we are trying to user the new SAML App in addition with user_ldap. can anyone tell me how to configure it on the admin panel?
it doesn´t work with this shibboleth idp configuration:
general-uid_mapping: mail
general-require_provisioned_account: 0
idp-entityId: https://myurl/idp/shibboleth
idp-singleSignOnService.url: https://myurl/idp/profile/Shibboleth/SSO
thanks
Hi @julio1501
This entirely depends on your Shibboleth configuration. It may be best to check the Shibboleth server error logs for errors.
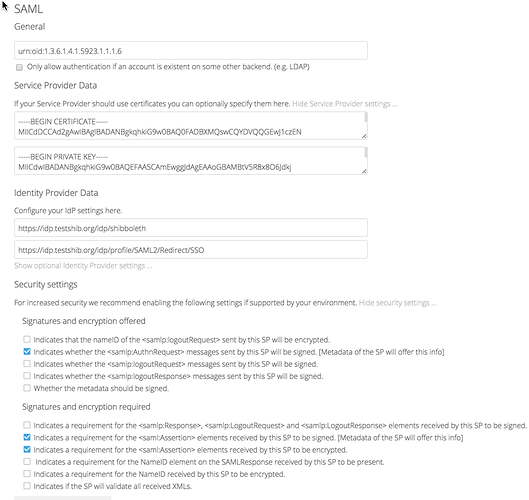
My first guess would be that your IdP requires a certificate and signed communication? The following works for testshib.org after the metadata has been uploaded to their platform:
Your Single-Sign-On Service URL has likely to be something alone the lines of “https://idp.testshib.org/idp/profile/SAML2/Redirect/SSO”, that’s what it would be for testshib.
I can very much imagine that your Shibboleth server also requires to have the signing and encryption to be properly configured, if so: Then configure some certificates.
What works with testshib.org is the following:
- Generate certificates with the correct common name
- Enter Identity Provider using the IdP from your provider, available from https://idp.testshib.org/idp/profile/Metadata/SAML (adjust domain):
- Security Settings, check the following:
- Indicates whether the samlp:AuthnRequest messages sent by this SP will be signed. [Metadata of the SP will offer this info]
- Indicates a requirement for the saml:Assertion elements received by this SP to be encrypted.
- Indicates a requirement for the saml:Assertion elements received by this SP to be signed. [Metadata of the SP will offer this info]
- Download metadata and configure in your shibboleth.
Also are you sure that you really use mail as general-uid_mapping? Normally that would be something like urn:oid:1.3.6.1.4.1.5923.1.1.1.6 if you want to match on the Mail Address.
This config will do for testshib.org, of course this is a dummy certificate only valid for me 
| appid |
configkey |
configvalue |
| user_saml |
general-require_provisioned_account |
0 |
| user_saml |
general-uid_mapping |
