STrike
August 16, 2020, 4:27pm
1
Hello everbody,
I have some files in my clouds which are installer for windows. For example driver for printer and so an which I don´t want to search everytime in the www.
One is wrongly detected as a virus:
Fatal files_antivirus Infected file found (during background scan) Win.Virus.Ramnit-7537604-0 File: 1268538Account: *** Path: /***/files/Installer/Labelprinter Q710 Treiber.zip
It´s spamming my activities and my logs and I think that is a bad behavior for my enviroment (Makes MySQL and logs large…).
Can I whitelist this file in any way? Maybe as clamav exception or directly in the nextcloud app Anti Virus?
Cheers.
j-ed
August 17, 2020, 8:07am
2
I think this is the wrong place to search for an answer on your question, because the mentioned app relies on clamav, an external anti-virus scanner. Therefore you should e.g. ask aunt G. for an answer:
https://www.google.com/search?client=firefox-b-d&q=clamav+whitelist+file
@STrike STrike
STrike
August 21, 2020, 4:37pm
4
Why do you think this is the wrong place for an answer? Year I know this is based on clamav, but maybe another user has the same question. And I can´t find another support platform for the scanner, but the Nextcloud app is based on it.
@devnull I think to use multi zips is annoying and for me a not wanted behavior to do that.
Back to whitelistings:http://www.owlbearconsulting.com/doku.php?id=linux_wiki:clamav
Whitelist a File
To whitelist a file:
Generate a md5 signature for the file and append it to the file whitelist
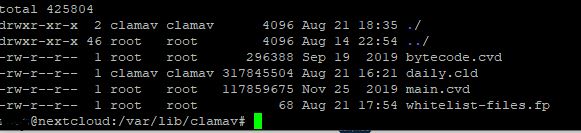
sigtool --md5 /data/testfile >> /var/lib/clamav/whitelist-files.fp
The entry will look like this
cat /var/lib/clamav/whitelist-files.fp
d41d8cd98f00b204e9800998ecf8427e:0:testfile
Fields are → MD5sum:Filesize:Comment
I got the following entry:
Actually I try it without the .zip ending. I’ll let you know if it works.
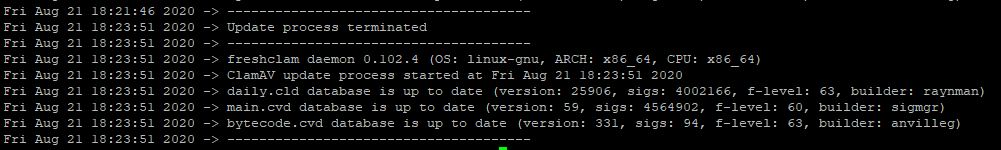
My logs:
Clamav:
The Virus Log entry:
Edit:
Tested it now with clamscan:
----------- SCAN SUMMARY -----------
Its not infected now, but nextcloud with clamav daemon is still recognizing it as a virus.
did you know there is extra ClamAV options inside the Admin Settings -> Security page.
you can add a custom regex rule there like :
Scanner output /.*.(31cd5e66d1866aacfcb5291d131f37be:94208) FOUND$/ not checked
I have not tried this myself and do not know how this will appear in your log.
STrike
August 24, 2020, 10:24am
6
I got the following SQL Error in my Log files and the change will not commited. After reloading the page it is still not there.
