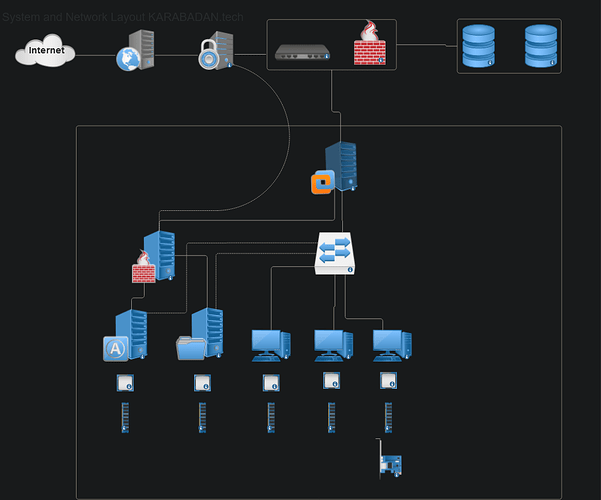
First, don’t use LXCs, and certainly not privileged LXCs, if you plan to expose it to the internet. That way you you have better isolation from the host and the rest of you’re services you might run on that host. Further put it in a separate network segment / VLAN, and don’t allow traffic to other subnets, so when you’re Nextcloud should be comromized they cannot pivit to other things you’re running on your network, or comporomise the host the VM is running on.
Reverse Proxies are not a security feature, especially if they are running on the same machine/VM/network segment with the rest of your services. They are mainly needed to direct traffic to multiple services behind a single public IP, because you cannot forward port 80/443 to multiple local IP addresses, and in larger envirements they can also be used for traffic shaping and load balancing. Cloudflare adds some “magic (security) sauce” to it, but this comes with a price. 1.) Things like large file upload don’t work very well with Coudflare tunnels, at least not with their free plans. 2.) Now you have to trust Cloudflare, that they don’t mess with your data.
I can only say what I do. I’m running Nextcloud in a VM on Proxmox, and I port forward Port 80/443 directly to that VM. On that VM I’m running a classic LAMP stack, secured with Let’s Encrypt and Fail2ban.
BUT! I’m just a home user…
…and since you are planing to use it in a business, I wouldn’t recommend doing anything without doing proper planing and risk assesment, and I would certainly not recommend to use a home lab “hobbyist” product like NGINX Proxy Manager. 
Also, your questions aren’t specific to Nextcloud, but rather about general concepts of how you should design your infrastructure, which is highly dependent on the size of your organization, the nature of your business, and of course your budget.
So I’d say you should probably hire a professional IT consultant that will help you to plan your infrastructure or maybe even hire an MSP that can also help to buld it out and manage it.
If this all sounds already too complicated and/or too expensive for you, you probably shouldn’t host it yourself, and use a managed Nextcloud provider instead. Or at least don’t publicly expose it, and use a VPN or overlay network like Tailscale to access it remotely.