So I use this docker compose file.
version: '3'
services:
db:
image: postgres:12.9-alpine
restart: always
volumes:
- db:/var/lib/postgresql/data
env_file:
- db.env
redis:
image: redis:alpine
restart: always
# volumes:
# - ./redis.conf:/usr/local/etc/redis/redis.conf
# ports:
# - 6379:6379
networks:
- proxy-tier
- default
command: redis-server --requirepass nextcloud
app:
image: nextcloud:29.0.0-fpm-alpine
restart: always
volumes:
- nextcloud:/var/www/html
environment:
- POSTGRES_HOST=db
- REDIS_HOST=redis
- REDIS_HOST_PASSWORD=nextcloud
- REDIS_PORT=6379
- PHP_MEMORY_LIMIT=4096M
env_file:
- db.env
depends_on:
- db
networks:
- default
web:
build: ./web
restart: always
volumes:
- /var/run/docker.sock:/tmp/docker.sock:ro
#- /var/run/docker.sock:/var/run/docker.sock:ro
- nextcloud:/var/www/html:ro
- php-config:/usr/local/etc/php
environment:
- VIRTUAL_HOST=nextcloud.mysite.net
- LETSENCRYPT_HOST=nextcloud.mysite.net
- LETSENCRYPT_EMAIL=dns@mysite.net
depends_on:
- app
networks:
- proxy-tier
- default
cron:
image: nextcloud:fpm-alpine
restart: always
volumes:
- nextcloud:/var/www/html
entrypoint: /cron.sh
depends_on:
- db
- redis
proxy:
build: ./proxy
restart: always
ports:
- 80:80
- 443:443
labels:
com.github.jrcs.letsencrypt_nginx_proxy_companion.nginx_proxy: "true"
volumes:
- certs:/etc/nginx/certs:ro
- vhost.d:/etc/nginx/vhost.d
- html:/usr/share/nginx/html
- /var/run/docker.sock:/tmp/docker.sock:ro
#- /var/run/docker.sock:/var/run/docker.sock:ro
networks:
- proxy-tier
letsencrypt-companion:
image: nginxproxy/acme-companion
restart: always
environment:
- NGINX_PROXY_CONTAINER=proxy
volumes:
- certs:/etc/nginx/certs
- acme:/etc/acme.sh
- vhost.d:/etc/nginx/vhost.d
- html:/usr/share/nginx/html
- /var/run/docker.sock:/var/run/docker.sock:ro
#- /var/run/docker.sock:/tmp/docker.sock:ro
networks:
- proxy-tier
depends_on:
- proxy
# self signed
# omgwtfssl:
# image: paulczar/omgwtfssl
# restart: "no"
# volumes:
# - certs:/certs
# environment:
# - SSL_SUBJECT=servhostname.local
# - CA_SUBJECT=my@example.com
# - SSL_KEY=/certs/servhostname.local.key
# - SSL_CSR=/certs/servhostname.local.csr
# - SSL_CERT=/certs/servhostname.local.crt
# networks:
# - proxy-tier
volumes:
db:
nextcloud:
certs:
acme:
vhost.d:
html:
php-config:
networks:
proxy-tier:
default:
And upgraded from 28.0.3 → 28.0.5 → 29.0.0
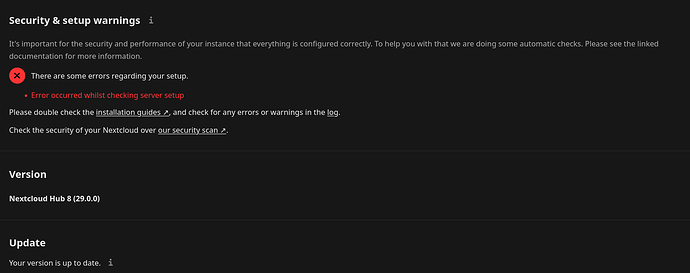
and several things are broken. First the setupchecks reveals this.
And the occ command gives this.
docker exec -it --user=www-data nextcloud_app_1 ./occ setupchecks -vv
dav:
✓ DAV system address book: No outstanding DAV system address book sync.
network:
✓ WebDAV endpoint: Your web server is properly set up to allow file synchronization over WebDAV.
