zoo3
September 13, 2022, 9:23am
1
I’m having trouble with “Security & setup warnings”. I get the following warning when I write an X header to nginx.
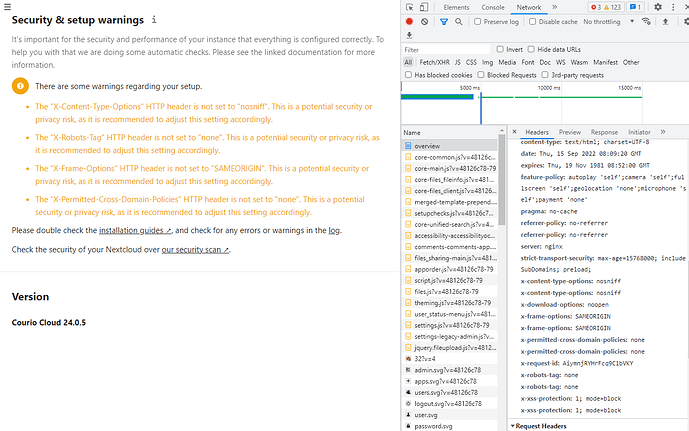
There are some warnings regarding your setup.
The "X-Content-Type-Options" HTTP header is not set to "nosniff". This is a potential security or privacy risk, as it is recommended to adjust this setting accordingly.
The "X-Robots-Tag" HTTP header is not set to "none". This is a potential security or privacy risk, as it is recommended to adjust this setting accordingly.
The "X-Frame-Options" HTTP header is not set to "SAMEORIGIN". This is a potential security or privacy risk, as it is recommended to adjust this setting accordingly.
The "X-Permitted-Cross-Domain-Policies" HTTP header is not set to "none". This is a potential security or privacy risk, as it is recommended to adjust this setting accordingly.
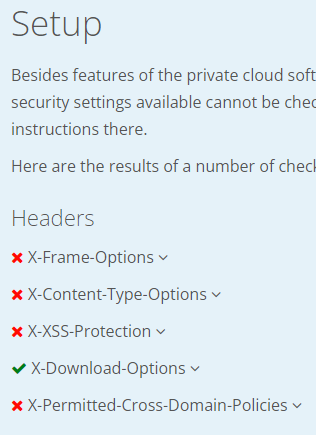
Result is “A”. However, the Setup section states the following
NO - X-Frame-Options
NO - X-Content-Type-Options
NO - X-XSS-Protection
PASS - X-Download-Options
NO - X-Permitted-Cross-Domain-Policies
→ NO is an X and PASS is a check mark. If the pass is only “X-Download-Options”, I would question an A grade decision on that.
I added the X header to nginx to verify and the result was “B”.
Content Security Policy (CSP) header not implemented
Cookies Prefixed
*The X header I added is itself recognized.
So the X header is recognized by the two sites(Nextcloud / Moziila ), so is the warnings in “Security & setup warnings” wrong?
I can add the X header and run “curl -i URL” and it will output the X header, or not if I don’t add it.
How can I fix this crazy state?
zoo3
September 15, 2022, 8:20am
2
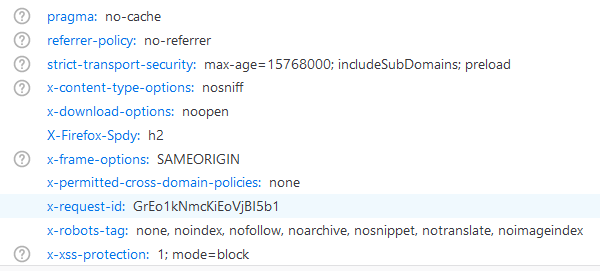
I check the response headers in the browser’s developer tools and an X headers are returned.
I don’t understand this either.
wwe
September 15, 2022, 7:10pm
3
My first guess was the headers (check) is case sensitive - but it’s not the case, my headers are lower-case as well and I have no warnings and A+ Nextcloud security scan result.