urn:oid:1.3.6.1.4.1.5923.1.1.1.6 |
| user_saml |
idp-entityId |
https://idp.testshib.org/idp/shibboleth |
| user_saml |
idp-singleSignOnService.url |
https://idp.testshib.org/idp/profile/SAML2/Redirect/SSO |
| user_saml |
idp-singleLogoutService.url |
|
| user_saml |
idp-x509cert |
-----BEGIN CERTIFICATE-----
MIIEDjCCAvagAwIBAgIBADANBgkqhkiG9w0BAQUFADBnMQswCQYDVQQGEwJVUzEV
MBMGA1UECBMMUGVubnN5bHZhbmlhMRMwEQYDVQQHEwpQaXR0c2J1cmdoMREwDwYD
VQQKEwhUZXN0U2hpYjEZMBcGA1UEAxMQaWRwLnRlc3RzaGliLm9yZzAeFw0wNjA4
MzAyMTEyMjVaFw0xNjA4MjcyMTEyMjVaMGcxCzAJBgNVBAYTAlVTMRUwEwYDVQQI
EwxQZW5uc3lsdmFuaWExEzARBgNVBAcTClBpdHRzYnVyZ2gxETAPBgNVBAoTCFRl
c3RTaGliMRkwFwYDVQQDExBpZHAudGVzdHNoaWIub3JnMIIBIjANBgkqhkiG9w0B
AQEFAAOCAQ8AMIIBCgKCAQEArYkCGuTmJp9eAOSGHwRJo1SNatB5ZOKqDM9ysg7C
yVTDClcpu93gSP10nH4gkCZOlnESNgttg0r+MqL8tfJC6ybddEFB3YBo8PZajKSe
3OQ01Ow3yT4I+Wdg1tsTpSge9gEz7SrC07EkYmHuPtd71CHiUaCWDv+xVfUQX0aT
NPFmDixzUjoYzbGDrtAyCqA8f9CN2txIfJnpHE6q6CmKcoLADS4UrNPlhHSzd614
kR/JYiks0K4kbRqCQF0Dv0P5Di+rEfefC6glV8ysC8dB5/9nb0yh/ojRuJGmgMWH
gWk6h0ihjihqiu4jACovUZ7vVOCgSE5Ipn7OIwqd93zp2wIDAQABo4HEMIHBMB0G
A1UdDgQWBBSsBQ869nh83KqZr5jArr4/7b+QazCBkQYDVR0jBIGJMIGGgBSsBQ86
9nh83KqZr5jArr4/7b+Qa6FrpGkwZzELMAkGA1UEBhMCVVMxFTATBgNVBAgTDFBl
bm5zeWx2YW5pYTETMBEGA1UEBxMKUGl0dHNidXJnaDERMA8GA1UEChMIVGVzdFNo
aWIxGTAXBgNVBAMTEGlkcC50ZXN0c2hpYi5vcmeCAQAwDAYDVR0TBAUwAwEB/zAN
BgkqhkiG9w0BAQUFAAOCAQEAjR29PhrCbk8qLN5MFfSVk98t3CT9jHZoYxd8QMRL
I4j7iYQxXiGJTT1FXs1nd4Rha9un+LqTfeMMYqISdDDI6tv8iNpkOAvZZUosVkUo
93pv1T0RPz35hcHHYq2yee59HJOco2bFlcsH8JBXRSRrJ3Q7Eut+z9uo80JdGNJ4
/SJy5UorZ8KazGj16lfJhOBXldgrhppQBb0Nq6HKHguqmwRfJ+WkxemZXzhediAj
Geka8nz8JjwxpUjAiSWYKLtJhGEaTqCYxCCX2Dw+dOTqUzHOZ7WKv4JXPK5G/Uhr
8K/qhmFT2nIQi538n6rVYLeWj8Bbnl+ev0peYzxFyF5sQA==
-----END CERTIFICATE----- |
| user_saml |
security-authnRequestsSigned |
1 |
| user_saml |
security-wantAssertionsEncrypted |
1 |
| user_saml |
sp-x509cert |
-----BEGIN CERTIFICATE-----
MIICdDCCAd2gAwIBAgIBADANBgkqhkiG9w0BAQ0FADBXMQswCQYDVQQGEwJ1czEN
MAsGA1UECAwEVGVzdDENMAsGA1UECgwEdGVzdDEqMCgGA1UEAwwhbXRlc3RraXRl
LW15bmV4dGNsb3VkLnBhZ2VraXRlLm1lMB4XDTE2MDcwNjEwMDUxMloXDTE3MDcw
NjEwMDUxMlowVzELMAkGA1UEBhMCdXMxDTALBgNVBAgMBFRlc3QxDTALBgNVBAoM
