Nextcloud version: 28.0.4
Operating system and version: Debian Bookworm
Apache or nginx version: nginx 1.25.5
PHP version: 8.2-fpm
DB Version: Postgresql 15
The issue you are facing:
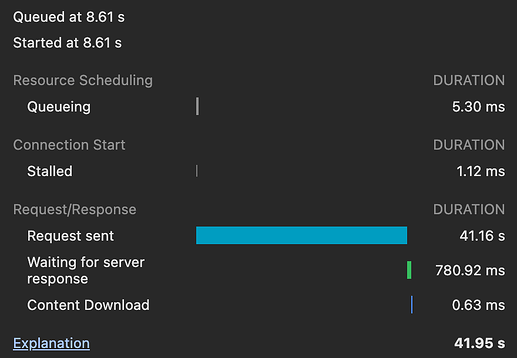
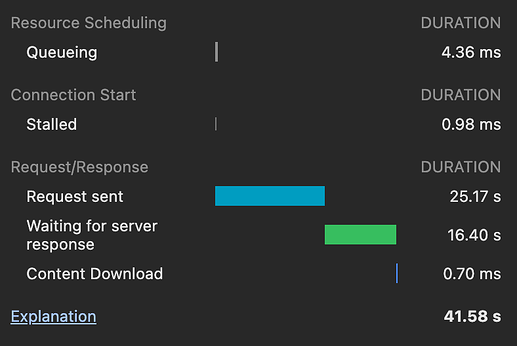
Slow upload speed on a new Nextcloud install (0.5 MB/s max).
For example:
- 14MB JPG Upload Time: 35 seconds
- 16MB DNG Upload Time: 39 seconds
- 10MB DNG Upload Time: 25 seconds
Is this the first time you’ve seen this error? (Y/N): N
Had a Nextcloud instance running on a raspi with the same slow upload speed and put it off on the “slow” hardware.
New instance is a VM running 6 vCPUs, 8 GB Ram, 32 GB Boot NVMe SSD and 2x 10TB HDD (Raid 1 ncdata disks - dd speed: 245 MB/s).
So shouldn’t be a resource problem (if necessary, more ram can be allocated).
Steps to replicate it:
- Install Nextcloud with Setup Guide:
https://decatec.de/home-server/nextcloud-auf-ubuntu-server-22-04-lts-mit-nginx-postgresql-mariadb-php-lets-encrypt-redis-und-fail2ban/ - Configure Imaginary
- Upload File
Only thing I left out was Fail2Ban.
The output of your Nextcloud log in Admin > Logging:
nothing relevant
The output of your config.php file in /path/to/nextcloud (make sure you remove any identifiable information!):
$CONFIG = array (
'maintenance_window_start' => 3,
'instanceid' => 'balela',
'passwordsalt' => 'blabla',
'secret' => 'blabla,
'trusted_domains' =>
array (
0 => 'my-domain',
),
'datadirectory' => '/mnt/ncdata/data',
'dbtype' => 'pgsql',
'version' => '28.0.4.1',
'overwrite.cli.url' => 'https://my-domain,
'dbname' => 'nextcloud_db',
'dbhost' => 'localhost',
'dbport' => '',
'dbtableprefix' => 'oc_',
'dbuser' => '',
'dbpassword' => '',
'installed' => true,
'default_phone_region' => 'DE',
'memcache.local' => '\OC\Memcache\APCu',
'overwriteprotocol' => 'https',
'logtimezone' => 'Europe/Berlin',
'filelocking.enabled' => true,
'memcache.locking' => '\OC\Memcache\Redis',
'redis' => array (
'host' => '/var/run/redis/redis-server.sock',
'port' => 0,
'timeout' => 0.0,
),
'enable_previews' => true,
'enabledPreviewProviders' =>
array (
0 => 'OC\\Preview\\PNG',
1 => 'OC\\Preview\\JPEG',
2 => 'OC\\Preview\\GIF',
3 => 'OC\\Preview\\HEIC',
4 => 'OC\\Preview\\BMP',
5 => 'OC\\Preview\\XBitmap',
6 => 'OC\\Preview\\MP3',
7 => 'OC\\Preview\\TXT',
8 => 'OC\\Preview\\MarkDown',
9 => 'OC\\Preview\\Movie',
10 => 'OC\\Preview\\MKV',
11 => 'OC\\Preview\\MP4',
12 => 'OC\\Preview\\AVI',
13 => 'OC\\Preview\\PDF',
14 => 'OC\\Preview\\Imaginary',
),
'preview_imaginary_url' => 'http://127.0.0.1:9000',
'preview_max_x' => 4096,
'preview_max_y' => 4096,
'preview_max_filesize_image' => 50,
'preview_max_memory' => 256,
);
The output of your Apache/nginx/system log in /var/log/____:
nothing indicating an error
I’d really appreciate the help to configure this instance correctly for a somewhat reasonable upload speed.
The instance is btw. local so it can’t be a network bottleneck.
The test device is connected via 1 Gbit Lan to the server.
(iPerf says 940 Mbit in both directions)
Thank you in advance