I see you all your headers doubled. This may or may not be an issue, please review.
if you had provide us with the support form, we would have known what was your server conf, but…
So, guessing with the help of my chrystall ball what you might use apache… could be a misconfiguration, but as you get A+, maybee not.
So next on the list is /var/www/… …/.htaccess
<IfModule mod_headers.c>
<IfModule mod_setenvif.c>
<IfModule mod_fcgid.c>
SetEnvIfNoCase ^Authorization$ "(.+)" XAUTHORIZATION=$1
RequestHeader set XAuthorization %{XAUTHORIZATION}e env=XAUTHORIZATION
</IfModule>
<IfModule mod_proxy_fcgi.c>
SetEnvIfNoCase Authorization "(.+)" HTTP_AUTHORIZATION=$1
</IfModule>
<IfModule mod_lsapi.c>
SetEnvIfNoCase ^Authorization$ "(.+)" XAUTHORIZATION=$1
RequestHeader set XAuthorization %{XAUTHORIZATION}e env=XAUTHORIZATION
</IfModule>
</IfModule>
<IfModule mod_env.c>
# Add security and privacy related headers
# Avoid doubled headers by unsetting headers in "onsuccess" table,
# then add headers to "always" table: https://github.com/nextcloud/server/pull/19002
Header onsuccess unset Referrer-Policy
Header always set Referrer-Policy "no-referrer"
Header onsuccess unset X-Content-Type-Options
Header always set X-Content-Type-Options "nosniff"
Header onsuccess unset X-Frame-Options
Header always set X-Frame-Options "SAMEORIGIN"
Header onsuccess unset X-Permitted-Cross-Domain-Policies
Header always set X-Permitted-Cross-Domain-Policies "none"
Header onsuccess unset X-Robots-Tag
Header always set X-Robots-Tag "none"
Header onsuccess unset X-XSS-Protection
Header always set X-XSS-Protection "1; mode=block"
SetEnv modHeadersAvailable true
</IfModule>
# Add cache control for static resources
<FilesMatch "\.(css|js|svg|gif|png|jpg|ico|wasm|tflite)$">
Header set Cache-Control "max-age=15778463"
</FilesMatch>
<FilesMatch "\.(css|js|svg|gif|png|jpg|ico|wasm|tflite)(\?v=.*)?$">
Header set Cache-Control "max-age=15778463, immutable"
</FilesMatch>
# Let browsers cache WOFF files for a week
<FilesMatch "\.woff2?$">
Header set Cache-Control "max-age=604800"
</FilesMatch>
</IfModule>
# PHP 8+
<IfModule mod_php.c>
php_value mbstring.func_overload 0
php_value default_charset 'UTF-8'
php_value output_buffering 0
<IfModule mod_env.c>
SetEnv htaccessWorking true
</IfModule>
</IfModule>
<IfModule mod_mime.c>
AddType image/svg+xml svg svgz
AddType application/wasm wasm
AddEncoding gzip svgz
</IfModule>
<IfModule mod_dir.c>
DirectoryIndex index.php index.html
</IfModule>
<IfModule pagespeed_module>
ModPagespeed Off
</IfModule>
<IfModule mod_rewrite.c>
RewriteEngine on
RewriteCond %{HTTP_USER_AGENT} DavClnt
RewriteRule ^$ /remote.php/webdav/ [L,R=302]
RewriteRule .* - [env=HTTP_AUTHORIZATION:%{HTTP:Authorization}]
RewriteRule ^\.well-known/carddav /remote.php/dav/ [R=301,L]
RewriteRule ^\.well-known/caldav /remote.php/dav/ [R=301,L]
RewriteRule ^remote/(.*) remote.php [QSA,L]
RewriteRule ^(?:build|tests|config|lib|3rdparty|templates)/.* - [R=404,L]
RewriteRule ^\.well-known/(?!acme-challenge|pki-validation) /index.php [QSA,L]
RewriteRule ^(?:\.(?!well-known)|autotest|occ|issue|indie|db_|console).* - [R=404,L]
</IfModule>
AddDefaultCharset utf-8
Options -Indexes
#### DO NOT CHANGE ANYTHING ABOVE THIS LINE ####
ErrorDocument 403 //
ErrorDocument 404 //
1 Like
zoo3
September 16, 2022, 1:13am
5
I see you all your headers doubled. This may or may not be an issue, please review.
