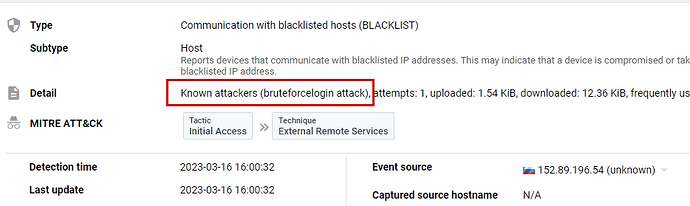
Starting March 10th '23 I started to notice systematic brute force and other attacks coming into my externally published NC.
The source of the attacks has been from IP address 152.89.196.54. You can see some of the evidence here (the last attack yesterday):
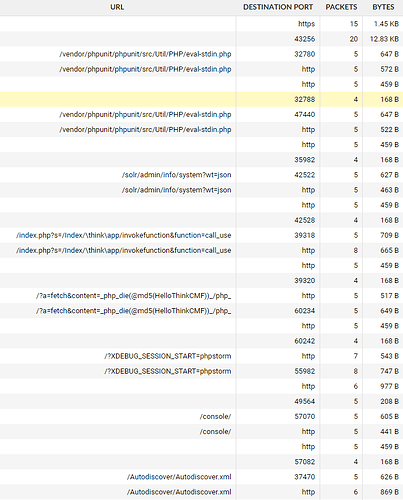
You can see the various attacks here:
I’ve blocked the IP on my border FW, but thought you’d enjoy seeing the types of attempts. I’ll note, the service-chain to get to NC is FW <> ADC w/WAF <> NC w/bruteforce, fail2ban, etc.
Hope this helps,
Andy
ernolf
March 17, 2023, 8:02pm
2
aredman:
Starting March 10th '2
Same pattern here since March 9th '23
“background noise”
1 Like
Fancy that … yes, background noise
1 Like
bb77
March 18, 2023, 9:02am
4
Yes, this is the usual noise when you expose things on the Internet. Btw. they visited me too…
152.89.196.54 - - [17/Mar/2023:23:26:28 +0100] "GET /actuator/gateway/routes HTTP/1.1" 404 360 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36" ┤
152.89.196.54 - - [18/Mar/2023:09:02:10 +0100] "GET /?XDEBUG_SESSION_START=phpstorm HTTP/1.1" 404 6299 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.108 Safari/537.36"
Alas … threat actors. Fortunately, NC is a fantastic solution with native protection against so many threats