There is also the nextcloud app “geoblocking”.
To confirm:
Any computer or device needs to translate the url (domain part) to an IP. When hitting that IP it hits on a port. Typically port 80 for HTTP (none encrypted) and port 443 HTTPS (TLS encryption). That will essentially hit a listenning webserver, which (skipping the three way handshake and goes stright to connection established) only at this point, looks at the header to extract the url requested by your browser. Essentially DNS is only translating a domain to an IP.
So:
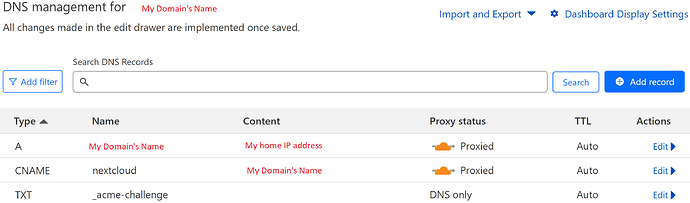
No matter where you are in the world, cloud.mydom.tld needs to translate into the IP that essentially points to your webserver. Outside your home network, this is your Public IP. This is handled by your registered name servers in the .tld registrant. This COULD be cloudflare, desec.io, opendns, whatever.
When you are on your LAN, your devices will try to ask the DNS server your devices is told to ask. If you have not setup a local DNS on your LAN, this will typically by forwarded to the DNS provider your ISP defines. However to hit LAN addresses, you will have to setup an internal DNS on your lan, which:
- Has A records for your “local” services like: cloud.mydom.tld A 192.168.1.x
- Has a forwarding pointer to an external DNS server for anything else: server 8.8.8.8 (google DNS)
Only other alternative is to add this to your local devices hosts file, however this is NOT recommendable for anything portable. Stationary devices never leaving your home: could be in the hosts file. Any other devices will suffer when you brings the device outside your LAN.
To keep it short:
If you use OpenWRT it has very good DNS server capabilities, including DNS intercept. If I am not mistaken, it is using dnsmasq? If so, all you have to do is to activate DNS intercept or define the OpenWRT server/host/routers LAN IP as appointet DNS in your DHCP settings. Up to you. But DNSMASQ “custom config”:
address=/cloud.mydom.tld/192.168.1.X
address=/www.mydom.tld/192.168.1.Y
address=/www.mydom2.tld/192.168.1.Z
server=8.8.8.8
server=8.8.4.4
For server= then add whatever public DNS server you trust. OpenDNS, DeSEC, Google or even one of the root DNS servers from iana.org
Now all devices - even guests - will always go straight to your LAN hosts based on domain names and for all other adresses besides those specifically listed in your dnsmasq config, will work as always.