Hi folks, this thread seem to fit my problem, but I can’t get it to work for me.
I have to admit, my experience witrh webservers, reverse proxy and so on is not that much. So I hope you can give me some hints that I’m able to understand it.
First of all, only public access for Android / iOS Apps is not working as this shall be done via port forwarding.
Local / VPN Network with subdomain (Local Pi-hole with DNS pointing to the same reverse proxy) seems to work perfectly (Web and Apps).
The target is not to expose a whole container / VM, I want to keep it small and therefore just port forwarding with reverse proxy in the local network. Actually this is working fine for some other services / ports I use.
So lets get a bit more detailed into my setup.
- My Fritz!Box synchronizes a DDNS and does also the TCP Port (9880) forwarding to the Docker LXC and therefore to the Reverse Proxy (“Nginx Proxy Manger” as Docker Container (LXC installation failed in my case) 192.168.10.199).
- The NPM listens at the forwarded port (9880)
For this container the internal port 443, 80 is open so it can communicate with any other VM / LXC locally.
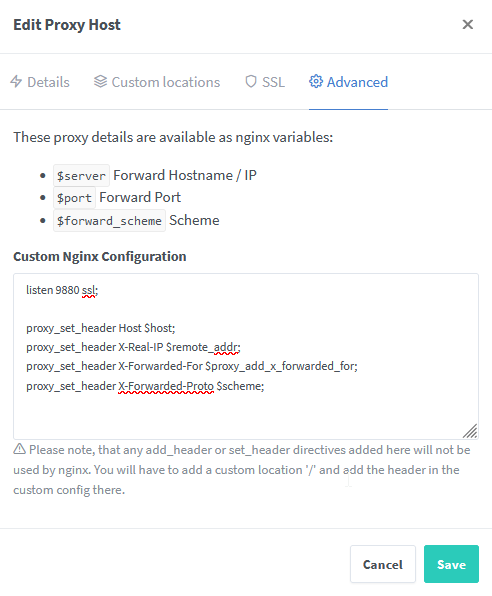
The automatically generated configuration from NPM (The part between ... listen 9880 ... location / { ... was manually entered as shown in the screenshot below):
server {
set $forward_scheme https;
set $server "192.168.10.200";
set $port 443;
listen 80;
listen [::]:80;
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name my.ddns-service.tld:9880;
# Let's Encrypt SSL
include conf.d/include/letsencrypt-acme-challenge.conf;
include conf.d/include/ssl-ciphers.conf;
ssl_certificate /etc/letsencrypt/live/npm-5/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/npm-5/privkey.pem;
# Block Exploits
include conf.d/include/block-exploits.conf;
# HSTS (ngx_http_headers_module is required) (63072000 seconds = 2 years)
add_header Strict-Transport-Security "max-age=63072000;includeSubDomains; preload" always;
# Force SSL
include conf.d/include/force-ssl.conf;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection $http_connection;
proxy_http_version 1.1;
access_log /data/logs/proxy-host-28_access.log proxy;
error_log /data/logs/proxy-host-28_error.log warn;
listen 9880 ssl;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
location / {
# HSTS (ngx_http_headers_module is required) (63072000 seconds = 2 years)
add_header Strict-Transport-Security "max-age=63072000;includeSubDomains; preload" always;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection $http_connection;
proxy_http_version 1.1;
# Proxy!
include conf.d/include/proxy.conf;
}
# Custom
include /data/nginx/custom/server_proxy[.]conf;
}
- The Nextcloud container (LXC not Docker) is being created with a turnkey template.
- config.php (trusted domain, proxy and some other changes):
<?php
$CONFIG = array (
'passwordsalt' => 'salty',
'secret' => 'secret',
'trusted_domains' =>
array (
0 => 'localhost',
1 => 'my.ddns-service.tld',
2 => 'nextcloud.my.ddns-service.tld',
3 => '192.168.10.200',
),
'trusted_proxies' =>
array (
0 => '192.168.10.199',
),
'datadirectory' => '/var/www/nextcloud-data',
'dbtype' => 'mysql',
'version' => '25.0.2.3',
'overwrite.cli.url' => 'https://my.ddns-service.tld:9880/',
'overwriteprotocol' => 'https',
'dbname' => 'nextcloud',
'dbhost' => 'localhost',
'dbport' => '',
'dbtableprefix' => 'oc_',
'mysql.utf8mb4' => true,
'dbuser' => 'nextcloud',
'dbpassword' => 'password',
'installed' => true,
'instanceid' => 'instance',
'memcache.local' => '\\OC\\Memcache\\Redis',
'redis' =>
array (
'host' => '/var/run/redis/redis.sock',
'port' => 0,
'timeout' => 0.0,
),
'default_language' => 'de',
'default_locale' => 'de_DE',
'default_phone_region' => 'de',
'filelocking.enabled' => true,
'memcache.locking' => '\\OC\\Memcache\\Redis',
'updater.secret' => 'secret',
'maintenance' => false,
'theme' => '',
'loglevel' => 2,
);
- nextcloud.conf (only changes for caldav / carddav):
ServerName localhost
<VirtualHost *:80>
UseCanonicalName Off
ServerAdmin webmaster@localhost
RewriteEngine On
RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301]
</VirtualHost>
<VirtualHost *:443>
SSLEngine on
ServerAdmin webmaster@localhost
DocumentRoot /var/www/nextcloud/
<IfModule mod_headers.c>
Header always set Strict-Transport-Security "max-age=15552000; includeSubDomains"
</IfModule>
<IfModule mod_rewrite.c>
RewriteEngine on
RewriteRule ^/\.well-known/carddav /remote.php/dav [R=301,L]
RewriteRule ^/\.well-known/caldav /remote.php/dav [R=301,L]
</IfModule>
</VirtualHost>
<Directory /var/www/nextcloud/>
Options +FollowSymLinks
AllowOverride All
Require all granted
</Directory>
- The SSL Certificate is done on the NPM.
The weird thing is when I connect my Android to the local subdomain of the nextcloud. The Pi-Hole DNS returns the Docker IP-Address. With this Address and Subdomain the NPM has another setup listening on port 443 and does more or less the same forwarding. This is working, so where is the problem between the Fritz!Box and the port forwarding?
So hope someone has the right hint for me, I’ll appreciate any help.