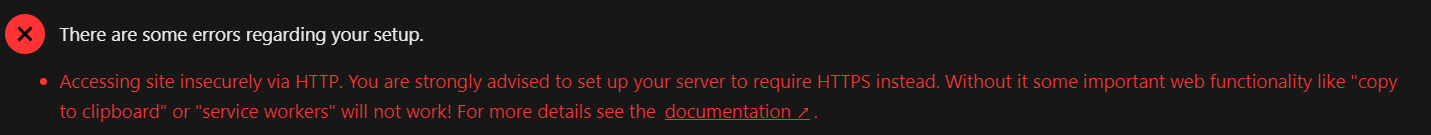
I recently re-installed Nextcloud using docker-compose from a different drive, and I went through all the installation process and SSL certificate assignment and reverse proxy just like how I did it before, only this time I received the following error in the Nextcloud Overview Section:
At first, I was confused, since my browser:
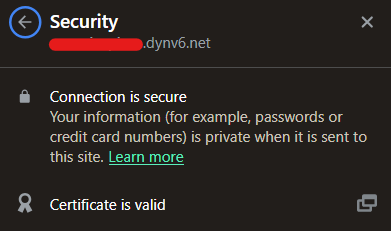
reported that the webUI is on https, and whatever NC prompted such as copy to clipboard not working, worked just fine.
The website worked perfectly, even though it gave an error 504 every time i tried logging in, but it logged in normally once i refreshed the page, so I didnt’ think that was too big of an issue.
So, I tried signing in through the desktop client, however it gave me the following error:
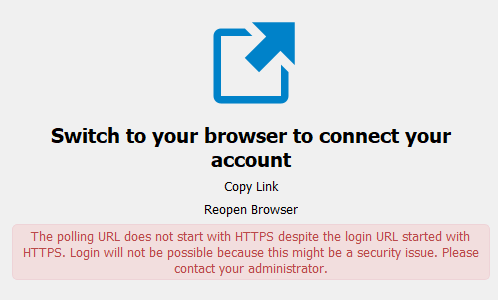
I figured the solution might lie in the error i received in the NC overview, so I rechecked my configs, thinking I might have made a mistake, but I couldn’t find anything.
I am using Nextcloud 29.0.1 on Zorin OS Lite 16.3 (Ubuntu 20.04)
For the reverse proxy I am using nginx-1.18
I tried finding similar issues in the community, but almost everyone uses apache2, so I couldnt get a clear resolution.
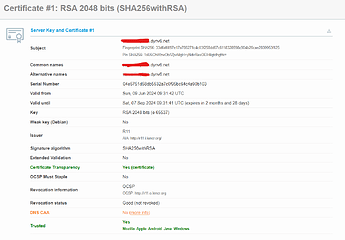
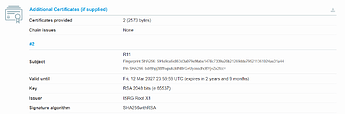
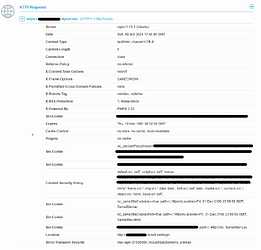
But then I ran the Qualys SSL test, below are the important parts of the results:
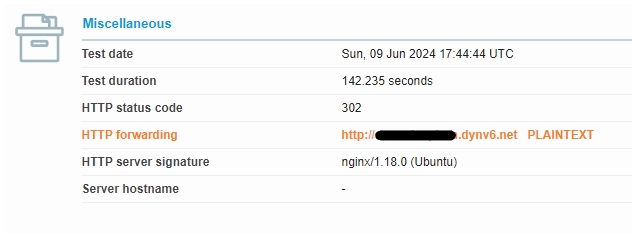
What caught my eye is that in the Miscellaneous section, the HTTP forwarding is not going to HTTPS, also that the HTTP status code is 302, even though we know that for nginx to redirect http traffic to https, it sends an HTTP request 301.