I too have not been able to figure out why each of these headers are duplicated showing two lines each. There is a switch in the Firefox developer tools called “raw header” and when I turn it on, each header is one at a time.
I have NC’s .htaccess permissions set to inaccessible, but those headers show duplicates. If the headers are removed, of course the X headers will not appear on the security check sites.
zoo3
September 16, 2022, 10:16am
6
I still found the problem in nginx.conf. First, reduce nginx.conf to the minimum configuration to run the site. Then create test.html and check the headers. Then, of course, the X headers are not set.
Then I checked by appending only the X header to nginx.conf and each one was set correctly. Developer tools and on the verification site. Next, I create nginx.conf as described on the official site.https://docs.nextcloud.com/server/latest/admin_manual/installation/nginx.html
I configured nginx.conf by adding parts step by step. ~~It seems that the only way to make each X header display independently is to put only the X header in nginx.conf. ~~
Just removing the X headers from nginx.conf on the above site will set the X header in the browser. Which setting is making the browser recognize it twice?
Do you have this line in the Nextcloud php location block of your nginx configuration?
fastcgi_param modHeadersAvailable true;
zoo3
September 21, 2022, 3:55am
10
curl -i https://MY-NEXTCLOUD/index.html
HTTP/1.1 200 OK
Server: nginx
Date: Wed, 21 Sep 2022 03:39:58 GMT
Content-Type: text/html; charset=UTF-8
Content-Length: 156
Last-Modified: Thu, 08 Sep 2022 10:32:53 GMT
Connection: keep-alive
Vary: Accept-Encoding
ETag: "6319c4d5-9c"
Strict-Transport-Security: max-age=15768000; includeSubDomains
Referrer-Policy: no-referrer
X-Content-Type-Options: nosniff
X-Download-Options: noopen
X-Frame-Options: SAMEORIGIN
X-Permitted-Cross-Domain-Policies: none
X-Robots-Tag: none
X-XSS-Protection: 1; mode=block
Content-Security-Policy: default-src 'XXX';
Accept-Ranges: bytes
<!DOCTYPE html>
<html>
<head>
<script> window.location.href="index.php"; </script>
<meta http-equiv="refresh" content="0; URL=index.php">
</head>
</html>
curl -i https://MY-NEXTCLOUD/index.php
HTTP/1.1 302 Found
Server: nginx
Date: Wed, 21 Sep 2022 03:40:08 GMT
Content-Type: text/html; charset=UTF-8
Transfer-Encoding: chunked
Connection: keep-alive
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Set-Cookie: oc_sessionPassphrase=XXX; path=/; secure; HttpOnly; ameSite=Lax
Set-Cookie: ocSERIAL=YYY; path=/; secure; HttpOnly; SameSite=Lax
Content-Security-Policy: default-src 'self'; script-src 'self' 'nonce-ZZZ'; style-src 'self' 'unsafe-inline'; frame-src *; img-src * data: blob:; font-src 'self' data:; media-src *; connect-src *; object-src 'none'; base-uri 'self';
Referrer-Policy: no-referrer
X-Content-Type-Options: nosniff
X-Frame-Options: SAMEORIGIN
X-Permitted-Cross-Domain-Policies: none
X-Robots-Tag: none
X-XSS-Protection: 1; mode=block
Set-Cookie: __Host-nc_sameSiteCookielax=true; path=/; httponly;secure; expires=Fri, 31-Dec-2100 23:59:59 GMT; SameSite=lax
Set-Cookie: __Host-nc_sameSiteCookiestrict=true; path=/; httponly;secure; expires=Fri, 31-Dec-2100 23:59:59 GMT; SameSite=strict
Location: https://MY-NEXTCLOUD/index.php/login
Strict-Transport-Security: max-age=15768000; includeSubDomains
Referrer-Policy: no-referrer
X-Content-Type-Options: nosniff
X-Download-Options: noopen
X-Frame-Options: SAMEORIGIN
X-Permitted-Cross-Domain-Policies: none
X-Robots-Tag: none
X-XSS-Protection: 1; mode=block
Content-Security-Policy: default-src 'XXX';
Checking with the curl command, index.html seems to read the X headers only once and *****.php twice.