Doctrine\DBAL\Exception\DriverException: An exception occurred while executing 'INSERT INTO `oc_files_avir_status`(`status_type`,`description`,`status`,`result`) VALUES(?,?,?,?)' with params [1, "", -1, " \/.*.(31cd5e66d1866aacfcb5291d131f37be:94208) FOUND$\/"]: SQLSTATE[22007]: Invalid datetime format: 1366 Incorrect integer value: ' /.*.(31cd5e66d1866aacfcb5291d131f37be:94208) FOUND$/' for column `nextcloud`.`oc_files_avir_status`.`result` at row 1
/var/www/nextcloud/3rdparty/doctrine/dbal/lib/Doctrine/DBAL/DBALException.php - line 169:
Doctrine\DBAL\Driver\AbstractMySQLDriver->convertException()
/var/www/nextcloud/3rdparty/doctrine/dbal/lib/Doctrine/DBAL/DBALException.php - line 145:
Doctrine\DBAL\DBALException::wrapException()
/var/www/nextcloud/3rdparty/doctrine/dbal/lib/Doctrine/DBAL/Statement.php - line 162:
Doctrine\DBAL\DBALException::driverExceptionDuringQuery()
/var/www/nextcloud/lib/public/AppFramework/Db/Mapper.php - line 255:
Doctrine\DBAL\Statement->execute()
/var/www/nextcloud/lib/public/AppFramework/Db/Mapper.php - line 129:
OCP\AppFramework\Db\Mapper->execute()
/var/www/nextcloud/apps/files_antivirus/lib/Controller/RuleController.php - line 86:
OCP\AppFramework\Db\Mapper->insert()
/var/www/nextcloud/lib/private/AppFramework/Http/Dispatcher.php - line 170:
OCA\Files_Antivirus\Controller\RuleController->save()
/var/www/nextcloud/lib/private/AppFramework/Http/Dispatcher.php - line 99:
OC\AppFramework\Http\Dispatcher->executeController()
/var/www/nextcloud/lib/private/AppFramework/App.php - line 125:
OC\AppFramework\Http\Dispatcher->dispatch()
/var/www/nextcloud/lib/private/AppFramework/Routing/RouteActionHandler.php - line 47:
OC\AppFramework\App::main()
<<closure>>
OC\AppFramework\Routing\RouteActionHandler->__invoke()
/var/www/nextcloud/lib/private/Route/Router.php - line 299:
call_user_func()
/var/www/nextcloud/lib/base.php - line 1008:
OC\Route\Router->match()
/var/www/nextcloud/index.php - line 38:
OC::handleRequest()
Verursacht durchDoctrine\DBAL\Driver\PDOException: SQLSTATE[22007]: Invalid datetime format: 1366 Incorrect integer value: ’ /.*.(31cd5e66d1866aacfcb5291d131f37be:94208) FOUND$/’ for column nextcloud.oc_files_avir_status.result at row 1
/var/www/nextcloud/3rdparty/doctrine/dbal/lib/Doctrine/DBAL/Statement.php - line 153:
Doctrine\DBAL\Driver\PDOStatement->execute()
/var/www/nextcloud/lib/public/AppFramework/Db/Mapper.php - line 255:
Doctrine\DBAL\Statement->execute()
/var/www/nextcloud/lib/public/AppFramework/Db/Mapper.php - line 129:
OCP\AppFramework\Db\Mapper->execute()
/var/www/nextcloud/apps/files_antivirus/lib/Controller/RuleController.php - line 86:
OCP\AppFramework\Db\Mapper->insert()
/var/www/nextcloud/lib/private/AppFramework/Http/Dispatcher.php - line 170:
OCA\Files_Antivirus\Controller\RuleController->save()
/var/www/nextcloud/lib/private/AppFramework/Http/Dispatcher.php - line 99:
OC\AppFramework\Http\Dispatcher->executeController()
/var/www/nextcloud/lib/private/AppFramework/App.php - line 125:
OC\AppFramework\Http\Dispatcher->dispatch()
/var/www/nextcloud/lib/private/AppFramework/Routing/RouteActionHandler.php - line 47:
OC\AppFramework\App::main()
<<closure>>
OC\AppFramework\Routing\RouteActionHandler->__invoke()
/var/www/nextcloud/lib/private/Route/Router.php - line 299:
call_user_func()
/var/www/nextcloud/lib/base.php - line 1008:
OC\Route\Router->match()
/var/www/nextcloud/index.php - line 38:
OC::handleRequest()
