I am trying to use the AIO docker image, I can see this screen:
When clicking on Open your Nextcloud I get this screen:
I tried to add port 8443, not working. Any idea, what would be the IP or PORT to login to nextcloud?
I am trying to use the AIO docker image, I can see this screen:
When clicking on Open your Nextcloud I get this screen:
I tried to add port 8443, not working. Any idea, what would be the IP or PORT to login to nextcloud?
Hi, are you running the image behind some kind of reverse proxy? Also, did you enter a domain or an ip-address into the input field?
Also, please click on Running next to Apache and post the logs here. Thanks!
Additionally, you should anonymize your Nextcloud password…
@szaimen I will delete this instance, it’s installed on my local computer just to test the new feature. So it’s really just my laptop, running Ubuntu and I followed the instruction in docker, but it’s not working. I don’t recall any input field to choose a domain or IP…
nc: getaddrinfo for host "nextcloud-aio-nextcloud" port 9000: Temporary failure in name resolution
Waiting for Nextcloud to start...
Waiting for Nextcloud to start...
Waiting for Nextcloud to start...
AH00558: apache2: Could not reliably determine the server's fully qualified domain name, using 172.17.0.8. Set the 'ServerName' directive globally to suppress this message
{"level":"info","ts":1638500701.9345636,"msg":"using provided configuration","config_file":"/Caddyfile","config_adapter":""}
{"level":"warn","ts":1638500701.9366195,"msg":"input is not formatted with 'caddy fmt'","adapter":"caddyfile","file":"/Caddyfile","line":2}
{"level":"info","ts":1638500701.938665,"logger":"admin","msg":"admin endpoint started","address":"tcp/localhost:2019","enforce_origin":false,"origins":["localhost:2019","[::1]:2019","127.0.0.1:2019"]}
{"level":"info","ts":1638500701.9388475,"logger":"http","msg":"server is listening only on the HTTPS port but has no TLS connection policies; adding one to enable TLS","server_name":"srv0","https_port":443}
{"level":"info","ts":1638500701.939411,"logger":"tls.cache.maintenance","msg":"started background certificate maintenance","cache":"0xc0003dde30"}
{"level":"info","ts":1638500701.9424183,"logger":"tls","msg":"cleaning storage unit","description":"FileStorage:/mnt/data/caddy"}
{"level":"info","ts":1638500701.9438741,"logger":"tls","msg":"finished cleaning storage units"}
{"level":"warn","ts":1638500701.9764314,"logger":"pki.ca.local","msg":"installing root certificate (you might be prompted for password)","path":"storage:pki/authorities/local/root.crt"}
2021/12/03 03:05:01 Warning: "certutil" is not available, install "certutil" with "apt install libnss3-tools" or "yum install nss-tools" and try again
2021/12/03 03:05:01 define JAVA_HOME environment variable to use the Java trust
{"level":"error","ts":1638500701.978375,"logger":"pki.ca.local","msg":"failed to install root certificate","error":"failed to execute tee: exit status 1","certificate_file":"storage:pki/authorities/local/root.crt"}
{"level":"info","ts":1638500701.9789207,"logger":"http","msg":"enabling automatic TLS certificate management","domains":["172.16.238.1"]}
{"level":"warn","ts":1638500701.979697,"logger":"tls","msg":"stapling OCSP","error":"no OCSP stapling for [172.16.238.1]: no OCSP server specified in certificate"}
{"level":"info","ts":1638500701.9799016,"msg":"autosaved config (load with --resume flag)","file":"/var/www/.config/caddy/autosave.json"}
{"level":"info","ts":1638500701.9799137,"msg":"serving initial configuration"}
{"level":"info","ts":1638500701.9799054,"logger":"tls.renew","msg":"acquiring lock","identifier":"172.16.238.1"}
{"level":"info","ts":1638500701.9832299,"logger":"tls.renew","msg":"lock acquired","identifier":"172.16.238.1"}
{"level":"info","ts":1638500701.983394,"logger":"tls.renew","msg":"renewing certificate","identifier":"172.16.238.1","remaining":-7033.983392455}
{"level":"info","ts":1638500701.984902,"logger":"tls.renew","msg":"certificate renewed successfully","identifier":"172.16.238.1"}
{"level":"info","ts":1638500701.9849126,"logger":"tls.renew","msg":"releasing lock","identifier":"172.16.238.1"}
{"level":"info","ts":1638500701.9849956,"logger":"tls","msg":"reloading managed certificate","identifiers":["172.16.238.1"]}
{"level":"warn","ts":1638500701.9852617,"logger":"tls","msg":"stapling OCSP","error":"no OCSP stapling for [172.16.238.1]: no OCSP server specified in certificate"}
{"level":"info","ts":1638500701.985277,"logger":"tls.cache","msg":"replaced certificate in cache","subjects":["172.16.238.1"],"new_expiration":1638543901}
{"level":"info","ts":1638504348.8368025,"msg":"shutting down apps, then terminating","signal":"SIGTERM"}
{"level":"warn","ts":1638504348.8368332,"msg":"exiting; byeee!! 👋","signal":"SIGTERM"}
{"level":"info","ts":1638504348.8380532,"logger":"tls.cache.maintenance","msg":"stopped background certificate maintenance","cache":"0xc0003dde30"}
{"level":"info","ts":1638504348.8392572,"logger":"admin","msg":"stopped previous server","address":"tcp/localhost:2019"}
{"level":"info","ts":1638504348.8392687,"msg":"shutdown complete","signal":"SIGTERM","exit_code":0}
Waiting for Nextcloud to start...
