Nextcloud version: 24.0.5
Operating system and version: Ubuntu 20 LTS
Apache or nginx version: nginx/1.18.0 (Ubuntu)
PHP version (eg, 7.4): PHP 8.1.10 (cli) (built: Sep 18 2022 10:25:43) (NTS) FPM
The issue you are facing:
When creating files, this message pops up:
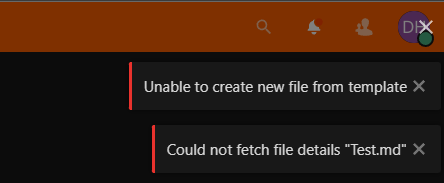
Unable to create new file from template
Could not fetch file details "Test.md"
Could not create folder "Testt"
There is also a problem sending files. If I refresh the page, the file is visible so it loads correctly.
Is this the first time you’ve seen this error? _(Y/N): Y
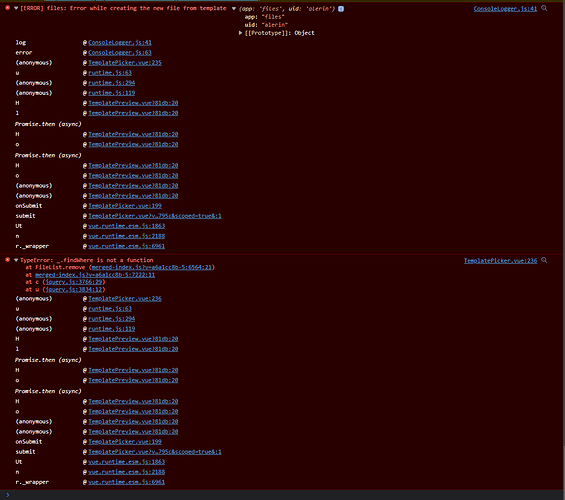
The output of your Nextcloud log in Admin > Logging:
Console log:
ConsoleLogger.js:41
[ERROR] files: Error while creating the new file from template
{app: 'files', uid: 'alerin'}
app
:
"files"
uid
:
"alerin"
[[Prototype]]
:
Object
log @ ConsoleLogger.js:41
error @ ConsoleLogger.js:63
(anonymous) @ TemplatePicker.vue:235
u @ runtime.js:63
(anonymous) @ runtime.js:294
(anonymous) @ runtime.js:119
H @ TemplatePreview.vue?81db:20
l @ TemplatePreview.vue?81db:20
Promise.then (async)
H @ TemplatePreview.vue?81db:20
o @ TemplatePreview.vue?81db:20
Promise.then (async)
H @ TemplatePreview.vue?81db:20
o @ TemplatePreview.vue?81db:20
(anonymous) @ TemplatePreview.vue?81db:20
(anonymous) @ TemplatePreview.vue?81db:20
onSubmit @ TemplatePicker.vue:199
submit @ TemplatePicker.vue?v…795c&scoped=true&:1
Ut @ vue.runtime.esm.js:1863
n @ vue.runtime.esm.js:2188
r._wrapper @ vue.runtime.esm.js:6961
TemplatePicker.vue:236
TypeError: _.findWhere is not a function
at FileList.remove (merged-index.js?v=a6a1cc8b-5:6564:21)
at merged-index.js?v=a6a1cc8b-5:7222:11
at c (jquery.js:3766:29)
at u (jquery.js:3834:12)
(anonymous) @ TemplatePicker.vue:236
u @ runtime.js:63
(anonymous) @ runtime.js:294
(anonymous) @ runtime.js:119
H @ TemplatePreview.vue?81db:20
l @ TemplatePreview.vue?81db:20
Promise.then (async)
H @ TemplatePreview.vue?81db:20
o @ TemplatePreview.vue?81db:20
Promise.then (async)
H @ TemplatePreview.vue?81db:20
o @ TemplatePreview.vue?81db:20
(anonymous) @ TemplatePreview.vue?81db:20
(anonymous) @ TemplatePreview.vue?81db:20
onSubmit @ TemplatePicker.vue:199
submit @ TemplatePicker.vue?v…795c&scoped=true&:1
Ut @ vue.runtime.esm.js:1863
n @ vue.runtime.esm.js:2188
r._wrapper @ vue.runtime.esm.js:6961
The output of your config.php file in /path/to/nextcloud (make sure you remove any identifiable information!):
<?php
$CONFIG = array (
'datadirectory' => '/home/cloud/data',
'dbtype' => 'mysql',
'version' => '24.0.5.1',
'overwrite.cli.url' => '',
'dbname' => 'cloud',
'dbhost' => 'localhost',
'dbport' => '',
'dbtableprefix' => 'oc_',
'mysql.utf8mb4' => true,
'dbuser' => 'cloud',
'dbpassword' => '',
'installed' => true,
'maintenance' => false,
'theme' => '',
'loglevel' => 2,
'default_phone_region' => 'PL',
'filelocking.enabled' => true,
'memcache.distributed' => '\\OC\\Memcache\\Redis',
'memcache.locking' => '\\OC\\Memcache\\Redis',
'memcache.local' => '\\OC\\Memcache\\Redis',
'redis' =>
array (
'host' => '127.0.0.1',
'port' => 6379,
),
'app_install_overwrite' =>
array (
0 => 'integration_whiteboard',
),
);
PHP config:
date.timezone = Europe/Warsaw
memory_limit = 512M
upload_max_filesize = 1G
post_max_size = 1G
max_execution_time = 300
opcache.memory_consumption = 512
opcache.interned_strings_buffer = 64
opcache.max_accelerated_files = 50000
