Hi.
If this is covered elsewhere please can someone point me in the correct direction please.
It feels like I’m not a million miles away from having Next Cloud running on my NAS server behind a reverse proxy accessible from the internet.
Apologies - I’ve had to mess around with addresses etc. as I’m a new user and can’t post more than 4 links.
All this is being done on an up to date Terra-Master F4-210 using Docker.
My Router NAT IP - 192dot168dot1dot254
My NAS IP - 192dot168dot1dot100
I have correctly installed NextCloud and got it up and running using the following docker-compose.yml
version: '2'
volumes:
nextcloud:
db:
services:
db:
image: mariadb
restart: always
command: --transaction-isolation=READ-COMMITTED --binlog-format=ROW
volumes:
- db:/var/lib/mysql
environment:
- MYSQL_ROOT_PASSWORD=rootpwd
- MYSQL_PASSWORD=userpwd
- MYSQL_DATABASE=nextcloud
- MYSQL_USER=nextcloud
app:
image: nextcloud
restart: always
ports:
- 8080:80
links:
- db
volumes:
- nextcloud:/var/www/html
environment:
- MYSQL_PASSWORD=userpwd
- MYSQL_DATABASE=nextcloud
- MYSQL_USER=nextcloud
- MYSQL_HOST=db
- VIRTUAL_HOST=nextcloud(dot)mydomain(dot)net
- LETSENCRYPT_HOST=nextcloud(dot)mydomain(dot)net
- LETSENCRYPT_EMAIL=abuse(at)mydomain(dot)net
(I’m not sure the last 3 lines are needed as that was when I was trying to set up a proxy in a different way)
docker-compose up -d starts everything and I can log into the NextCloud console (after creating an admin user) vi the LAN IP address of my Terra-master : (http://)192dot168dot1dot100:8080 from my PC on the same subnet.
I have set-up Nginx Proxy Manager following this recipe:
https://nginxproxymanager.com
My exact docker-compose.yml looks like this:
version: "3"
services:
app:
image: 'jc21/nginx-proxy-manager:latest'
restart: always
ports:
# Public HTTP Port:
- '80:80'
# Public HTTPS Port:
- '443:443'
# Admin Web Port:
- '81:81'
environment:
# These are the settings to access your db
DB_MYSQL_HOST: "db"
DB_MYSQL_PORT: 3306
DB_MYSQL_USER: "npm"
DB_MYSQL_PASSWORD: "userpasswd"
DB_MYSQL_NAME: "npm"
# If you would rather use Sqlite uncomment this
# and remove all DB_MYSQL_* lines above
# DB_SQLITE_FILE: "/data/database.sqlite"
# Uncomment this if IPv6 is not enabled on your host
# DISABLE_IPV6: 'true'
volumes:
- ./data:/data
- ./letsencrypt:/etc/letsencrypt
- ./config.json:/app/config/production.json
depends_on:
- db
db:
image: mariadb
restart: always
environment:
MYSQL_ROOT_PASSWORD: 'rootpasswd'
MYSQL_DATABASE: 'npm'
MYSQL_USER: 'npm'
MYSQL_PASSWORD: user'userpasswd'
volumes:
- ./data/mysql:/var/lib/mysql[/code]
This is a bit of a pain to get working: docker-compose up -d, then docker-compose down. Delete the directory that it’s created (./config.json) and then create a file ./config/json and add the following details:
{
"database": {
"engine": "mysql",
"host": "db",
"name": "npm",
"user": "npm",
"password": "userpasswd",
"port": 3306
},
}
And then do a docker-compose up -d again.
The Nginx proxy manager starts after a bit of waiting and then you can access on 192dot168dot1dot100:81.
I have DNS settings - netcloud(dot)mydomain(dot)net set up as a CNAME to DDNS domain other(dot)domain(dot)com and my router is set up to forward ports 80 and 443 to 192dot168dot1dot100:80 and :443 respectively.
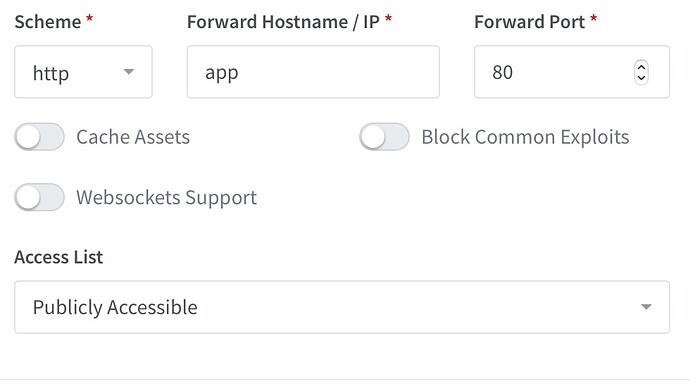
I have set up a proxy hosts rule in Nginx proxy manager to:
Listen on port 443, use LetsEncrypt (which created a certificate without problems - with the force SSL option) and forward that port to (http://)192dot168dot1dot100:8080 (the working NextCloud port)
I’ve added the following to the NextCloud config.php:
'trusted_domains' =>
array (
0 => '192dot168dot1dot100:8080',
1 => 'nextcloud(dot)mydomain(dot)net',
2 => 'UNRAID IP:PORT',
),
I’m not sure about 2 - followed that from another recipe somewhere
'trusted_proxies' =>
array (
0 => '192dot168dot1dot0/24',
1 => '172dot18dot0dot0/16',
),
The second one is the IP subnet of the proxy container.
'forwarded_for_headers' =>
array (
0 => 'X-Forwarded-For',
1 => 'HTTP_X_FORWARDED_FOR',
),
I the restarted the NextCloud with docker-compose down and docker-compose up -d
However - When I connect to (http://) nextcloud(dot)mydomain(dot)net the proxy server returns a 504 gateway timeout (after a delay) with this appearing in the proxy error log:
2021/01/13 14:54:48 [error] 4522#4522: *1127 upstream timed out (110: Operation timed out) while connecting to upstream, client: 192dot168dot1dot254, server: nextcloud(dot)mydomain(dot)net, request: "GET / HTTP/2.0", upstream: "(http://)192dot168dot1dot100:8080/", host: "nextcloud(dot)mydomain(day)net"
I’ve also tried modifying the rule config file as outlined at the bottom of this article https://shollyethan.medium.com/configuring-a-reverse-proxy-with-nginx-proxy-manager-cloudflare-and-a-custom-domain-100b5175fba2
Replacing
include conf.d/include/proxy.conf
with
add_header X-Served-By $host;
proxy_set_header Host $host;
proxy_set_header X-Forwarded-Scheme $scheme;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-For $remote_addr;
proxy_pass (https://)$server:$port;
Iv’e tried the last line as to http as well as the https documented.
However, if I change my port forwarding on the router to map port 80 to 192dot168dot1dot100:8080 (insecure just done for a test) then a (http) nextcloud(next)mydomain(dot)net connects and allows me to log in.
Also if I put my port forwarding back on the router to map port 80 to 192dot168dot1dot100:80 and change the Nginx proxy manager rule to map 192dot168dot1dot100:433 to 192dot168dot1dot254:80 sticking (https://) nextcloud(dot)mydomain(dot)net into a browser gives my router login page.
Any suggestions gratefully received.