Nextcloud version (eg, 29.0.5): 28.0.10(?) NextcloudPi v1.55.2
Operating system and version (eg, Ubuntu 24.04): nextcloudpi
Apache or nginx version (eg, Apache 2.4.25): nextcloudpi
PHP version (eg, 8.3): nextcloudpi
The issue you are facing:
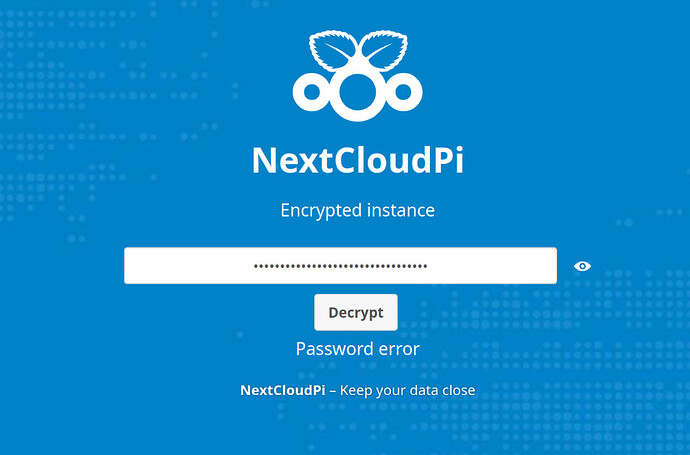
I’ve encrypted my local nextcloudpi installation, and normally I just past the password after an outage; the disk is then decrypted and I can access nextcloud. However, this time, after a short power outage, I get a “Password error”.
I am pretty sure the password is correct, as it has been in the password manager, which does not indicate any changes in its history.
Is there any way how I can manually decrypt or debug this?
Is this the first time you’ve seen this error? (Y/N): Y
Steps to replicate it:
- Pull the power plug of the raspberry pi; reconnect power a few seconds later.
- Access https://. A page “NextCloudPi Encrypted instance” pops up.
- paste the password into the password field. Click “Decrypt” button.
- Error message appears under the “Decrypt” button: “Password error”.
The output of your Nextcloud log in Admin > Logging:
can’t get this at this stage ![]()
The output of your config.php file in /path/to/nextcloud (make sure you remove any identifiable information!):
Can’t get this at this stage
The output of your Apache/nginx/system log in /var/log/____:
Can’t get this at this stage
Output errors in nextcloud.log in /var/www/ or as admin user in top right menu, filtering for errors. Use a pastebin service if necessary.
Can’t get this at this stage
In /var/log/ncp.log, I get:
[ nc-encrypt ] (Mon Oct 28 07:28:05 GMT 2024)
ESC[0;1;31mFailed to start transient service unit: Invalid environment block.ESC[0m