opcache.max_wasted_percentage = 15
opcache.save_comments = 1
opcache.revalidate_freq = 60
opcache.validate_timestamps = 0
opcache.fast_shutdown=1
Nginx:
upstream php-handler {
server unix:/var/run/php/php8.1-fpm.sock;
}
server {
listen 80;
listen [::]:80;
server_name
# Enforce HTTPS
return 301 https://$server_name$request_uri;
}
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name
ssl_certificate /etc/ssl/cloud.pem;
ssl_certificate_key /etc/ssl/cloud.key;
root /home/cloud;
# HSTS settings
# WARNING: Only add the preload option once you read about
# the consequences in https://hstspreload.org/. This option
# will add the domain to a hardcoded list that is shipped
# in all major browsers and getting removed from this list
# could take several months.
add_header Strict-Transport-Security "max-age=15768000; includeSubDomains; preload;" always;
# set max upload size
client_max_body_size 1G;
fastcgi_buffers 64 4K;
# Enable gzip but do not remove ETag headers
gzip on;
gzip_vary on;
gzip_comp_level 4;
gzip_min_length 256;
gzip_proxied expired no-cache no-store private no_last_modified no_etag auth;
gzip_types application/atom+xml application/javascript application/json application/ld+json application/manifest+json application/rss+xml application/vnd.geo+json application/vnd.ms-fontobject application/x-font-ttf application/x-web-app-manifest+json application/xhtml+xml application/xml font/opentype image/bmp image/svg+xml image/x-icon text/cache-manifest text/css text/plain text/vcard text/vnd.rim.location.xloc text/vtt text/x-component text/x-cross-domain-policy;
# Pagespeed is not supported by Nextcloud, so if your server is built
# with the `ngx_pagespeed` module, uncomment this line to disable it.
#pagespeed off;
# HTTP response headers borrowed from Nextcloud `.htaccess`
add_header Referrer-Policy "no-referrer" always;
add_header X-Content-Type-Options "nosniff" always;
add_header X-Download-Options "noopen" always;
add_header X-Frame-Options "SAMEORIGIN" always;
add_header X-Permitted-Cross-Domain-Policies "none" always;
add_header X-Robots-Tag "none" always;
add_header X-XSS-Protection "1; mode=block" always;
# Remove X-Powered-By, which is an information leak
fastcgi_hide_header X-Powered-By;
# Path to the root of your installation
# Specify how to handle directories -- specifying `/index.php$request_uri`
# here as the fallback means that Nginx always exhibits the desired behaviour
# when a client requests a path that corresponds to a directory that exists
# on the server. In particular, if that directory contains an index.php file,
# that file is correctly served; if it doesn't, then the request is passed to
# the front-end controller. This consistent behaviour means that we don't need
# to specify custom rules for certain paths (e.g. images and other assets,
# `/updater`, `/ocm-provider`, `/ocs-provider`), and thus
# `try_files $uri $uri/ /index.php$request_uri`
# always provides the desired behaviour.
index index.php index.html /index.php$request_uri;
# Rule borrowed from `.htaccess` to handle Microsoft DAV clients
location = / {
if ( $http_user_agent ~ ^DavClnt ) {
return 302 /remote.php/webdav/$is_args$args;
}
}
location = /robots.txt {
allow all;
log_not_found off;
access_log off;
}
rewrite ^/\.well-known/carddav https://$server_name/remote.php/dav/ permanent;
rewrite ^/\.well-known/caldav https://$server_name/remote.php/dav/ permanent;
