Nextcloud version: 25.0.2
Operating system and version: Ubuntu 22.04
nginx version: nginx/1.23.3
PHP version: PHP 8.1.2-1ubuntu2.9 (cli) (built: Oct 19 2022 14:58:09) (NTS)
Running in a lxc container (Host and Container OS Ubuntu 22.04)
Running behind haproxy
`
Hi,
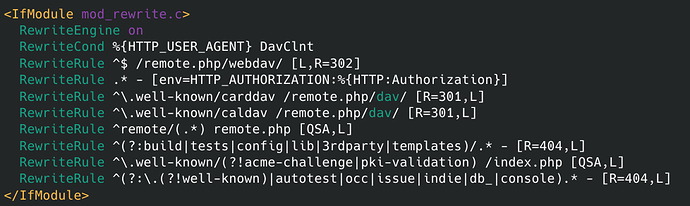
the Admin Overview give me some warnings like
Your web server is not properly set up to resolve "/.well-known/caldav". Further information can be found in the documentation ↗. (and for carddav, webinger…)
Hoewever, I think it answer it correct:
curl nc.caroschaf.de/.well-known/caldav -v
* Trying 2a02:810a:bc0:3800:216:3eff:fee4:84c4:80...
* Connected to nc.caroschaf.de (2a02:810a:bc0:3800:216:3eff:fee4:84c4) port 80 (#0)
> GET /.well-known/caldav HTTP/1.1
> Host: nc.caroschaf.de
> User-Agent: curl/7.81.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 301 Moved Permanently
< content-length: 0
< location: https://nc.caroschaf.de/remote.php/dav
<
* Connection #0 to host nc.caroschaf.de left intact
and
curl nc.caroschaf.de/.well-known/caldav -vL
* Trying 2a02:810a:bc0:3800:216:3eff:fee4:84c4:80...
* Connected to nc.caroschaf.de (2a02:810a:bc0:3800:216:3eff:fee4:84c4) port 80 (#0)
> GET /.well-known/caldav HTTP/1.1
> Host: nc.caroschaf.de
> User-Agent: curl/7.81.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 301 Moved Permanently
< content-length: 0
< location: https://nc.caroschaf.de/remote.php/dav
<
* Connection #0 to host nc.caroschaf.de left intact
* Clear auth, redirects to port from 80 to 443
* Issue another request to this URL: 'https://nc.caroschaf.de/remote.php/dav'
* Trying 2a02:810a:bc0:3800:216:3eff:fee4:84c4:443...
* Connected to nc.caroschaf.de (2a02:810a:bc0:3800:216:3eff:fee4:84c4) port 443 (#1)
* ALPN, offering h2
* ALPN, offering http/1.1
* CAfile: /etc/ssl/certs/ca-certificates.crt
* CApath: /etc/ssl/certs
* TLSv1.0 (OUT), TLS header, Certificate Status (22):
* TLSv1.3 (OUT), TLS handshake, Client hello (1):
* TLSv1.2 (IN), TLS header, Certificate Status (22):
* TLSv1.3 (IN), TLS handshake, Server hello (2):
* TLSv1.2 (IN), TLS header, Finished (20):
* TLSv1.2 (IN), TLS header, Supplemental data (23):
* TLSv1.3 (IN), TLS handshake, Encrypted Extensions (8):
* TLSv1.2 (IN), TLS header, Supplemental data (23):
* TLSv1.3 (IN), TLS handshake, Certificate (11):
* TLSv1.2 (IN), TLS header, Supplemental data (23):
* TLSv1.3 (IN), TLS handshake, CERT verify (15):
* TLSv1.2 (IN), TLS header, Supplemental data (23):
* TLSv1.3 (IN), TLS handshake, Finished (20):
* TLSv1.2 (OUT), TLS header, Finished (20):
* TLSv1.3 (OUT), TLS change cipher, Change cipher spec (1):
* TLSv1.2 (OUT), TLS header, Supplemental data (23):
* TLSv1.3 (OUT), TLS handshake, Finished (20):
* SSL connection using TLSv1.3 / TLS_AES_128_GCM_SHA256
* ALPN, server did not agree to a protocol
* Server certificate:
* subject: CN=nc.caroschaf.de
* start date: Jan 11 14:43:24 2023 GMT
* expire date: Apr 11 14:43:23 2023 GMT
* subjectAltName: host "nc.caroschaf.de" matched cert's "nc.caroschaf.de"
* issuer: C=US; O=Let's Encrypt; CN=R3
* SSL certificate verify ok.
* TLSv1.2 (OUT), TLS header, Supplemental data (23):
> GET /remote.php/dav HTTP/1.1
> Host: nc.caroschaf.de
> User-Agent: curl/7.81.0
> Accept: */*
>
* TLSv1.2 (IN), TLS header, Supplemental data (23):
* TLSv1.3 (IN), TLS handshake, Newsession Ticket (4):
* TLSv1.2 (IN), TLS header, Supplemental data (23):
* TLSv1.3 (IN), TLS handshake, Newsession Ticket (4):
* old SSL session ID is stale, removing
* TLSv1.2 (IN), TLS header, Supplemental data (23):
* Mark bundle as not supporting multiuse
< HTTP/1.1 401 Unauthorized
< server: nginx
< date: Sat, 04 Feb 2023 20:20:28 GMT
< content-type: application/xml; charset=utf-8
< transfer-encoding: chunked
< set-cookie: oc_sessionPassphrase=5efbRXoCRuYXqjEIWtARbpm3iXnsw8wImz0AaXSp8K26HSWyZBMkJql%2BfO%2BFmW3yPpWrM6E0bmf56O8kq9sQTt%2FvD8Wf2ztvCpzf%2Bj6iEDNhjmOQZg1nZdYu4RSBW3FP; path=/; secure; HttpOnly; SameSite=Lax
< set-cookie: __Host-nc_sameSiteCookielax=true; path=/; httponly;secure; expires=Fri, 31-Dec-2100 23:59:59 GMT; SameSite=lax
< set-cookie: __Host-nc_sameSiteCookiestrict=true; path=/; httponly;secure; expires=Fri, 31-Dec-2100 23:59:59 GMT; SameSite=strict
< set-cookie: ocb4a5xzzp24=9cs0llimqp17m9jmbq4j0vind9; path=/; secure; HttpOnly; SameSite=Lax
< expires: Thu, 19 Nov 1981 08:52:00 GMT
< cache-control: no-store, no-cache, must-revalidate
< pragma: no-cache
< content-security-policy: default-src 'none';
< www-authenticate: Basic realm="Nextcloud", charset="UTF-8"
< referrer-policy: no-referrer
< x-content-type-options: nosniff
< x-download-options: noopen
< x-frame-options: SAMEORIGIN
< x-permitted-cross-domain-policies: none
< x-robots-tag: none
< x-xss-protection: 1; mode=block
<
<?xml version="1.0" encoding="utf-8"?>
<d:error xmlns:d="DAV:" xmlns:s="http://sabredav.org/ns">
<s:exception>Sabre\DAV\Exception\NotAuthenticated</s:exception>
<s:message>No public access to this resource., No 'Authorization: Basic' header found. Either the client didn't send one, or the server is misconfigured, No 'Authorization: Bearer' header found. Either the client didn't send one, or the server is mis-configured, No 'Authorization: Basic' header found. Either the client didn't send one, or the server is misconfigured</s:message>
</d:error>
* Connection #1 to host nc.caroschaf.de left intact
Is this behaviour correct? If not, whats wrong? If yes, what “check” the internal test and doesn’t success?
Thanks