Originally published at: Encryption in Nextcloud - Nextcloud
Providing strong protection of data is the biggest benefit Nextcloud has over public clouds. Self-hosting means you are in control over your data. Of course, un-authorized access has to be stopped and this is where encryption comes in. In this blog post we’ll discuss the different types and layers of encryption used by Nextcloud to keep your data safe. We will discuss the threats the different kinds of encryption are designed to protect against, aiding system administrators in defining their threat model and taking the appropriate security measures. See our website for more about security and encryption.
What is encryption?
Encrypting data means mashing it up in a way that makes it nearly impossible for somebody else to read it without a secret token called the encryption key. A simple example is the Caesar cipher: just shift every letter in the alphabet a fixed number of characters. Say you choose 3. An A then becomes a D, a B becomes an E and so on. A message like meet me now becomes phhw ph qrz. Unless you know how many letters to shift, that is, the key (3 in this case) it is very hard to find out the content of the message.
Modern encryption is far more complicated than that, using mathematical tricks to make it extremely hard to break. You can learn more about those techniques on this Wikipedia page.
What is Threat Modelling?
Thread Modelling is the process of determining what threats are relevant and need to be protected against. It is used by system administrators to ensure their systems are correctly configured and provide adequate protection without unduly burdening users with overly complicated security hurdles.
Let’s give an example. Say you want to protect your car. Without asking “from what”, you might make the wrong decisions. Even a thick wall and a canal around your house with crocodiles, while probably effective against burglary, wouldn’t protect the car against heavy hail, something a simple roof would have done.
Of course, in an IT environment, you have multiple types of data. From customer data and fiscal year reports to the photos from last year’s Christmas party. While the latter could be embarrassing, generally speaking one could expect a draft fiscal year report in an enterprise traded on the stock exchange to require a greater degree of protection. Ideally even IT staff should not be able to access some of these files!
A simple approach to threat modelling is asking yourself: “what do I want to protect myself from?” Think of an imaginary attacker and think what they could do to breach your security. Then find solutions for the approaches you found. A formalized version of this approach is using ‘attack trees’ which was invented by security expert Bruce Schneider. You see an example attack tree for a virus attack here:
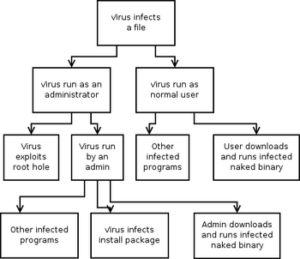
See the wikipedia page about threat modelling for more details and some history, and check this page about attack trees.
Encryption in Nextcloud
Nextcloud offers multiple layers of encryption for your data. First, data is protected when being transferred between clients and servers as well as between servers. Second, data can be encrypted on storage; and last but not least, we offer end-to-end encryption in the clients.
Each has their place and offers a different kind of protection, suitable to protect from a specific type of threat. We will describe each type of encryption and what it protects against.

Encryption during data transfer
Transfer encryption used by Nextcloud secures the connections between servers and clients. This uses standard TLS, a secure communication protocol used by HTTPS. HTTPS is what makes the lock in your browser address bar turn green! It is configured in the webserver, like Apache or NGINX, and our manual contains some instructions here. We strongly recommend to always use Nextcloud with TLS and we’ll warn system administrators strongly if it is not turned on.
Threat model

Nextcloud uses ‘plain and simple’ HTTP traffic for all file handling, which can be protected with TLS. TLS protects against attempts to capture data in transit between the server and client. It does not protect against a hacked device or server, but prevents data transfers on insecure networks like public WiFi networks, mobile devices or third party networks from being intercepted and is thus invaluable for a Nextcloud deployment.
Storage encryption
The Nextcloud Server Side Encryption feature provides secure storage of data by encrypting each file with a unique file key before it is stored. File keys are encrypted, in turn, either by a server wide key (default for feature and performance reasons) or a per-user key. Server Side Encryption provides protection for data on external storage as the files are encrypted before they are sent to storage and the keys never leave the Nextcloud server.
A server-wide key stores a server password in the Nextcloud data directory and uses it to decrypt the server key in the users’ data directory, which in turn is used to decrypt data.
When using per-user keys, the key in the data directory is per user and encrypted with the user password. We take great care to ensure keys never enter storage but keys will be kept in memory on the Nextcloud server for the duration of user login sessions to facilitate decryption and encryption of data.
