabora_user
tr -dc 'A-Za-z0-9#$%&+_' < /dev/urandom | head -c 32 | tee ./secrets/collabora_admin_password; echo
Customization of the Caddy Reverse Proxy
The reverse proxy still needs to be adapted so that our Collabora instance can be accessed via a subdomain.
We open the Caddyfile directly via: vim ${DOCKER_PROJECT_DIR}/proxy/Caddyfile and add a new section.
 The following also applies to this section: The subdomain should already point to your IP address of the reverse proxy or to the Docker host on which the reverse proxy is running via an A record!
The following also applies to this section: The subdomain should already point to your IP address of the reverse proxy or to the Docker host on which the reverse proxy is running via an A record!
docker-compose.yml
office.example.com {
header {
# Based on following source:
# https://raw.githubusercontent.com/nextcloud/docker/refs/heads/master/.examples/docker-compose/insecure/mariadb/fpm/web/nginx.conf
#
# HSTS settings
# WARNING: Only add the preload option once you read about
# the consequences in https://hstspreload.org/. This option
# will add the domain to a hardcoded list that is shipped
# in all major browsers and getting removed from this list
# could take several months.
# Strict-Transport-Security "max-age=15768000; includeSubDomains; preload;"
Strict-Transport-Security: "max-age=31536000; includeSubDomains;"
# HTTP response headers borrowed from Nextcloud `.htaccess`
Referrer-Policy no-referrer
X-Content-Type-Options nosniff
X-Download-Options noopen
X-Frame-Options SAMEORIGIN
X-Permitted-Cross-Domain-Policies none
X-Robots-Tag "noindex,nofollow"
X-XSS-Protection "1; mode=block"
Permissions-Policy "accelerometer=(), ambient-light-sensor=(), autoplay=(), battery=(), camera=(), cross-origin-isolated=(), display-capture=(), document-domain=(), encrypted-media=(), execution-while-not-rendered=(), execution-while-out-of-viewport=(), fullscreen=(), geolocation=(self), gyroscope=(), keyboard-map=(), magnetometer=(), microphone=(), midi=(), navigation-override=(), payment=(), picture-in-picture=(), publickey-credentials-get=(), screen-wake-lock=(), sync-xhr=(), usb=(), web-share=(), xr-spatial-tracking=()"
Content-Security-Policy upgrade-insecure-requests
}
# Source: https://caddy.community/t/help-with-getting-caddy-working-with-nextcloud-and-collabra/14543
@collabora {
path /browser/* # Browser is the client part of LibreOffice Online
path /hosting/discovery # WOPI discovery URL
path /hosting/capabilities # Show capabilities as json
}
reverse_proxy @collabora http://collabora:9980 {
header_up Host {host}
}
# download, presentation and image upload
@cool path_regexp ^/(c|l)ool/*
reverse_proxy @cool http://collabora:9980 {
header_up Host {host}
}
# main websocket
@websocket path_regexp ^/cool/(.*)/ws$
reverse_proxy @websocket http://collabora:9980 {
header_up Host {host}
header_up Upgrade {http.request.header.Upgrade}
header_up Connection "Upgrade"
transport http {
read_timeout 10h
}
}
# Admin Console websocket
@console path_regexp ^/cool/adminws$
reverse_proxy @console http://collabora:9980 {
header_up Host {host}
header_up Upgrade {http.request.header.Upgrade}
header_up Connection "Upgrade"
transport http {
read_timeout 10h
}
}
}
Launch the Collabora Stacks
First start of Collabora
Now is the time to start the stack: docker compose up -d
If the generation of the image does not work or you make adjustments to the Dockerfile, the following command can help to force the generation:
docker compose up -d --force-recreate --build
Testing the connection
A dial-in window should now open at the address https://office.example.com/browser/dist/admin/admin.html and it should be possible to dial in using admin and the password from ./secrets/collabora_admin_password.
Configuration of Nextcloud
After installation, the address of the Collabora server must be communicated to the Nextcloud Office app.
The compose file of the Nextcloud stack is used here, so either use -f to specify the path to the Nextcloud stack docker-compose.yaml or go to the directory of the Nextcloud stack.
