@enoch85
This is my step by step guide for you.
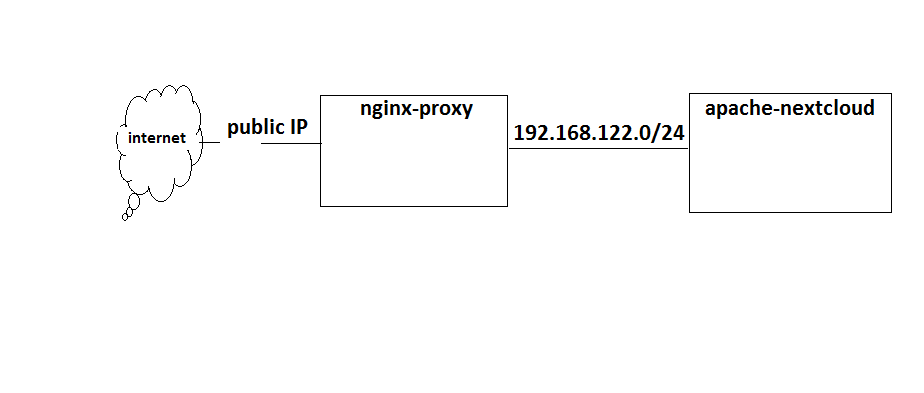
The structure of the network:
nginx-proxy
apt-get install letsencrypt nginx
gen cert:
letsencrypt --standalone certonly -d cloud.viop.pl
new file: /etc/nginx/sites-available/cloud.viop.pl
server {
listen 80;
server_name cloud.viop.pl;
return 301 https://$server_name$request_uri;
access_log /var/log/nginx/access.log;
}
server {
listen 443;
server_name cloud.viop.pl;
# LetsEncrypt
location ~ /.well-known {
allow all;
root /var/www/html;
}
# NextCloud
location / {
proxy_pass https://192.168.122.236/;
include /etc/nginx/proxy_params;
}
location ^~ /loleaflet {
proxy_pass https://192.168.122.236:9980;
proxy_set_header Host $http_host;
}
location ^~ /hosting/discovery {
proxy_pass https://192.168.122.236:9980;
proxy_set_header Host $http_host;
}
location ^~ /lool {
proxy_pass https://192.168.122.236:9980;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_set_header Host $http_host;
}
}
a small change in the config
--- a/etc/nginx/sites-available/default
+++ b/etc/nginx/sites-available/default
@@ -19,7 +19,9 @@ server {
# SSL configuration
#
- # listen 443 ssl default_server;
+ listen 443 ssl default_server;
+ ssl_certificate /etc/letsencrypt/live/cloud.viop.pl/fullchain.pem;
+ ssl_certificate_key /etc/letsencrypt/live/cloud.viop.pl/privkey.pem;
# listen [::]:443 ssl default_server;
#
# Note: You should disable gzip for SSL traffic.
apache-nextcloud
install some shits
apt-get install apache2 mariadb-server libapache2-mod-php php-gd php-json php-mysql php-curl php-intl php-mcrypt php-imagick php-mbstring php-xml php-zip
Install nextcloud + collabora
cd /tmp/
wget https://download.nextcloud.com/server/releases/nextcloud-10.0.1.tar.bz2
tar -jxvf nextcloud-10.0.1.tar.bz2 -C /var/www/
wget https://apps.owncloud.com/CONTENT/content-files/174727-richdocuments.zip
unzip 174727-richdocuments.zip -d /var/www/nextcloud/apps/
chown -R www-data:www-data /var/www/nextcloud/
Install docker:
apt-get install docker.io
docker pull collabora/code
docker run -t -d -p 192.168.122.236:9980:9980 -e 'domain=cloud\\.viop\\.pl' --restart always --cap-add MKNOD collabora/code
Database
mysql -uroot
CREATE DATABASE nextcloud;
GRANT ALL PRIVILEGES ON nextcloud.* TO 'nxuser'@'localhost' IDENTIFIED BY 'nextcloud';
self-signed cert:
mkdir /etc/apache2/ssl/
openssl req -x509 -subj "/C=EU/ST=Internet/L=Intranet/O=ViOP/CN=cloud.viop.pl" -nodes -days 3650 -newkey rsa:2048 -keyout /etc/apache2/ssl/apache.key -out /etc/apache2/ssl/apache.crt
cp /etc/apache2/ssl/apache.crt /usr/share/ca-certificates/apache.crt
update-ca-certificates --fresh
new file: /etc/apache2/sites-available/cloud.viop.pl.conf
<VirtualHost 192.168.122.236:443>
ServerName cloud.viop.pl:443
<IfModule mod_headers.c>
Header always set Strict-Transport-Security "max-age=15768000; includeSubDomains; preload"
</IfModule>
DocumentRoot "/var/www/nextcloud"