Verursacht durchPDOException: SQLSTATE[22007]: Invalid datetime format: 1366 Incorrect integer value: ’ /.*.(31cd5e66d1866aacfcb5291d131f37be:94208) FOUND$/’ for column nextcloud.oc_files_avir_status.result at row 1
/var/www/nextcloud/3rdparty/doctrine/dbal/lib/Doctrine/DBAL/Driver/PDOStatement.php - line 117:
PDOStatement->execute()
/var/www/nextcloud/3rdparty/doctrine/dbal/lib/Doctrine/DBAL/Statement.php - line 153:
Doctrine\DBAL\Driver\PDOStatement->execute()
/var/www/nextcloud/lib/public/AppFramework/Db/Mapper.php - line 255:
Doctrine\DBAL\Statement->execute()
/var/www/nextcloud/lib/public/AppFramework/Db/Mapper.php - line 129:
OCP\AppFramework\Db\Mapper->execute()
/var/www/nextcloud/apps/files_antivirus/lib/Controller/RuleController.php - line 86:
OCP\AppFramework\Db\Mapper->insert()
/var/www/nextcloud/lib/private/AppFramework/Http/Dispatcher.php - line 170:
OCA\Files_Antivirus\Controller\RuleController->save()
/var/www/nextcloud/lib/private/AppFramework/Http/Dispatcher.php - line 99:
OC\AppFramework\Http\Dispatcher->executeController()
/var/www/nextcloud/lib/private/AppFramework/App.php - line 125:
OC\AppFramework\Http\Dispatcher->dispatch()
/var/www/nextcloud/lib/private/AppFramework/Routing/RouteActionHandler.php - line 47:
OC\AppFramework\App::main()
<<closure>>
OC\AppFramework\Routing\RouteActionHandler->__invoke()
/var/www/nextcloud/lib/private/Route/Router.php - line 299:
call_user_func()
/var/www/nextcloud/lib/base.php - line 1008:
OC\Route\Router->match()
/var/www/nextcloud/index.php - line 38:
OC::handleRequest()
Please What database are you using and what version of NC and ClamAV
php -mclamd --version
I have got the Eicar test file and have been able to allow it to be uploaded. the regex need to be adjusted and there is a issue with the safety.
ISSUE: The regex length in the db is only 64 char.
the rexeg that did NOT work for me
/.*Eicar-Test-Signature(69630e4574ec6798239b091cda43dca0:69) FOUND$/
and also NOT WORKING
/.*(69630e4574ec6798239b091cda43dca0:69) FOUND$/
the regex that DID WORK
/.*Eicar-Test-Signature(.*) FOUND$/
also the last dropdown box should be the first option clean or Aufräumen
for your file the working regex would be
/.*Win.Virus.Ramnit-7537604-0.* FOUND$/
but it seems something is not right I did not got any errors entering the regex
STrike
August 24, 2020, 8:17pm
8
php -m
[Zend Modules]
ClamAV 0.102.4/25909/Mon Aug 24 15:26:24 2020
Thats true, I saw that only in the logs of nextcloud. Nextcloud 18.0.7
I included the whitelist.fp and during scans in console its working with the whitelist, but not in nextcloud.
10.4.14-MariaDB-1:10.4.14+maria~bionic
EDIT: I tried nowWin.Virus.Ramnit-7537604-0. FOUND$/
When you enter the rule there is a check mark in front to save it. Did you press it so it’s saved ?
Edit. You need to include the * as wildcard
/.*Win.Virus.Ramnit-7537604-0.* FOUND$/
STrike
August 24, 2020, 10:43pm
10
Sorry the discourse format edited my style above. Year I included the * as wildcard.
When I try to click on the check mark nothing happens.
Firefox 79.0 (64-Bit) was not successful in adding new exceptions./.*:Win.Virus.Ramnit-7537604-0.* FOUND$/
STrike
September 2, 2020, 5:07pm
11
Sill not working with latest v3.0.0.
So I opened an issue:
opened 11:30PM - 28 Aug 20 UTC
Steps to reproduce
Install it
Configure it and its still there.
Expected behaviour
Make exceptions like the whitelist.fp for files or for virus category. Should...