Support intro
Nextcloud version : 30.0.1.2 (docker)
Operating system and version: Debian 12
Apache or nginx version: 2.12.1 (docker)
PHP version: 8.2.25
I mounted my ntfs drive in nextcloud, but whenever I browse in Files I got an error in logging (shown below):
Exception
OCA\Files_External\Service\DBConfigService::getMountById(): Argument #1 ($mountId) must be of type int, string given, called in /var/www/html/apps/files_external/lib/Service/StoragesService.php on line 138 in file '/var/www/html/apps/files_external/lib/Service/DBConfigService.php' line 48
My ntfs drive permission is set as 777. I do see the files from nextcloud, so I’m not sure what it doesn’t like.
Another error from Nextcloud memories might be related. It says it can’t index the folder I mounted even thought it display all photos correctly (log error shown below).
Failed to index folder /tamashika/files/onetouch5t/LocalStorage/Photos: Local storage path does not exist "/onetouch5t/LocalStorage/Photos/"
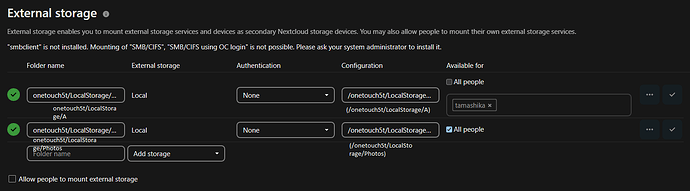
Here is a picture showing how I mounted my folders in ntfs drive:
Could someone tell me what the error means and how to fix it? Thanks.
My config.php file:
<?php
$CONFIG = array (
'memcache.local' => '\\OC\\Memcache\\APCu',
'apps_paths' =>
array (
0 =>
array (
'path' => '/var/www/html/apps',
'url' => '/apps',
'writable' => false,
),
1 =>
array (
'path' => '/var/www/html/custom_apps',
'url' => '/custom_apps',
'writable' => true,
),
),
'memcache.distributed' => '\\OC\\Memcache\\Redis',
'memcache.locking' => '\\OC\\Memcache\\Redis',
'redis' =>
array (
'host' => 'redis',
'password' => '',
'port' => 6379,
),
'upgrade.disable-web' => true,
'instanceid' => 'removed',
'passwordsalt' => 'removed',
'secret' => 'removed',
'trusted_domains' =>
array (
0 => 'removed',
),
'datadirectory' => '/var/www/html/data',
'dbtype' => 'sqlite3',
'version' => '30.0.1.2',
'overwrite.cli.url' => 'https://removed',
'installed' => true,
'memories.db.triggers.fcu' => true,
'memories.exiftool' => '/var/www/html/custom_apps/memories/bin-ext/exiftool-aarch64-musl',
'memories.vod.path' => '/var/www/html/custom_apps/memories/bin-ext/go-vod-aarch64',
'preview_max_x' => 2048,
'preview_max_y' => 2048,
'jpeg_quality' => '60',
'maintenance' => false,
'loglevel' => 3,
'enabledPreviewProviders' =>
array (
),
);