I’ve been following DBTech tutorials to setup a Nextcloud instance and I want to use Cloudflare Tunnel to access it over the internet.
Cloudflare Tunnel provides DDOS protection, firewall and many other features to keep the website safe from external factors, but is the Tunnel private (privacy focused)? Like is it truly encrypted? When I upload a file or use Nextcloud Talk to chat with my friends, is it possible that Cloudflare can view the decrypted contents?
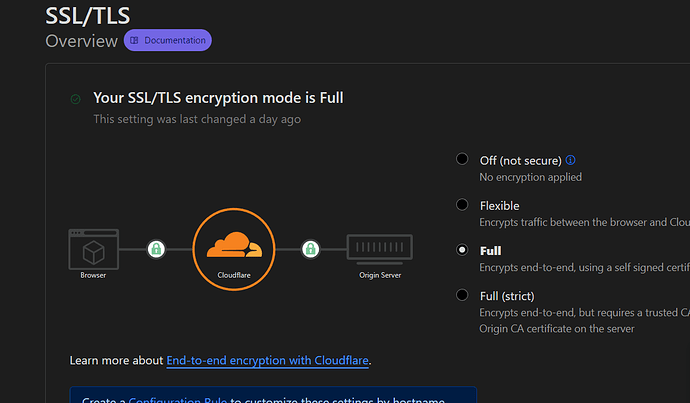
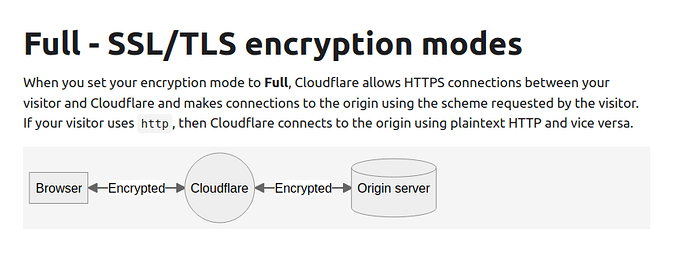
The free plan doesn’t allow usage of any other SSL certificates, you have to use the one provided by Cloudflare, and the origin server can only use SSL certificates from Cloudflare.
I’ve read few posts saying it’s not really private, but the Nextcloud AIO documentation says it can be hosted behind a Cloudflare Tunnel.
Is there a way to harden Cloudflare Tunnel? If it isn’t private, are there any other good alternatives?
I’m new to self hosting, so I’m sorry if these things sound trivial, but I really need to know if the service (Cloudflare Tunnel) is privacy focused before using it.