Hi, I have some issues getting access to my nc running at home from the internet.
I have nexcloud up and running on a raspberry pi 4 at my home. To access it from outside my home I rented a vps with a public ip and connected the pi via wireguard (my ISP only provides a public ipv6 and a non-configurable firewall -.- ). Also, I configured iptables on the vps for routing all traffic to port 80 and 443 to the pi and changing the source of outgoing traffic to the public ip of the vps. With this, I can ping the vps through wireguard, as well as the internet (from the pi).
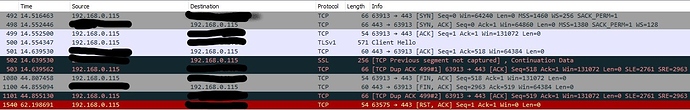
But : I can’t access nc in the browser, I get a timeout message.
The really weird thing is that terminal tools, like curl or wget, do get messages from the nginx server running nc, like the expected 301 error when connecting over http.
I’m not very experienced with network stuff so I might have a stupid error somewhere and I’m very much out of ideas how to debug this situation.
Here are some more details:
- DNS entry pointing on public ip of vps
On the my home network:
- Nextcloud running on nginx
- let’s encrypt certificate & certbot
- no iptables rules
- forwarding enabled in kernel & iptables
- wireguard config:
[Interface]
Address = 192.168.2.2/32
PrivateKey =
ListenPort = 51653
[Peer]
PublicKey =
AllowedIPs = 0.0.0.0/0
Endpoint = xxx.xxx.xxx.xxx:51653
PersistentKeepalive = 25
On the vps:
- forwarding enabled in kernel & iptables
- wireguard config:
[Interface]
Address = 192.168.2.1/24
Address = fd13:3dae:bf12:8012::/64
SaveConfig = true
ListenPort = 51653
PrivateKey =
[Peer]
PublicKey =
AllowedIPs = 192.168.2.2/32
Endpoint = yyy.yyy.yyy.yyy:54089
- External firewall of the vps allows ports 22,80,443,51653
- iptables:
-A PREROUTING -i ens192 -p tcp --dport 80 -j DNAT --to-destination 192.168.2.2:80
-A PREROUTING -i ens192 -p tcp --dport 443 -j DNAT --to-destination 192.168.2.2:443
-A POSTROUTING -o ens192 -j SNAT --to-source (vps public ip)
Some tutorials suggested to also use
-A POSTROUTING -d 192.168.2.2/32 -o wg1 -p tcp -j SNAT --to-source 192.168.2.1
but this didn’t help. Bonus question: Would the vps even be able to deliver responses from nc when this last rule replaces the real sender?
I also tried MASQUERADE instead SNAT.
Thanks for every idea or solution!