✓ Data directory protected
✓ Internet connectivity
✓ JavaScript source map support
✗ JavaScript modules support: Your webserver does not serve `.mjs` files using the JavaScript MIME type. This will break some apps by preventing browsers from executing the JavaScript files. You should configure your webserver to serve `.mjs` files with either the `text/javascript` or `application/javascript` MIME type.
✓ OCS provider resolving
⚠ .well-known URLs: Your web server is not properly set up to resolve `.well-known` URLs, failed on:
`/.well-known/caldav`
✓ WOFF2 file loading
system:
⚠ Errors in the log: 933 errors in the logs since May 4, 2024, 4:15:02 AM
ℹ Brute-force Throttle: Your remote address could not be determined.
✓ Cron errors: The last cron job ran without errors.
✓ Cron last run: Last background job execution ran 4 minutes ago.
✓ Debug mode: Debug mode is disabled.
✓ File locking
✓ Maintenance window start: Maintenance window to execute heavy background jobs is between 3:00 UTC and 9:00 UTC
✓ Memcache: Configured
✓ Architecture: 64-bit
✓ Temporary space available: Temporary directory is correctly configured:
- 33.0 GiB available in /tmp (PHP temporary directory)
✓ Push service: Free push service
notifications:
✓ Push notifications - Fair use policy
security:
✓ App directories owner: App directories have the correct owner "www-data"
✓ Old administration imported certificates
✓ Code integrity: No altered files
ℹ Forwarded for headers: Your remote address could not be determined.
⚠ HTTPS access and URLs: You are accessing your instance over a secure connection, however your instance is generating insecure URLs. This most likely means that you are behind a reverse proxy and the overwrite config variables are not set correctly.
✓ Old server-side-encryption: Disabled
✓ PHP version: You are currently running PHP 8.2.18.
✓ Random generator: Secure
✓ HTTP headers: Your server is correctly configured to send security headers.
database:
✓ Database missing columns: None
✓ Database missing indices: None
✓ Database missing primary keys: None
✓ Database pending bigint migrations: None
✓ MySQL Unicode support: You are not using MySQL
✓ Database version: 12.9
✓ Database transaction isolation level: Read committed
config:
✓ Default phone region: GB
✓ Email test: Email test was successfully sent
✓ Overwrite CLI URL: The "overwrite.cli.url" option in your config.php is set to "http://nextcloud.locascio.org" which is a correct URL. Suggested URL is "https://localhost".
✓ Configuration file access rights: Nextcloud configuration file is writable
php:
✓ PHP default charset: UTF-8
✓ PHP set_time_limit: The function is available.
✓ Freetype: Supported
✓ PHP getenv
✓ PHP memory limit: 4 GB
✓ PHP modules
✗ PHP opcache: The PHP OPcache module is not properly configured. OPcache is not working as it should, opcache_get_status() returns false, please check configuration.
The maximum number of OPcache keys is nearly exceeded. To assure that all scripts can be kept in the cache, it is recommended to apply "opcache.max_accelerated_files" to your PHP configuration with a value higher than "32768".
The OPcache buffer is nearly full. To assure that all scripts can be hold in cache, it is recommended to apply "opcache.memory_consumption" to your PHP configuration with a value higher than "8192".
The OPcache interned strings buffer is nearly full. To assure that repeating strings can be effectively cached, it is recommended to apply "opcache.interned_strings_buffer" to your PHP configuration with a value higher than "4096"..
✓ PHP "output_buffering" option: Disabled
ℹ PHP Imagick module: The PHP module "imagick" in this instance has no SVG support. For better compatibility it is recommended to install it.
That first error Your webserver does not serve .mjs files using the JavaScript MIME type is bogus. When I run curl -I https://nextcloud.mysite.net/apps/settings/js/esm-test.mjs
It returns:
HTTP/2 200
server: nginx/1.21.3
date: Sun, 05 May 2024 09:07:47 GMT
content-type: application/octet-stream
content-length: 109
last-modified: Sat, 04 May 2024 10:49:33 GMT
etag: "663612bd-6d"
referrer-policy: no-referrer
x-content-type-options: nosniff
x-download-options: noopen
x-frame-options: SAMEORIGIN
x-permitted-cross-domain-policies: none
x-robots-tag: noindex,nofollow
x-xss-protection: 1; mode=block
accept-ranges: bytes
strict-transport-security: max-age=31536000
and even inside the container it shows this.