-
Installation of the richdocuments app:
docker compose exec app php occ app:enable richdocuments
-
Cofiguration of the CODE server URL:
# docker compose
docker compose exec app php occ config:app:set richdocuments wopi_url --value office.example.com
docker compose exec app php occ richdocuments:activate-config
-
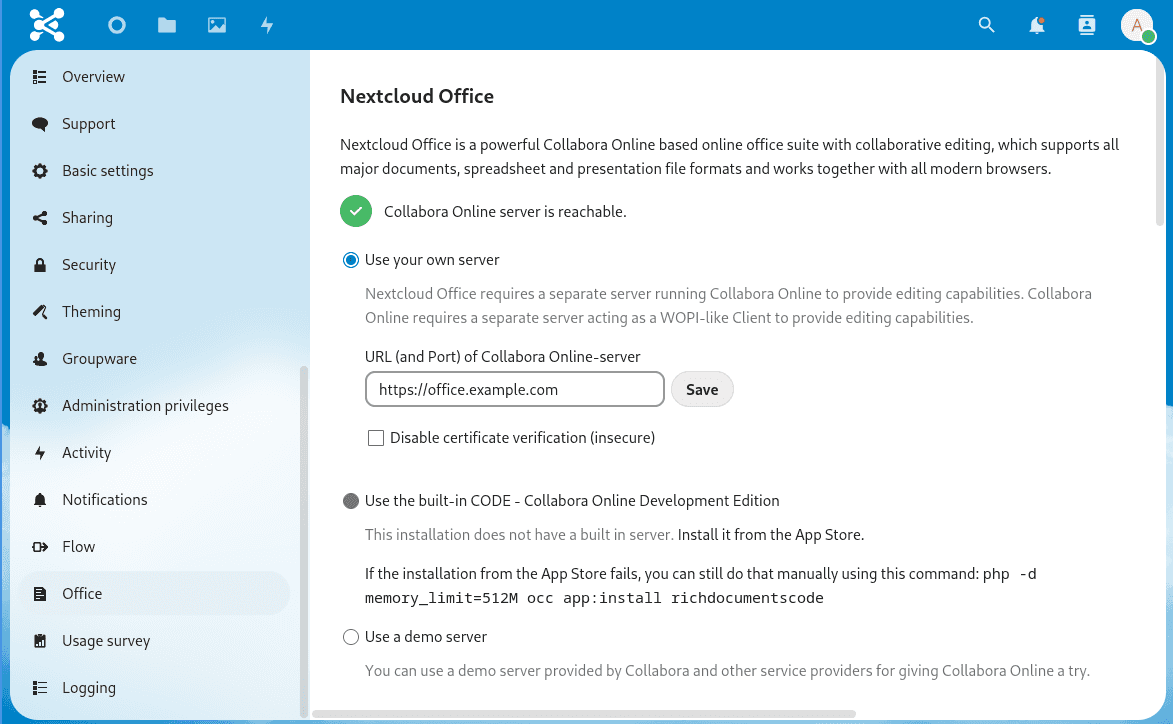
The last step must be implemented in the Nextcloud interface
- Go to the settings of your Nextcloud (user menu top right corner “ Administration settings)
- Select the Office menu item in the left-hand menu under Administration
- Select Use your own server and enter the address of your Collabora server (e.g. https://office.example.com)
- In addition, the Allow list for WOPI requests should be configured so that only the Collabora server can retrieve documents. This can be found further down below the advanced settings. The IPv4 and IPv6 address of the Collabora server must be entered here (e.g.
1.2.3.4,2a01:4f8:aaaa:bbbb:cccc::1).
- In this case, it is the IP-Address of the host, that serves the reverse proxy. If you think of the picture at the beginning of the tutorial, the host of
/docker/proxy:
In my case 192.168.77.1
 The IP address of the Collabora host should be the IP address of the Docker container that it has in the
The IP address of the Collabora host should be the IP address of the Docker container that it has in the collabora network. You remember? The Collabora and Nextcloud stacks are connected via the proxy network.
 A separate Collabora server has been installed and set up in a Nextcloud. When opening documents in the Nextcloud web interface, Collabora is now automatically loaded so that the document can be edited.
A separate Collabora server has been installed and set up in a Nextcloud. When opening documents in the Nextcloud web interface, Collabora is now automatically loaded so that the document can be edited.