Waiting for Nextcloud to start...
Waiting for Nextcloud to start...
Waiting for Nextcloud to start...
Waiting for Nextcloud to start...
Waiting for Nextcloud to start...
Waiting for Nextcloud to start...
Waiting for Nextcloud to start...
Waiting for Nextcloud to start...
Waiting for Nextcloud to start...
Waiting for Nextcloud to start...
Waiting for Nextcloud to start...
Waiting for Nextcloud to start...
Waiting for Nextcloud to start...
Waiting for Nextcloud to start...
Waiting for Nextcloud to start...
AH00558: apache2: Could not reliably determine the server's fully qualified domain name, using 172.17.0.5. Set the 'ServerName' directive globally to suppress this message
{"level":"info","ts":1638537364.9673767,"msg":"using provided configuration","config_file":"/Caddyfile","config_adapter":""}
{"level":"warn","ts":1638537364.9712768,"msg":"input is not formatted with 'caddy fmt'","adapter":"caddyfile","file":"/Caddyfile","line":2}
{"level":"info","ts":1638537364.9735048,"logger":"admin","msg":"admin endpoint started","address":"tcp/localhost:2019","enforce_origin":false,"origins":["localhost:2019","[::1]:2019","127.0.0.1:2019"]}
{"level":"info","ts":1638537364.9737206,"logger":"http","msg":"server is listening only on the HTTPS port but has no TLS connection policies; adding one to enable TLS","server_name":"srv0","https_port":443}
{"level":"info","ts":1638537364.9743958,"logger":"tls.cache.maintenance","msg":"started background certificate maintenance","cache":"0xc0000da5b0"}
{"level":"info","ts":1638537364.9781172,"logger":"tls","msg":"cleaning storage unit","description":"FileStorage:/mnt/data/caddy"}
{"level":"info","ts":1638537364.9796786,"logger":"tls","msg":"finished cleaning storage units"}
{"level":"warn","ts":1638537365.0471437,"logger":"pki.ca.local","msg":"installing root certificate (you might be prompted for password)","path":"storage:pki/authorities/local/root.crt"}
2021/12/03 13:16:05 Warning: "certutil" is not available, install "certutil" with "apt install libnss3-tools" or "yum install nss-tools" and try again
2021/12/03 13:16:05 define JAVA_HOME environment variable to use the Java trust
{"level":"error","ts":1638537365.0500958,"logger":"pki.ca.local","msg":"failed to install root certificate","error":"failed to execute tee: exit status 1","certificate_file":"storage:pki/authorities/local/root.crt"}
{"level":"info","ts":1638537365.05069,"logger":"http","msg":"enabling automatic TLS certificate management","domains":["172.16.238.1"]}
{"level":"warn","ts":1638537365.051946,"logger":"tls","msg":"stapling OCSP","error":"no OCSP stapling for [172.16.238.1]: no OCSP server specified in certificate"}
{"level":"info","ts":1638537365.0523639,"logger":"tls.renew","msg":"acquiring lock","identifier":"172.16.238.1"}
{"level":"info","ts":1638537365.0525978,"msg":"autosaved config (load with --resume flag)","file":"/var/www/.config/caddy/autosave.json"}
{"level":"info","ts":1638537365.0526392,"msg":"serving initial configuration"}
{"level":"info","ts":1638537365.0564508,"logger":"tls.renew","msg":"lock acquired","identifier":"172.16.238.1"}
{"level":"info","ts":1638537365.0569696,"logger":"tls.renew","msg":"renewing certificate","identifier":"172.16.238.1","remaining":6535.943033251}
{"level":"info","ts":1638537365.059791,"logger":"tls.renew","msg":"certificate renewed successfully","identifier":"172.16.238.1"}
{"level":"info","ts":1638537365.0598307,"logger":"tls.renew","msg":"releasing lock","identifier":"172.16.238.1"}
{"level":"info","ts":1638537365.0599806,"logger":"tls","msg":"reloading managed certificate","identifiers":["172.16.238.1"]}
{"level":"warn","ts":1638537365.0605683,"logger":"tls","msg":"stapling OCSP","error":"no OCSP stapling for [172.16.238.1]: no OCSP server specified in certificate"}
{"level":"info","ts":1638537365.0605974,"logger":"tls.cache","msg":"replaced certificate in cache","subjects":["172.16.238.1"],"new_expiration":1638580565}
Going to 172.17.0.8 (8080) = Container UI and 8444 = KO.