docker exec -it --user=www-data nextcloud_app_1 curl -I http://web/apps/settings/js/esm-test.mjs
HTTP/1.1 200 OK
Server: nginx/1.21.3
Date: Sun, 05 May 2024 09:09:25 GMT
Content-Type: application/octet-stream
Content-Length: 109
Last-Modified: Sat, 04 May 2024 10:49:33 GMT
Connection: keep-alive
ETag: "663612bd-6d"
Referrer-Policy: no-referrer
X-Content-Type-Options: nosniff
X-Download-Options: noopen
X-Frame-Options: SAMEORIGIN
X-Permitted-Cross-Domain-Policies: none
X-Robots-Tag: noindex,nofollow
X-XSS-Protection: 1; mode=block
Accept-Ranges: bytes
The MIME types are in the Nginx config.
./nginx -T
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
# configuration file /etc/nginx/nginx.conf:
worker_processes auto;
error_log /var/log/nginx/error.log warn;
pid /var/run/nginx.pid;
events {
worker_connections 1024;
}
http {
include /etc/nginx/mime.types;
default_type application/octet-stream;
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'$status $body_bytes_sent "$http_referer" '
'"$http_user_agent" "$http_x_forwarded_for"';
access_log /var/log/nginx/access.log main;
sendfile on;
#tcp_nopush on;
keepalive_timeout 65;
#gzip on;
upstream php-handler {
server app:9000;
}
server {
listen 80;
# HSTS settings
# WARNING: Only add the preload option once you read about
# the consequences in https://hstspreload.org/. This option
# will add the domain to a hardcoded list that is shipped
# in all major browsers and getting removed from this list
# could take several months.
#add_header Strict-Transport-Security "max-age=15768000; includeSubDomains; preload;" always;
# set max upload size
client_max_body_size 512M;
fastcgi_buffers 64 4K;
# Enable gzip but do not remove ETag headers
gzip on;
gzip_vary on;
gzip_comp_level 4;
gzip_min_length 256;
gzip_proxied expired no-cache no-store private no_last_modified no_etag auth;
gzip_types application/atom+xml application/javascript application/json application/ld+json application/manifest+json application/rss+xml application/vnd.geo+json application/vnd.ms-fontobject application/x-font-ttf application/x-web-app-manifest+json application/xhtml+xml application/xml font/opentype image/bmp image/svg+xml image/x-icon text/cache-manifest text/css text/plain text/vcard text/vnd.rim.location.xloc text/vtt text/x-component text/x-cross-domain-policy;
# Pagespeed is not supported by Nextcloud, so if your server is built
# with the `ngx_pagespeed` module, uncomment this line to disable it.
#pagespeed off;
# HTTP response headers borrowed from Nextcloud `.htaccess`
add_header Referrer-Policy "no-referrer" always;
add_header X-Content-Type-Options "nosniff" always;
add_header X-Download-Options "noopen" always;
add_header X-Frame-Options "SAMEORIGIN" always;
add_header X-Permitted-Cross-Domain-Policies "none" always;
add_header X-Robots-Tag "noindex,nofollow" always;
add_header X-XSS-Protection "1; mode=block" always;
# Remove X-Powered-By, which is an information leak
fastcgi_hide_header X-Powered-By;
# Path to the root of your installation
root /var/www/html;