<Directory /var/www/nextcloud/>
Options +FollowSymlinks
AllowOverride All
Order allow,deny
Allow from all
<IfModule mod_dav.c>
Dav off
</IfModule>
SetEnv HOME /var/www/nextcloud
SetEnv HTTP_HOME /var/www/nextcloud
</Directory>
# SSL configuration, you may want to take the easy route instead and use Lets Encrypt!
SSLEngine on
SSLCertificateFile /etc/apache2/ssl/apache.crt
# SSLCertificateChainFile /path/to/intermediate_certificate
SSLCertificateKeyFile /etc/apache2/ssl/apache.key
SSLProtocol all -SSLv2 -SSLv3
SSLCipherSuite ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:ECDHE-ECDSA-DES-CBC3-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:DES-CBC3-SHA:!DSS
SSLHonorCipherOrder on
# Encoded slashes need to be allowed
AllowEncodedSlashes On
# Container uses a unique non-signed certificate
SSLProxyEngine On
SSLProxyVerify None
SSLProxyCheckPeerCN Off
SSLProxyCheckPeerName Off
# keep the host
ProxyPreserveHost On
# static html, js, images, etc. served from loolwsd
# loleaflet is the client part of LibreOffice Online
ProxyPass /loleaflet https://192.168.122.236:9980/loleaflet retry=0
ProxyPassReverse /loleaflet https://192.168.122.236:9980/loleaflet
# WOPI discovery URL
ProxyPass /hosting/discovery https://192.168.122.236:9980/hosting/discovery retry=0
ProxyPassReverse /hosting/discovery https://192.168.122.236:9980/hosting/discovery
# Main websocket
ProxyPassMatch "/lool/(.*)/ws$" wss://192.168.122.236:9980/lool/$1/ws
# Admin Console websocket
ProxyPass /lool/adminws wss://192.168.122.236:9980/lool/adminws
# Download as, Fullscreen presentation and Image upload operations
ProxyPass /lool https://192.168.122.236:9980/lool
ProxyPassReverse /lool https://192.168.122.236:9980/lool
</VirtualHost>
enable mods:
a2enmod proxy
a2enmod proxy_wstunnel
a2enmod proxy_http
a2enmod ssl
a2enmod headers
a2ensite cloud.viop.pl
service apache2 restart
Open https://cloud.viop.pl
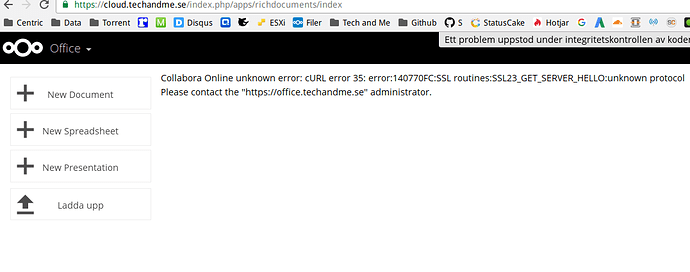
go to admin → apps → not enabled
scroll down and enable Collabora Online
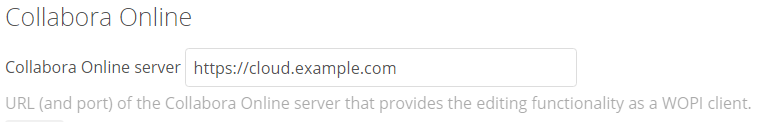
now go to admin → Additional setting
In Collabora Online server put https://cloud.viop.pl
It works for me