Hi, you must have seen an input field where you can put in your domain.
Please try to start all over again by doing the following:
Stop containers button and wait until they are stoppedsudo docker stop nextcloud-aio-mastercontainer && \
sudo docker rm nextcloud-aio-mastercontainer && \
docker container prune -f && \
docker volume prune -f && \
docker pull nextcloud/all-in-one:latest
docker run... command again.Please report back if that works. Thanks! 
@szaimen Now I get this error:
Fatal error: Uncaught GuzzleHttp\Exception\ServerException: Server error: `POST http://localhost/v1.41/containers/nextcloud-aio-domaincheck/start` resulted in a `500 Internal Server Error` response: {"message":"driver failed programming external connectivity on endpoint nextcloud-aio-domaincheck (c575e8f0413bd3b072149 (truncated...) in /var/www/docker-aio/php/vendor/guzzlehttp/guzzle/src/Exception/RequestException.php:113 Stack trace: #0 /var/www/docker-aio/php/vendor/guzzlehttp/guzzle/src/Middleware.php(69): GuzzleHttp\Exception\RequestException::create(Object(GuzzleHttp\Psr7\Request), Object(GuzzleHttp\Psr7\Response), NULL, Array, NULL) #1 /var/www/docker-aio/php/vendor/guzzlehttp/promises/src/Promise.php(204): GuzzleHttp\Middleware::GuzzleHttp\{closure}(Object(GuzzleHttp\Psr7\Response)) #2 /var/www/docker-aio/php/vendor/guzzlehttp/promises/src/Promise.php(153): GuzzleHttp\Promise\Promise::callHandler(1, Object(GuzzleHttp\Psr7\Response), NULL) #3 /var/www/docker-aio/php/vendor/guzzlehttp/promises/src/TaskQueue.php(48): GuzzleHttp\Promise\Promise::GuzzleHttp\Promise\{closure}() #4 /var/www/docker-aio/php/vendor/guzzlehttp/promises/src/Promise.php(248): GuzzleHttp\Promise\TaskQueue->run(true) #5 /var/www/docker-aio/php/vendor/guzzlehttp/promises/src/Promise.php(224): GuzzleHttp\Promise\Promise->invokeWaitFn() #6 /var/www/docker-aio/php/vendor/guzzlehttp/promises/src/Promise.php(269): GuzzleHttp\Promise\Promise->waitIfPending() #7 /var/www/docker-aio/php/vendor/guzzlehttp/promises/src/Promise.php(226): GuzzleHttp\Promise\Promise->invokeWaitList() #8 /var/www/docker-aio/php/vendor/guzzlehttp/promises/src/Promise.php(62): GuzzleHttp\Promise\Promise->waitIfPending() #9 /var/www/docker-aio/php/vendor/guzzlehttp/guzzle/src/Client.php(187): GuzzleHttp\Promise\Promise->wait() #10 /var/www/docker-aio/php/vendor/guzzlehttp/guzzle/src/ClientTrait.php(95): GuzzleHttp\Client->request('POST', 'http://localhos...', Array) #11 /var/www/docker-aio/php/src/Docker/DockerActionManager.php(155): GuzzleHttp\Client->post('http://localhos...') #12 /var/www/docker-aio/php/src/Controller/DockerController.php(40): AIO\Docker\DockerActionManager->StartContainer(Object(AIO\Container\Container)) #13 /var/www/docker-aio/php/src/Controller/DockerController.php(165): AIO\Controller\DockerController->PerformRecursiveContainerStart('nextcloud-aio-d...') #14 /var/www/docker-aio/php/public/index.php(75): AIO\Controller\DockerController->StartDomaincheckContainer() #15 /var/www/docker-aio/php/vendor/slim/slim/Slim/Handlers/Strategies/RequestResponse.php(43): Closure->{closure}(Object(GuzzleHttp\Psr7\ServerRequest), Object(GuzzleHttp\Psr7\Response), Array) #16 /var/www/docker-aio/php/vendor/slim/slim/Slim/Routing/Route.php(384): Slim\Handlers\Strategies\RequestResponse->__invoke(Object(Closure), Object(GuzzleHttp\Psr7\ServerRequest), Object(GuzzleHttp\Psr7\Response), Array) #17 /var/www/docker-aio/php/vendor/slim/slim/Slim/MiddlewareDispatcher.php(81): Slim\Routing\Route->handle(Object(GuzzleHttp\Psr7\ServerRequest)) #18 /var/www/docker-aio/php/vendor/slim/slim/Slim/MiddlewareDispatcher.php(81): Slim\MiddlewareDispatcher->handle(Object(GuzzleHttp\Psr7\ServerRequest)) #19 /var/www/docker-aio/php/vendor/slim/slim/Slim/Routing/Route.php(341): Slim\MiddlewareDispatcher->handle(Object(GuzzleHttp\Psr7\ServerRequest)) #20 /var/www/docker-aio/php/vendor/slim/slim/Slim/Routing/RouteRunner.php(84): Slim\Routing\Route->run(Object(GuzzleHttp\Psr7\ServerRequest)) #21 /var/www/docker-aio/php/vendor/slim/csrf/src/Guard.php(456): Slim\Routing\RouteRunner->handle(Object(GuzzleHttp\Psr7\ServerRequest)) #22 /var/www/docker-aio/php/vendor/slim/slim/Slim/MiddlewareDispatcher.php(209): Slim\Csrf\Guard->process(Object(GuzzleHttp\Psr7\ServerRequest), Object(Slim\Routing\RouteRunner)) #23 /var/www/docker-aio/php/vendor/slim/twig-view/src/TwigMiddleware.php(125): Psr\Http\Server\RequestHandlerInterface@anonymous->handle(Object(GuzzleHttp\Psr7\ServerRequest)) #24 /var/www/docker-aio/php/vendor/slim/slim/Slim/MiddlewareDispatcher.php(147): Slim\Views\TwigMiddleware->process(Object(GuzzleHttp\Psr7\ServerRequest), Object(Psr\Http\Server\RequestHandlerInterface@anonymous)) #25 /var/www/docker-aio/php/src/Middleware/AuthMiddleware.php(38): Psr\Http\Server\RequestHandlerInterface@anonymous->handle(Object(GuzzleHttp\Psr7\ServerRequest)) #26 /var/www/docker-aio/php/vendor/slim/slim/Slim/MiddlewareDispatcher.php(313): AIO\Middleware\AuthMiddleware->__invoke(Object(GuzzleHttp\Psr7\ServerRequest), Object(Psr\Http\Server\RequestHandlerInterface@anonymous)) #27 /var/www/docker-aio/php/vendor/slim/slim/Slim/MiddlewareDispatcher.php(81): Psr\Http\Server\RequestHandlerInterface@anonymous->handle(Object(GuzzleHttp\Psr7\ServerRequest)) #28 /var/www/docker-aio/php/vendor/slim/slim/Slim/App.php(215): Slim\MiddlewareDispatcher->handle(Object(GuzzleHttp\Psr7\ServerRequest)) #29 /var/www/docker-aio/php/vendor/slim/slim/Slim/App.php(199): Slim\App->handle(Object(GuzzleHttp\Psr7\ServerRequest)) #30 /var/www/docker-aio/php/public/index.php(140): Slim\App->run() #31 {main} thrown in /var/www/docker-aio/php/vendor/guzzlehttp/guzzle/src/Exception/RequestException.php on line 113
Is another service running on port 443 on your instance?
BTW: I’ve just overworked the readme and added some more docs about the project:
Maybe it makes sense for you to check that out 
@szaimen Thank you for your patience… I now get the input asking my to choose a DNS, but I don’t know what to input because I am installing NC on my laptop, it is just to test locally (no need for external connection), I want to play with NC on my computer before deploying eventually to a real server.
What should I input? 172.X.X.X or 127.0.0.1 or localhost or?
Thanks!
Hi, unfortunately are local domains and ip-addresses currently not supported.
But I just found this article that shows and explains the whole process pretty well:
Wow, that’s a good how-to! I will have to try this. We need such how-to’s in the official documentation!
Yeah it’s a good article. But all the additions in the article are about how to run docker in rootless mode. The part about Nextcloud AIO is literally the same like on the GitHub page of the project, because there isn’t really much to it from a users perspective. Everything is handeld through the containers. There is not much you can do wrong. It really just works. 
@szaimen If we could install it with a local domain name or IP address to run it only locally or behind an existing reverse proxy, it would be perfect. 