BHRlc3QxKjAoBgNVBAMMIW10ZXN0a2l0ZS1teW5leHRjbG91ZC5wYWdla2l0ZS5t
ZTCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEAwG1XlHzHw7ol2SM1JL8iXzEQ
2u9/FlzxXsqe30GJYsV6oOGbybB2qsIr/HTJW8uFsF+68bx87+XHesNzIMyoVwJS
HudkMUvIrPIYYS3tkw84DYHE8aytCPNwdn6Y4Ph3Je5Urcz/R/G5RPFa0j20d3y8
he43FJQLBXbqsGmXeMcCAwEAAaNQME4wHQYDVR0OBBYEFJ8/rVfyF3ExwfNe2rvd
0AWOYvoyMB8GA1UdIwQYMBaAFJ8/rVfyF3ExwfNe2rvd0AWOYvoyMAwGA1UdEwQF
MAMBAf8wDQYJKoZIhvcNAQENBQADgYEAZKi3vt90VEyy0D5kv80KyIF1ctlIAMrB
zP9cl3aIN6CQbpyKvkXvcaC/MpxcdQxCTPUKnjunNVfbT/ZPK55kuaPGbmkslkPO
6nq4eEvOkTFX0hDV/AXxijdPNilUueYLuUt/wvnj8o3y2wHDtG5lYE9pwgan/lcM
r/VcaQnapVk=
-----END CERTIFICATE----- |
| user_saml |
sp-privateKey |
-----BEGIN PRIVATE KEY-----
MIICdwIBADANBgkqhkiG9w0BAQEFAASCAmEwggJdAgEAAoGBAMBtV5R8x8O6Jdkj
NSS/Il8xENrvfxZc8V7Knt9BiWLFeqDhm8mwdqrCK/x0yVvLhbBfuvG8fO/lx3rD
cyDMqFcCUh7nZDFLyKzyGGEt7ZMPOA2BxPGsrQjzcHZ+mOD4dyXuVK3M/0fxuUTx
WtI9tHd8vIXuNxSUCwV26rBpl3jHAgMBAAECgYBK3b/HW8z1D8WN967Df0HGO3bN
V4TglISsVrT9M6haL28IjP5puChTQ3yNmnqFJmf7OSOozabmR0YXM1flmPqdQfIC
4Bv63hdyyC4eGgt9hLxGdrvYvtBrqljvFWfAfxvd3BWUrCO+HQpgtoM4Om6nezAG
fhz1kOMynxbWKT/yQQJBAPbJETZ/ZAVCdBs90sEl1OKSX2tU1vs7GbNd8xSjaBEA
iyetm+GU5qDjb/GKHp20RRolufklDMScuz6DfKOzTXECQQDHnK747qa9wZb/htws
TrR5Nt3T6OQHWw8CVyHm6Iqvt7G6WWSXfz2gL8C1o++WX6NREGytIRf/DYykYPcC
km23AkEA9pvCeaUffCoGAFrtSlnVvHvsokLrea57ZkRR7qPEEIlshT/1b5zuQoRE
jygopAtKqnBcwV2GvsqoSjX2zVcV4QJAWtc6Zb0uEtNEJZu5HUzgIv3OK/8jrxlI
llcS7aPMYbVmY5kFB1D3uauhtsgZY8S4bU7dNlkGM6N16uTZ5MjAtwJBAJ3i+CI0
ysgHpc442oJ/NKIOBryWu51L1ByeN3lB979x1jZLxyRbHe1OYpNjTkA7nC48mkl7
+BilKtditPTeSUA=
-----END PRIVATE KEY----- |
| user_saml |
security-wantAssertionsSigned |
1 |
If you have any more questions please let us know! If you encounter any bug or have a feature request, please file them directly at GitHub - nextcloud/user_saml: App for authenticating Nextcloud users using SAML
Best,
Lukas
Also, since you want to use it in addition with the LDAP app you may want to check " Only allow authentication if an account is existent on some other backend. (e.g. LDAP)".
This will disable auto provisioning, if somebody is not existent in the LDAP they will then be rejected the login. That’s something that I’d highly recommend to do!