Is this similar to this issue on Github?
opened 04:23PM - 30 Aug 19 UTC
closed 03:15PM - 24 Apr 20 UTC
enhancement
3. to review
Copied from https://github.com/nextcloud/server/issues/8207#issuecomment-5253730… 89
I'm running NextCloud 16.0.4 on Apache/2.4.39, PHP 7.2 CGI/FastCGI. For me, the headers are sent twice - once from the `.htaccess` and once from here:
https://github.com/nextcloud/server/blob/1b074f48d824107de651a34a3948692cb5ca448f/lib/private/legacy/response.php#L100-L103
Normally, this line should avoid running into the case shown above:
https://github.com/nextcloud/server/blob/9d6eb2daf7c0f9d50aca78db02dbe8418a642768/.htaccess#L21
But the environment variable can't be retrieved by `getenv` and is not shown in a phpinfo either. [Apparently](https://mediatemple.net/community/products/grid/204643130/using-environment-variables-in-php#Setting_your_own_variables), in some environments, only environment variables starting with `HTTP_` can be set in the `.htaccess`. I tried it and if I change the variable to e.g. `HTTP_MOD_HEADERS_AVAILABLE`, it works in phpinfo as well as in the `response.php`.
Maybe someone who has more experience with Apache / PHP-CGI can tell whether this might be a solution for at least some of the issues discussed here?
### Steps to reproduce
1. Navigate to https://cloud.zweiiconkram.de/index.php/settings/admin/overview
2. Look at the messages displayed there, and inspect the header information returned by the server.
### Expected behaviour
The headers like `X-Content-Type-Options: nosniff` should be transmitted exactly once. No messages warning about these headers should be displayed. `modHeadersAvailable` should be set to `true` in the `.htaccess`.
### Actual behaviour
The headers are sent twice. Once here:
https://github.com/nextcloud/server/blob/9d6eb2daf7c0f9d50aca78db02dbe8418a642768/.htaccess#L16-L21
and once here:
https://github.com/nextcloud/server/blob/1b074f48d824107de651a34a3948692cb5ca448f/lib/private/legacy/response.php#L100-L103
The environment variable `modHeadersAvailable` doesn't exist.
If I change the server from CGI/FastCGI to FPM, neither `modHeadersAvailable` nor `HTTP_MOD_HEADERS_AVAILABLE` can be accessed by PHP - they seem to be prefixed with `REDIRECT_`. But FPM somehow seems to avoid sending the same headers twice, so the issue doesn't visibly appear there. However, I would not regard this as a solution to the problem, because the intended behaviour (not running into the if case if the headers have been sent by `.htaccess`) doesn't apply.
### Server configuration
**Operating system**: Linux x86_64
**Web server:** Apache/2.4.39
**Database:** MySQL 5.6.19
**PHP version:** 7.2.11, CGI/FastCGI
**Nextcloud version:** 16.0.4
**Updated from an older Nextcloud/ownCloud or fresh install:** Continuously updated, starting from probably 11 or 12.
**Where did you install Nextcloud from:** https://nextcloud.com/install/#instructions-server
**Signing status:**
<details>
<summary>Signing status</summary>
```
No errors have been found.
