(I have experience with OAuth2 (a/b), this is a somewhat advanced question.)
In my quest to authenticate more things against my nextcloud, I would like to combine it with a Traefik middleware: ForwardAuth.
I am not entirely sure that this can work out of the box, I certainly couldn’t get it working in a few hours of trying. I have already consulted examples that use ForwardAuth+Google and ForwardAuth+Authelia, but I couldn’t put all the pieces together, apparently.
What’s working:
- my nextcloud, including other services that authenticate against it successfully
- my traefik, including tls certificates, routes and services
- the middleware in my traefik, redirecting me towards nextcloud
What isn’t working:
I am not sure how, after allowing authentication on the nextcloud page, this should continue, which way the traefik proxy would be notified of the authentication result. Currently, I am stuck in an endless loop on my nextcloud page.
What I tried:
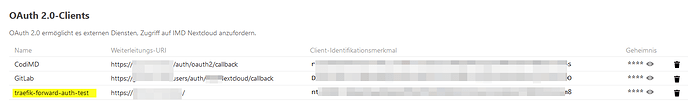
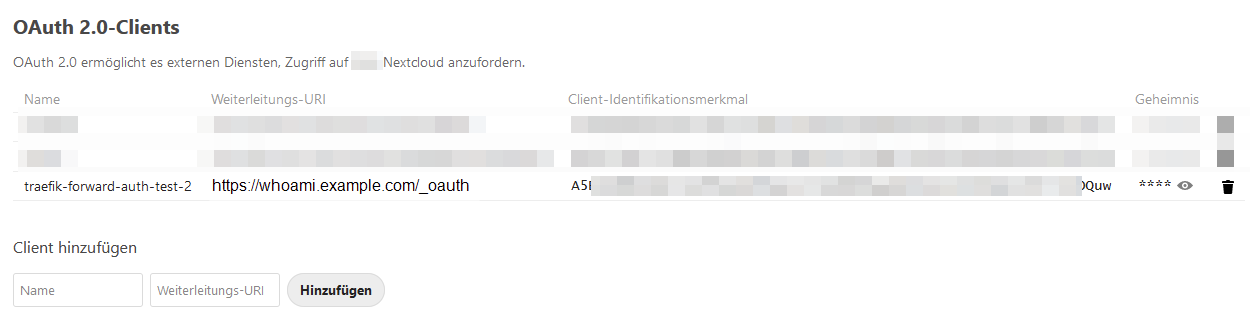
- I added another shiny OAuth2-Client to my nextcloud setup:
- I added one of the most basic examples to my server:
# docker-compose.yml version: "3.3" services: whoami: image: "traefik/whoami" container_name: "simple-service" labels: - "traefik.docker.network=traefik_proxy" - "traefik.enable=true" - "traefik.http.routers.whoami.rule=Host(`some.example.com`)" - "traefik.http.routers.whoami.entrypoints=websecure" - "traefik.http.routers.whoami.tls.certresolver=myhttpchallenge" - "traefik.http.routers.whoami.middlewares=auth-nextcloud" - "traefik.http.middlewares.auth-nextcloud.forwardauth.address=https://nc.example.com/apps/oauth2/authorize?response_type=code&client_id=nt---full-client-id---m8&redirect_url=https%3A%2F%2Fsome.example.com" - "traefik.http.middlewares.auth-nextcloud.forwardauth.trustForwardHeader=true" networks: traefik_proxy: networks: traefik_proxy: external: true
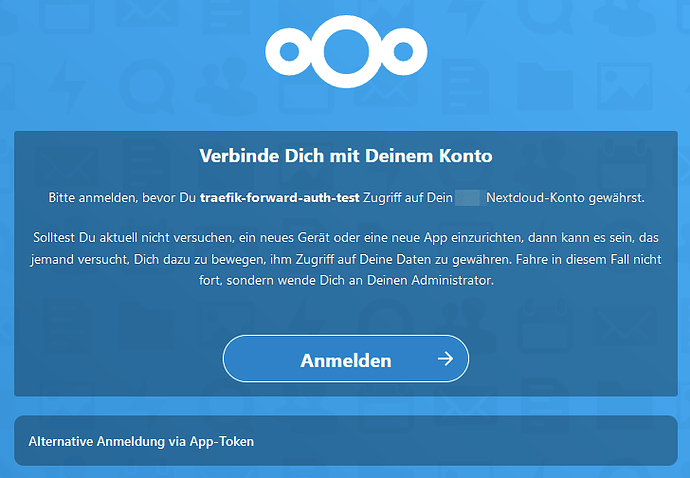
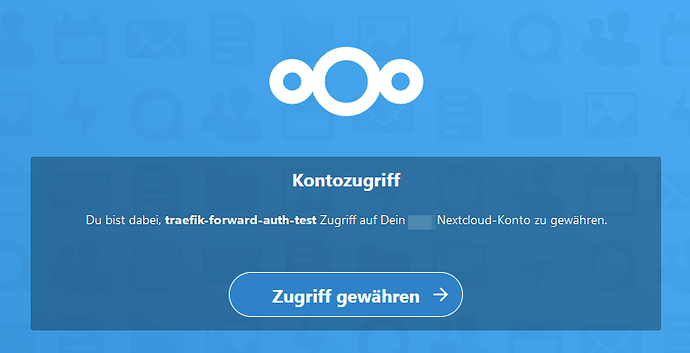
now, when I go to some.example.com, I am redirected to my nc.example.com site correctly, and there I get these screens, on which I am then stuck:
and then I’m back to the first one. The amount i can configure in both nextcloud and traefik is very small. I don’t really see where to go next. If you have read this far, maybe you can help me?