Hi,
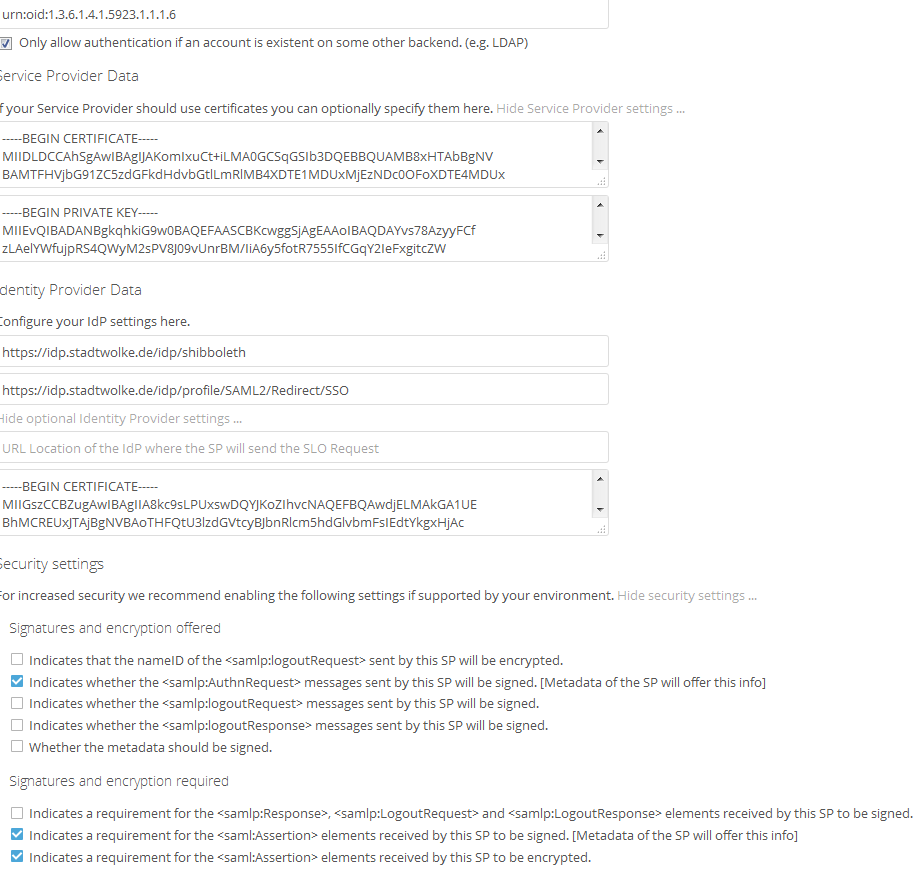
the idp server doesn´t give any error. The nextcloud server only shows this error:
{“reqId”:“DGaxutmWrSIZneGAyPXw”,“remoteAddr”:“xx.xxx.xx.xx”,“app”:“index”,“message”:"Exception: {"Exception":"Doctrine\\DBAL\\Exception\\InvalidFieldNameException","Message":"An exception occurred while executing ‘SELECT token FROM oc_user_saml_users WHERE uid = ? LIMIT 1’ with params [null]:\n\nSQLSTATE[42S22]: Column not found: 1054 Unknown column ‘token’ in ‘field list’","Code":0,"Trace":"#0 \/var\/www\/nextcloud\/3rdparty\/doctrine\/dbal\/lib\/Doctrine\/DBAL\/DBALException.php(116): Doctrine\\DBAL\\Driver\\AbstractMySQLDriver->convertException('An exception oc…
my config is the following:
Thanks. I could reproduce your problem locally here. This seems to be caused by a small mistake in the code that doesn’t happened on the development environment due to the fact that DB behaves more forgetting there.
Many apologies for that, this should not have happened.
Can I ask you to test the change in https://github.com/nextcloud/user_saml/pull/20 ?
2 Likes
Thanks. it works now like a charm.
And we can use the app in addition with our ldap users. it´s great!
2 Likes
Thanks for the feedback, @julio1501 very much appreciated!
If you have any feature request or bug reports please file them at https://github.com/nextcloud/user_saml/issues. That would be awesome