```
</details>
**List of activated apps:**
<details>
<summary>App list</summary>
```
Enabled:
- accessibility: 1.2.0
- activity: 2.9.1
- bruteforcesettings: 1.4.0
- cloud_federation_api: 0.2.0
- comments: 1.6.0
- dav: 1.9.2
- federatedfilesharing: 1.6.0
- federation: 1.6.0
- files: 1.11.0
- files_pdfviewer: 1.5.0
- files_rightclick: 0.15.1
- files_sharing: 1.8.0
- files_texteditor: 2.8.0
- files_trashbin: 1.6.0
- files_versions: 1.9.0
- files_videoplayer: 1.5.0
- firstrunwizard: 2.5.0
- gallery: 18.3.0
- logreader: 2.1.0
- lookup_server_connector: 1.4.0
- nextcloud_announcements: 1.5.0
- notifications: 2.4.1
- oauth2: 1.4.2
- occweb: 0.0.4
- password_policy: 1.6.0
- previewgenerator: 2.1.0
- privacy: 1.0.0
- provisioning_api: 1.6.0
- recommendations: 0.4.0
- serverinfo: 1.6.0
- sharebymail: 1.6.0
- support: 1.0.0
- survey_client: 1.4.0
- systemtags: 1.6.0
- theming: 1.7.0
- twofactor_backupcodes: 1.5.0
- twofactor_u2f: 3.0.1
- updatenotification: 1.6.0
- viewer: 1.1.0
- workflowengine: 1.6.0
Disabled:
- admin_audit
- encryption
- files_external
- user_ldap
```
</details>
**Nextcloud configuration:**
<details>
<summary>Config report</summary>
```
{
"system": {
"instanceid": "***REMOVED SENSITIVE VALUE***",
"passwordsalt": "***REMOVED SENSITIVE VALUE***",
"secret": "***REMOVED SENSITIVE VALUE***",
"trusted_domains": [
"cloud.zweiiconkram.de"
],
"datadirectory": "***REMOVED SENSITIVE VALUE***",
"overwrite.cli.url": "http:\/\/cloud.zweiiconkram.de",
"dbtype": "mysql",
"version": "16.0.4.1",
"dbname": "***REMOVED SENSITIVE VALUE***",
"dbhost": "***REMOVED SENSITIVE VALUE***",
"dbport": "",
"dbtableprefix": "oc_",
"dbuser": "***REMOVED SENSITIVE VALUE***",
"dbpassword": "***REMOVED SENSITIVE VALUE***",
"logtimezone": "UTC",
"installed": true,
"maintenance": false,
"theme": "",
"loglevel": 2,
"tempdirectory": ".../tmp\/nextcloud",
"mail_smtpmode": "smtp",
"mail_smtpsecure": "ssl",
"mail_from_address": "***REMOVED SENSITIVE VALUE***",
"mail_domain": "***REMOVED SENSITIVE VALUE***",
"mail_smtpauthtype": "LOGIN",
"mail_smtpauth": 1,
"mail_smtphost": "***REMOVED SENSITIVE VALUE***",
"mail_smtpport": "465",
"mail_smtpname": "***REMOVED SENSITIVE VALUE***",
"mail_smtppassword": "***REMOVED SENSITIVE VALUE***",
"app_install_overwrite": [
"occweb"
]
}
}
```
</details>
**Are you using external storage, if yes which one:** no
**Are you using encryption:** no
**Are you using an external user-backend, if yes which one:** no
### Client configuration
**Browser:** Mozilla Firefox 68.0.1
**Operating system:** Manjaro Linux
zoo3
September 28, 2022, 9:11am
11
I am willing to give up any further search for a solution, but I would like to know one thing.
When a user accesses the NC, the server returns various X headers twice.
Can you post the output of nginx -T?
This topic was automatically closed 90 days after the last reply. New replies are no longer allowed.