# Specify how to handle directories -- specifying `/index.php$request_uri`
# here as the fallback means that Nginx always exhibits the desired behaviour
# when a client requests a path that corresponds to a directory that exists
# on the server. In particular, if that directory contains an index.php file,
# that file is correctly served; if it doesn't, then the request is passed to
# the front-end controller. This consistent behaviour means that we don't need
# to specify custom rules for certain paths (e.g. images and other assets,
# `/updater`, `/ocm-provider`, `/ocs-provider`), and thus
# `try_files $uri $uri/ /index.php$request_uri`
# always provides the desired behaviour.
index index.php index.html /index.php$request_uri;
# Rule borrowed from `.htaccess` to handle Microsoft DAV clients
location = / {
if ( $http_user_agent ~ ^DavClnt ) {
return 302 /remote.php/webdav/$is_args$args;
}
}
location = /robots.txt {
allow all;
log_not_found off;
access_log off;
}
# Make a regex exception for `/.well-known` so that clients can still
# access it despite the existence of the regex rule
# `location ~ /(\.|autotest|...)` which would otherwise handle requests
# for `/.well-known`.
location ^~ /.well-known {
# The rules in this block are an adaptation of the rules
# in `.htaccess` that concern `/.well-known`.
location = /.well-known/carddav { return 301 /remote.php/dav/; }
location = /.well-known/caldav { return 301 /remote.php/dav/; }
location /.well-known/acme-challenge { try_files $uri $uri/ =404; }
location /.well-known/pki-validation { try_files $uri $uri/ =404; }
# Let Nextcloud's API for `/.well-known` URIs handle all other
# requests by passing them to the front-end controller.
return 301 /index.php$request_uri;
}
# Rules borrowed from `.htaccess` to hide certain paths from clients
location ~ ^/(?:build|tests|config|lib|3rdparty|templates|data)(?:$|/) { return 404; }
location ~ ^/(?:\.|autotest|occ|issue|indie|db_|console) { return 404; }
# Ensure this block, which passes PHP files to the PHP process, is above the blocks
# which handle static assets (as seen below). If this block is not declared first,
# then Nginx will encounter an infinite rewriting loop when it prepends `/index.php`
# to the URI, resulting in a HTTP 500 error response.
location ~ \.php(?:$|/) {
# Required for legacy support
rewrite ^/(?!index|remote|public|cron|core\/ajax\/update|status|ocs\/v[12]|updater\/.+|oc[ms]-provider\/.+|.+\/richdocumentscode\/proxy) /index.php$request_uri;
fastcgi_split_path_info ^(.+?\.php)(/.*)$;
set $path_info $fastcgi_path_info;
try_files $fastcgi_script_name =404;
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
fastcgi_param PATH_INFO $path_info;
#fastcgi_param HTTPS on;
fastcgi_param modHeadersAvailable true; # Avoid sending the security headers twice
fastcgi_param front_controller_active true; # Enable pretty urls
fastcgi_pass php-handler;
fastcgi_intercept_errors on;
fastcgi_request_buffering off;
}
location ~ \.(?:css|js|svg|gif)$ {
try_files $uri /index.php$request_uri;
expires 6M; # Cache-Control policy borrowed from `.htaccess`
access_log off; # Optional: Don't log access to assets
}
location ~ \.woff2?$ {
try_files $uri /index.php$request_uri;
expires 7d; # Cache-Control policy borrowed from `.htaccess`
access_log off; # Optional: Don't log access to assets
}
# Rule borrowed from `.htaccess`
location /remote {
return 301 /remote.php$request_uri;
}
location / {
try_files $uri $uri/ /index.php$request_uri;
}
}
}
# configuration file /etc/nginx/mime.types:
types {
text/html html htm shtml;
text/css css;
text/xml xml;
image/gif gif;
image/jpeg jpeg jpg;