We’ll maybe add that at some point in the future. But for now we have other priorities like adding support for arm64 and more ![]()
Feel free to investigate yourself how it could made work with reverse proxies and Co. PRs are always welcome ![]()
Yeah, I just tried it, you are right. Looks like a perfect setup. Everything is working out of the box after less than 10 minutes and uses less than 1GB RAM.
Reverse proxies are supported since v0.6.0 
Hi All,
I’m struggling with the same issue and cannot resolve it.
I’ve installed NC from Nextcloud All In One Beta in docker hosted in VPS (contabo VPS). I’ve domain (bla.blabla.meh) at a different company with hopefully properly configured records. At contabo I’ve configured reverse DNS pointing my domain to the server’s IPv4 and IPv6 address (or vica versa, whatever). (I’ve a currently disabled different webserver application working properly without HTTPS)
In the apache log I see:
tls.obtain",“msg”:“could not get certificate from issuer”,“identifier”:“bla.blabla.meh”,“issuer”:“acme-v02.api.letsencrypt.org-directory”,“error”:"[bla.blabla.meh] solving challenges: bla.blabla.meh: no solvers available for remaining challenges (configured=[tls-alpn-01] offered=[http-01 dns-01 tls-alpn-01] remaining=[http-01 dns-01]) …
I use portainer to manage docker containers. apache has open port: 443, mastercontainer 80
In the browser I cannot open NC because of ERR_SSL_PROTOCOL_ERROR.
I assume I’m missing something trivial, can somebody suggest what to do?
I’ve seen that before but no idea how to solve it. Did you maybe have had a wildcard certificate at some point in time before for that domain? And could you try with a different domain?
Apart from that you might be able to make it work using the reverse proxy option which allows to configure the whole tls handling manually. See: all-in-one/reverse-proxy.md at main · nextcloud/all-in-one · GitHub
I hadn’t have wildcard certificate. I have no different domain currently. (I’ll try to get some free fot the test).
I’m not an IT professional, so maybe I’m missing something trivial.
I’ve done the reverse proxy update in the Caddy file in the container and restarted. No change. ![]()
Long time ago I had successfully deployd let’s encrypt certbot on a different server, but that was also not trivial.
Could you suggest some basic tutorial, wiki, guide, anything how to get work HTTPS especially in docker virtualized next cloud? Including what’s supposed to be done at the providers configuration (DNS, reverse DNS, domain)?
Apache says:
“tls.issuance.acme.acme_client”,“msg”:“validating authorization”,“identifier”:“bla.bla”,“problem”:{“type”:“urn:ietf:params:acme:error:connection”,“title”:"",“detail”:“Timeout during connect (likely firewall problem)”,“instance”:"",“subproblems”:},“order”:"https://acme-staging-v02.api.l…
I don’t get this firewall problem.
My portainer:
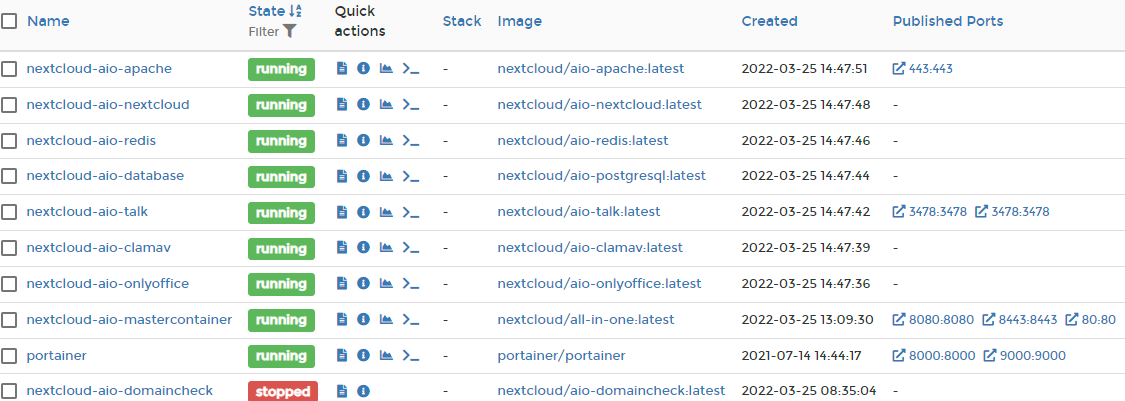
Sorry, no idea what could be wrong. If you still get this warning after following all-in-one/reverse-proxy.md at main · nextcloud/all-in-one · GitHub, you’ve configured something wrong though. (probably needs a container restart via the aio interface…)