Note that the Nextcloud desktop synchronization clients check for updates every 30 seconds, frequently and predictably providing a window for a malicious server administrator or hacker to steal the keys from the user session!
And note that Server Side Encryption only encrypts the content of files, not their name or folder structure. Using object storage like S3 works around this limitation as that type of storage back-end never leaks file or folder names.
Also note that when external storage is not used and a server-wide key is used, storing the encryption keys together with the data means little protection is afforded in cases the drives are stolen. For this threat model, a full-disk-encryption technology is often a better choice than the built-in Server Side Encryption in Nextcloud. dm-crypt, eCryptFS and EncFS tend to be good choices on the server, also allowing modern encryption acceleration features in CPU’s and operating systems to be used.
Learn more about Server-side encryption on our storage page.
Threat model
Server Side Encryption protects data on storage as long as that storage is not on the same server as Nextcloud itself.
Per-user keys only offer additional protection over a server-wide key in the case of physical theft of the Nextcloud server and storage or a security breach of the sever provided the user(s) do NOT log in for the duration of the breach. A full, undetected Nextcloud server breach by skilled attackers or malicious server administrator still risks exposing user data.
Client side end-to-end encryption
The ultimate protection of user data is provided by end-to-end Encryption. The Nextcloud end-to-end encryption feature is designed such that the server never has access to unencrypted files or keys, nor does server-provided code ever handle unencrypted data which could provide avenues for compromise.
Nextcloud makes end-to-end encryption very easy to use, seamlessly handling key exchange by the server without leaking any data and facilitating easy sharing with other users and collaboration. However, it comes with a feature loss as any type of online file editing and access to encrypted data as well as public sharing and sharing to groups is not possible for data in folders that are end-to-end encrypted.
Users can activate the Nextcloud end-to-end encryption feature for one or more folders. The content of each of these folders will be fully hidden from the server, including file names and directory structure. To sync the data with other devices, users have to enter a code created by the first device. Once that is done, end-to-end encrypted folders are seamlessly synced between devices. Users can share encrypted folders with other users on their server without any need for re-encrypting and re-uploading the data or having to enter passwords for either sender or recipient.
Cryptographic Identity Protection in the form of server signed certificates and a Trust On First Use (TOFU) model protects against attackers trying to impersonate other users. Nextcloud supports an optional offline administrator recovery key and allows a complete audit log. Enterprises can optionally employ a secure HSM to to issue certificates to users.
Nextcloud File Access Control can be employed to enforce end-to-end encryption in Nextcloud based on set criteria, for example group membership of users, file extension, size and more. This way, a sub-set of sensitive data can be afforded the highest level of protection while other data and users can continue to benefit from the easy public file exchange and online collaboration capabilities of Nextcloud.
As an example, Nextcloud enables a system administrator to ensure that all files created by the Finance department have to be end-to-end encrypted while other departments can collaborate and share to their hearts’ desire.
Note that the very nature of end-to-end encryption means there is no access to data through the web interface, nor any public sharing. This is because a browser would need to decrypt the files locally for the user to see them, but the code to do that has to come in the form of javascript from the server. This would break the trust model: End-to-end encryption is meant to protect from the server and thus one can’t trust the code from the server to decrypt the data and not sent a copy of the secure key to a third party server. This is more extensively discussed in an article from the security experts at the NCC Group. End-to-end schemes that have a browser component are no more secure than server-side encryption, which is why we recommend using instead if access through a browser is needed.
Learn more about End-to-end Encryption on our website. Note that as of August 2020, end-to-end encryption is available on the latest releases of the desktop and mobile clients. It requires Nextcloud server 19 with version 1.5.2 or version 20 with 1.6.1. Sharing between users is not yet implemented and on the roadmap for 2021.
Threat model
End-to-end Encryption in Nextcloud is designed to protect user data against any attack scenario between user devices, even in case of a undetected, long-term security breach or against untrusted server administrators.
It does not protect the data on user devices themselves and theft of an unencrypted, unlocked user device would enable an attacker to get access to private keys.
Conclusion
Encryption is used by Nextcloud to protect your data in transit and on external storage – and with End-to-end Encryption even against an untrusted server. When setting up a self-hosted file sync and share solution, it is wise to develop a threat model, determining clearly what threats the server should protect against, and then configuring the server environment to ensure protection against the identified threats. This blog post should then help choose the correct type(s) of encryption to employ to achieve the desired level of protection.