# Make a regex exception for `/.well-known` so that clients can still
# access it despite the existence of the regex rule
# `location ~ /(\.|autotest|...)` which would otherwise handle requests
# for `/.well-known`.
location ^~ /.well-known {
# The rules in this block are an adaptation of the rules
# in `.htaccess` that concern `/.well-known`.
location = /.well-known/carddav { return 301 /remote.php/dav/; }
location = /.well-known/caldav { return 301 /remote.php/dav/; }
location /.well-known/acme-challenge { try_files $uri $uri/ =404; }
location /.well-known/pki-validation { try_files $uri $uri/ =404; }
# Let Nextcloud's API for `/.well-known` URIs handle all other
# requests by passing them to the front-end controller.
return 301 /index.php$request_uri;
}
# Rules borrowed from `.htaccess` to hide certain paths from clients
location ~ ^/(?:build|tests|config|lib|3rdparty|templates|data)(?:$|/) { return 404; }
location ~ ^/(?:\.|autotest|occ|issue|indie|db_|console) { return 404; }
# Ensure this block, which passes PHP files to the PHP process, is above the blocks
# which handle static assets (as seen below). If this block is not declared first,
# then Nginx will encounter an infinite rewriting loop when it prepends `/index.php`
# to the URI, resulting in a HTTP 500 error response.
location ~ \.php(?:$|/) {
# Required for legacy support
rewrite ^/(?!index|remote|public|cron|core\/ajax\/update|status|ocs\/v[12]|updater\/.+|oc[ms]-provider\/.+|.+\/richdocumentscode\/proxy) /index.php$request_uri;
fastcgi_split_path_info ^(.+?\.php)(/.*)$;
set $path_info $fastcgi_path_info;
try_files $fastcgi_script_name =404;
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
fastcgi_param PATH_INFO $path_info;
fastcgi_param HTTPS on;
fastcgi_param modHeadersAvailable true; # Avoid sending the security headers twice
fastcgi_param front_controller_active true; # Enable pretty urls
fastcgi_pass php-handler;
fastcgi_intercept_errors on;
fastcgi_request_buffering off;
fastcgi_max_temp_file_size 0;
}
location ~ \.(?:css|js|svg|gif|map)$ {
try_files $uri /index.php$request_uri;
expires 6M; # Cache-Control policy borrowed from `.htaccess`
access_log off; # Optional: Don't log access to assets
}
location ~ \.woff2?$ {
try_files $uri /index.php$request_uri;
expires 7d; # Cache-Control policy borrowed from `.htaccess`
access_log off; # Optional: Don't log access to assets
}
# Rule borrowed from `.htaccess`
location /remote {
return 301 /remote.php$request_uri;
}
location / {
try_files $uri $uri/ /index.php$request_uri;
}
}
apps list:
Enabled:
- accessibility: 1.10.0
- activity: 2.16.0
- bruteforcesettings: 2.4.0
- calendar: 3.5.0
- circles: 24.0.1
- cloud_federation_api: 1.7.0
- comments: 1.14.0
- contacts: 4.2.1
- contactsinteraction: 1.5.0
- dashboard: 7.4.0
- dav: 1.22.0
- deck: 1.7.1
- event_update_notification: 1.5.0
- extract: 1.3.5
- federatedfilesharing: 1.14.0
- federation: 1.14.0
- files: 1.19.0
- files_linkeditor: 1.1.11
- files_pdfviewer: 2.5.0
- files_rightclick: 1.3.0
- files_sharing: 1.16.2
- files_trashbin: 1.14.0
- files_versions: 1.17.0
- files_videoplayer: 1.13.0
- firstrunwizard: 2.13.0
- flow_notifications: 1.4.0
- forms: 2.5.1
- integration_whiteboard: 0.0.14
- logreader: 2.9.0
- lookup_server_connector: 1.12.0
- mail: 1.13.8
- maps: 0.2.1
- metadata: 0.16.0
- nextcloud_announcements: 1.13.0
- notes: 4.5.1
- notifications: 2.12.1
- oauth2: 1.12.0
- password_policy: 1.14.0
- photos: 1.6.0
- polls: 3.8.0
- privacy: 1.8.0
- provisioning_api: 1.14.0
- recommendations: 1.3.0
- richdocuments: 6.2.0
- serverinfo: 1.14.0
- settings: 1.6.0
- sharebymail: 1.14.0
- socialsharing_email: 2.5.0
- spreed: 14.0.5
- support: 1.7.0
- survey_client: 1.12.0
- systemtags: 1.14.0
- talk_matterbridge: 1.25.2
- tasks: 0.14.4
- text: 3.5.1
- theming: 1.15.0
- transfer: 0.6.0
- twofactor_backupcodes: 1.13.0
- updatenotification: 1.14.0
- user_status: 1.4.0
- viewer: 1.8.0
- weather_status: 1.4.0
- workflowengine: 2.6.0
Disabled:
- admin_audit
- encryption
- files_external
- user_ldap
Additional logs that were created at a similar time:
{“reqId”:“B3MuajRlEc2H1kzQRTvH”,“level”:3,“time”:“2022-09-20T01:07:25+00:00”,"re - Pastebin.com