application/javascript js;
application/javascript mjs:
application/atom+xml atom;
application/rss+xml rss;
text/mathml mml;
text/plain txt;
text/vnd.sun.j2me.app-descriptor jad;
text/vnd.wap.wml wml;
text/x-component htc;
image/png png;
image/svg+xml svg svgz;
image/tiff tif tiff;
image/vnd.wap.wbmp wbmp;
image/webp webp;
image/x-icon ico;
image/x-jng jng;
image/x-ms-bmp bmp;
font/woff woff;
font/woff2 woff2;
application/java-archive jar war ear;
application/json json;
application/mac-binhex40 hqx;
application/msword doc;
application/pdf pdf;
application/postscript ps eps ai;
application/rtf rtf;
application/vnd.apple.mpegurl m3u8;
application/vnd.google-earth.kml+xml kml;
application/vnd.google-earth.kmz kmz;
application/vnd.ms-excel xls;
application/vnd.ms-fontobject eot;
application/vnd.ms-powerpoint ppt;
application/vnd.oasis.opendocument.graphics odg;
application/vnd.oasis.opendocument.presentation odp;
application/vnd.oasis.opendocument.spreadsheet ods;
application/vnd.oasis.opendocument.text odt;
application/vnd.openxmlformats-officedocument.presentationml.presentation
pptx;
application/vnd.openxmlformats-officedocument.spreadsheetml.sheet
xlsx;
application/vnd.openxmlformats-officedocument.wordprocessingml.document
docx;
application/vnd.wap.wmlc wmlc;
application/wasm wasm;
application/x-7z-compressed 7z;
application/x-cocoa cco;
application/x-java-archive-diff jardiff;
application/x-java-jnlp-file jnlp;
application/x-makeself run;
application/x-perl pl pm;
application/x-pilot prc pdb;
application/x-rar-compressed rar;
application/x-redhat-package-manager rpm;
application/x-sea sea;
application/x-shockwave-flash swf;
application/x-stuffit sit;
application/x-tcl tcl tk;
application/x-x509-ca-cert der pem crt;
application/x-xpinstall xpi;
application/xhtml+xml xhtml;
application/xspf+xml xspf;
application/zip zip;
application/octet-stream bin exe dll;
application/octet-stream deb;
application/octet-stream dmg;
application/octet-stream iso img;
application/octet-stream msi msp msm;
audio/midi mid midi kar;
audio/mpeg mp3;
audio/ogg ogg;
audio/x-m4a m4a;
audio/x-realaudio ra;
video/3gpp 3gpp 3gp;
video/mp2t ts;
video/mp4 mp4;
video/mpeg mpeg mpg;
video/quicktime mov;
video/webm webm;
video/x-flv flv;
video/x-m4v m4v;
video/x-mng mng;
video/x-ms-asf asx asf;
video/x-ms-wmv wmv;
video/x-msvideo avi;
}
# configuration file /etc/nginx/fastcgi_params:
fastcgi_param QUERY_STRING $query_string;
fastcgi_param REQUEST_METHOD $request_method;
fastcgi_param CONTENT_TYPE $content_type;
fastcgi_param CONTENT_LENGTH $content_length;
fastcgi_param SCRIPT_NAME $fastcgi_script_name;
fastcgi_param REQUEST_URI $request_uri;
fastcgi_param DOCUMENT_URI $document_uri;
fastcgi_param DOCUMENT_ROOT $document_root;
fastcgi_param SERVER_PROTOCOL $server_protocol;
fastcgi_param REQUEST_SCHEME $scheme;
fastcgi_param HTTPS $https if_not_empty;
fastcgi_param GATEWAY_INTERFACE CGI/1.1;
fastcgi_param SERVER_SOFTWARE nginx/$nginx_version;
fastcgi_param REMOTE_ADDR $remote_addr;
fastcgi_param REMOTE_PORT $remote_port;
fastcgi_param SERVER_ADDR $server_addr;
fastcgi_param SERVER_PORT $server_port;
fastcgi_param SERVER_NAME $server_name;
# PHP only, required if PHP was built with --enable-force-cgi-redirect
fastcgi_param REDIRECT_STATUS 200;
The other errors I read only happens becuase of the occ command not testing opcache correctly.
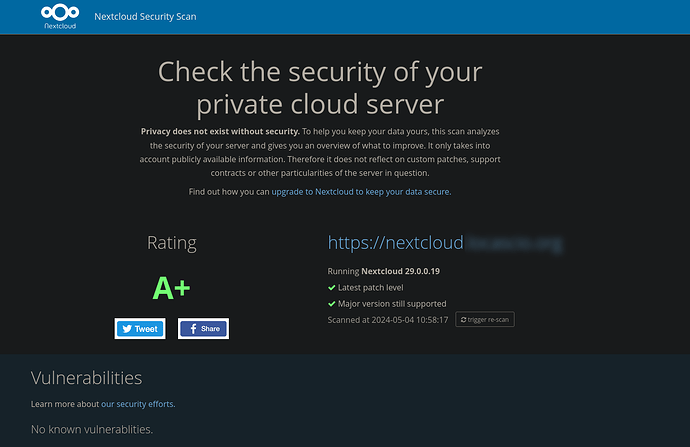
FWIW a external security check gives the server a rating of A+
So why is the check so broken with occ? The first error is bogus and the other errors shouold not be showing either.
How to go about debugging this?
TIA