We need to define some stuff here.
Identifier/Login
A character strings that represents you. It’s probably not private, as it often uses your email or public username/handle. As far as security goes, it’s weak.
Password
A secret character string supposed to authentify someone. Problem is, it has to be stored on some server (preferably encrypted, but many sysadmins and devs are idiots and store it in plain text). Because it is stored on some server, it may leak into the wild (security breach or malevolent sysadmin). Also, because it’s only n characters (and people re-use passwords in many places), it can be guessed (either by bruteforce or by dictionnary). Also the password could be shared with a person you trust.
Authentication
The process by which a technical system asserts that the person trying to access data/account is the data/account’s owner. Authentication is typically done through login/password (with or without two-factor), but could also be done with RSA/ECC certificates or GPG keys.
Theat model
So anything accessible from the web can be hacked, in particular : passwords. Something that needs to be protected from hackers is your Nextcloud instance, because it probably contains sensitive info. Storing passwords in the very thing that should be protected is a very bad idea : in case it falls, the rest of your digital life falls with it.
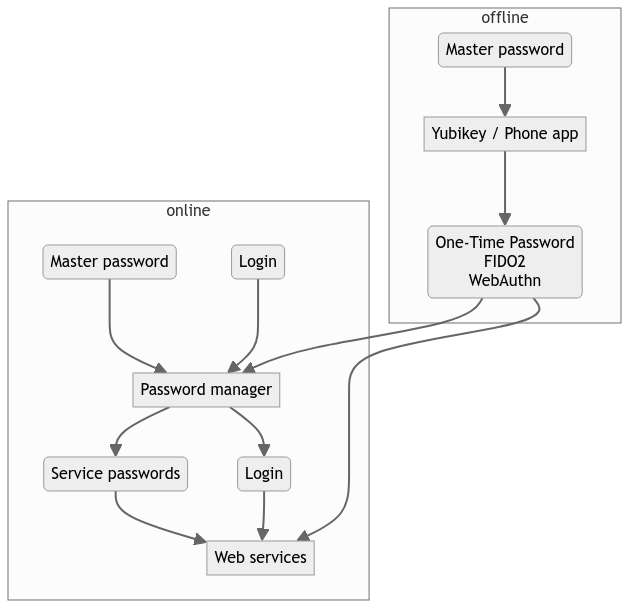
The point of two-factors is to mix the (server-side) passwords with a (client-side) one-time password, and connect server with OTP through cryptographic ways. Meaning someone would have to physically steal your smartphone (or any second factor authentifier) AND your server-side password to actually break in your system. Suddenly, it’s a lot more complicated for a hacker.
Now, indeed, relying on a smartphone that can be stolen, lost or destroyed, for the second factor has its caveats. But I’m afraid, the solution is not to backup everything where it can be hacked.
I would advise you to use something like a security key (Yubikey is the most ubiquitous) to handle your second factor. You can have more than one Yubikey for offline backups. You can wear the Yubikey on your keychain or around your neck. The Yubikey will securily hold your second factor offline, has its own password, and can be used on Linux/Mac/Windows/Android/MacOS, through Yubico Authenticator app. This app is merely a GUI for the key, and will display the one-time password that the key computes through its internal cryptographic magic.
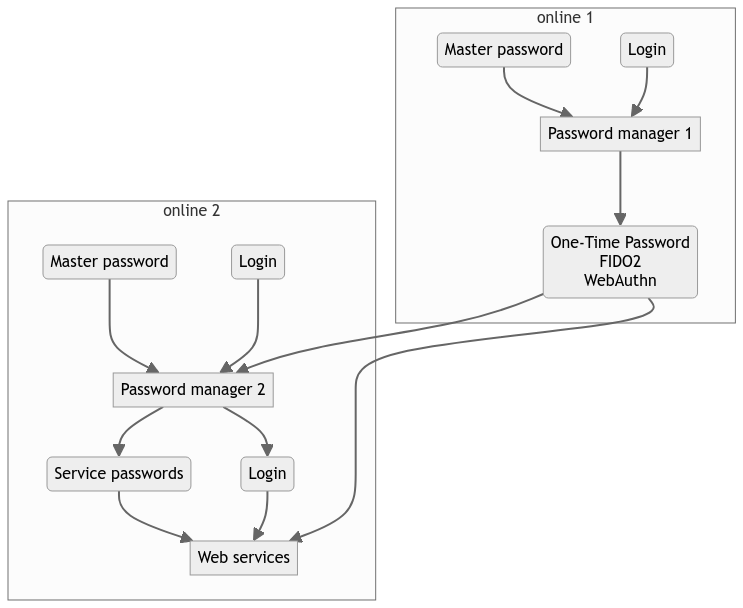
This solution allows you to have redundancy (several Yubikeys), that are all offline (can’t be breached from the web), and individually secured by an offline password (so even stealing the actual keys at your home don’t get hackers very far). After n wrong passwords inputs (n can be configured) they will also get blocked entirely (limited opportunities to try bruteforce).
But I strongly advise against using Nextcloud as a password vault, because it is on the web, and as such, it is exposed to threats, but also because it is already a central place where private data can be stolen. Even more if you are securing the Nextcloud server yourself, because properly securing a server is a difficult job, and if you trust your own server that much, you probably don’t understand security as much as you think.
Final words
Maybe one day you will end up in a coma, or at the hospital for a long time. It happens sooner that you think. Maybe this day, someone will need to take care of your taxes, health insurance, housing bills, kids and other sensitive stuff like that on your behalf, because you will be lying down in an hospital bed, unable to do it yourself.
Maybe this day, having turned your digital life into Fort Knox will be actively harmful to you. Always have a plan B for that case.