Speaking of which, Here is my /etc/nginx/conf.d/nextcloud.conf file:
server {
root /var/www/html;
server_name foo.dynv6.net;
location / {
proxy_pass http://localhost:8080;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains; preload";
client_max_body_size 0;
}
location /.well-known/carddav {
return 301 $scheme://$host/remote.php/dav;
}
location /.well-known/caldav {
return 301 $scheme://$host/remote.php/dav;
}
listen [::]:443 ssl ipv6only=on; # managed by Certbot
listen 443 ssl; # managed by Certbot
ssl_certificate /etc/letsencrypt/live/foo.dynv6.net/fullchain.pem; # managed by Certbot
ssl_certificate_key /etc/letsencrypt/live/foo.dynv6.net/privkey.pem; # managed by Certbot
include /etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot
}
server {
if ($host = foo.dynv6.net) {
return 301 https://$host$request_uri;
} # managed by Certbot
listen 80;
listen [::]:80;
server_name foo.dynv6.net;
return 404; # managed by Certbot
}
it seemed to be fine, but then I checked my Nextcloud’s config.php as well:
<?php
$CONFIG = array (
'htaccess.RewriteBase' => '/',
'memcache.local' => '\\OC\\Memcache\\APCu',
'apps_paths' =>
array (
0 =>
array (
'path' => '/var/www/html/apps',
'url' => '/apps',
'writable' => false,
),
1 =>
array (
'path' => '/var/www/html/custom_apps',
'url' => '/custom_apps',
'writable' => true,
),
),
'memcache.distributed' => '\\OC\\Memcache\\Redis',
'memcache.locking' => '\\OC\\Memcache\\Redis',
'redis' =>
array (
'host' => 'redis',
'password' => '<redacted>',
'port' => 6379,
),
'instanceid' => '<redacted>',
'passwordsalt' => '<redacted>',
'secret' => '<redacted>',
'trusted_domains' =>
array (
0 => 'foo.dynv6.net',
1 => '1xx.1xx.2xx.1xx',
),
'mail_smtpstreamoptions' =>
array (
'ssl' =>
array (
'allow_self_signed' => true,
'verify_peer' => false,
'verify_peer_name' => false,
),
),
'upgrade.disable-web' => true,
'datadirectory' => '/var/www/html/data',
'dbtype' => 'mysql',
'version' => '29.0.1.1',
'overwriteprotoccol' => 'https',
'overwrite.cli.url' => 'https://foo.dynv6.net',
'dbname' => 'db',
'dbhost' => 'db',
'dbport' => '',
'dbtableprefix' => 'oc_',
'opcache.memory_consumption=512M',
'opcache.jit = 1255',
'opcache.jit_buffer_size = 256M',
'mysql.utf8mb4' => true,
'dbuser' => 'NextCloud',
'dbpassword' => '<redacted>',
'installed' => true,
'default_phone_region' => '<redacted>',
'default_timezone' => '<redacted>',
'maintenance_window_start' => 1,
'logfile' => '/var/log/nextcloud.log',
'loglevel' => 2,
'mail_from_address' => '<redacted>',
'mail_smtpmode' => 'smtp',
'mail_sendmailmode' => 'smtp',
'mail_domain' => 'gmail.com',
'mail_smtphost' => 'smtp.gmail.com',
'mail_smtpport' => '465',
'mail_smtpauth' => 1,
'mail_smtpname' => '<redacted>',
'mail_smtppassword' => '<redacted>,
'mail_smtpsecure' => 'ssl',
);
The protocol was being overwritten, as well as the cli-url, but I was getting the same issue again and again. I purged and reinstalled nginx, purged and reinstalled certbot; however the problem still persisted. I found myself out of ways to troubleshoot and decided to approach the community for my problem. I would really be thankful for any help. If you need any other diagnostic information, please ask me, I’ll be happy to provide them. Thank you!