Originally published at: https://nextcloud.com/blog/security-in-nextcloud-how-to-block-99-9-of-attacks/
If tech sites would write about every individual data leak, they’d have no time to cover anything else. Generally, only email-and-password leaks numbered in the millions get covered. LinkedIn: 164 million. Adobe: 38 million. MySpace: 359 million. Facebook: 200 to 600 million.
It should be painfully clear that you can’t count on large tech companies to secure data sufficiently. The more important point here is, however, that passwords do not offer sufficient security. Most experts agree that it is time for a radical change. But how? A few solutions exist.
Password managers and single sign-on
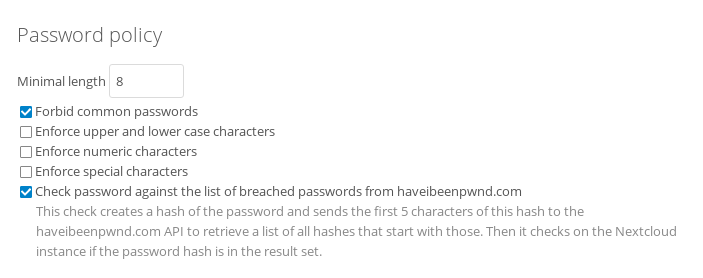
There are dozens of websites like Have I Been Pwned who inform users about theft of their accounts – Nextcloud uses this service to block users picking a leaked combination of username and passwords. The problem here is, of course, that users tend to re-use passwords across services. Password managers offer a solution to this, automatically generating a secure password for each site a user uses. While that does create a single location which could be hacked, there have been no known, large password manager leaks yet.
Another solution is single sign-on. Users can log into various services using their Google or Facebook account. The advantage is, indeed, that you only need to remember one password. The downside is, of course, that these companies gain incredible power and know everything the user does. The vendor-lock-in is severe. Users who wanted to cancel Facebook accounts due to the continuing stream of security, privacy and ethical violations discovered they would lose attached accounts. For example, a Spotify account, with all favorite music and playlists, would disappear as well.
The best solution: second-factor authentication
A far better solution is second-factor authentication (2fa). This essentially means that rather than logging in with a single method of identity verification, like knowledge of a password, a service will ask for a second verification factor. For example, a code the user receives in a SMS or from an app. This would prove that not only does the user know the password, he/she also has his or her phone on them. An attacker would of course have a much harder time getting their hands on both.
Is this more secure? You bet it is. While SMS itself is not the most secure method, Microsoft has estimated that 99.9% of all attacks on Hotmail and Outlook accounts is blocked by 2fa.
So why does not everybody use a second factor like an SMS to secure logging in? There is a variety of reasons for this. With regards to SMS as second factor, users are worried about the privacy implications. They are not comfortable handing over their phone number to a service, and those worries are not unjustified. Last year, it turned out that Facebook was using the phone numbers users gave for second-factor authentication for advertisement.
But there are other issues. Two-factor authentication via SMS is relatively easy, but other factors, like TOTP, which requires users to install an app, scan a qr code on the screen and then manually enter codes, are far more complicated. Or expensive – while hardware keys are easy to use and very secure, the prices are typically over 50 euro for a key.
2FA in Nextcloud: flexible and easy
So 2FA is a great solution, but it tends to complicate things. How does Nextcloud deal with this dilemma?
Our security team always works with two simple but important assumptions: if it is difficult to use, it is less secure. And not all users are the same!
We therefore designed a number of second factors and allow administrators and users to enable and use any number of them. Currently, the following are supported and we’ll explain each of them quickly:
- Time-based One-Time Password (TOTP, including Google Authenticator or similar apps)
- Universal 2nd Factor hardware tokens (U2F, like Yubikeys or Nitrokeys, also supports NFC)
- Gateways: SMS, secure messaging apps Telegram, Signal and more
- Code in an email
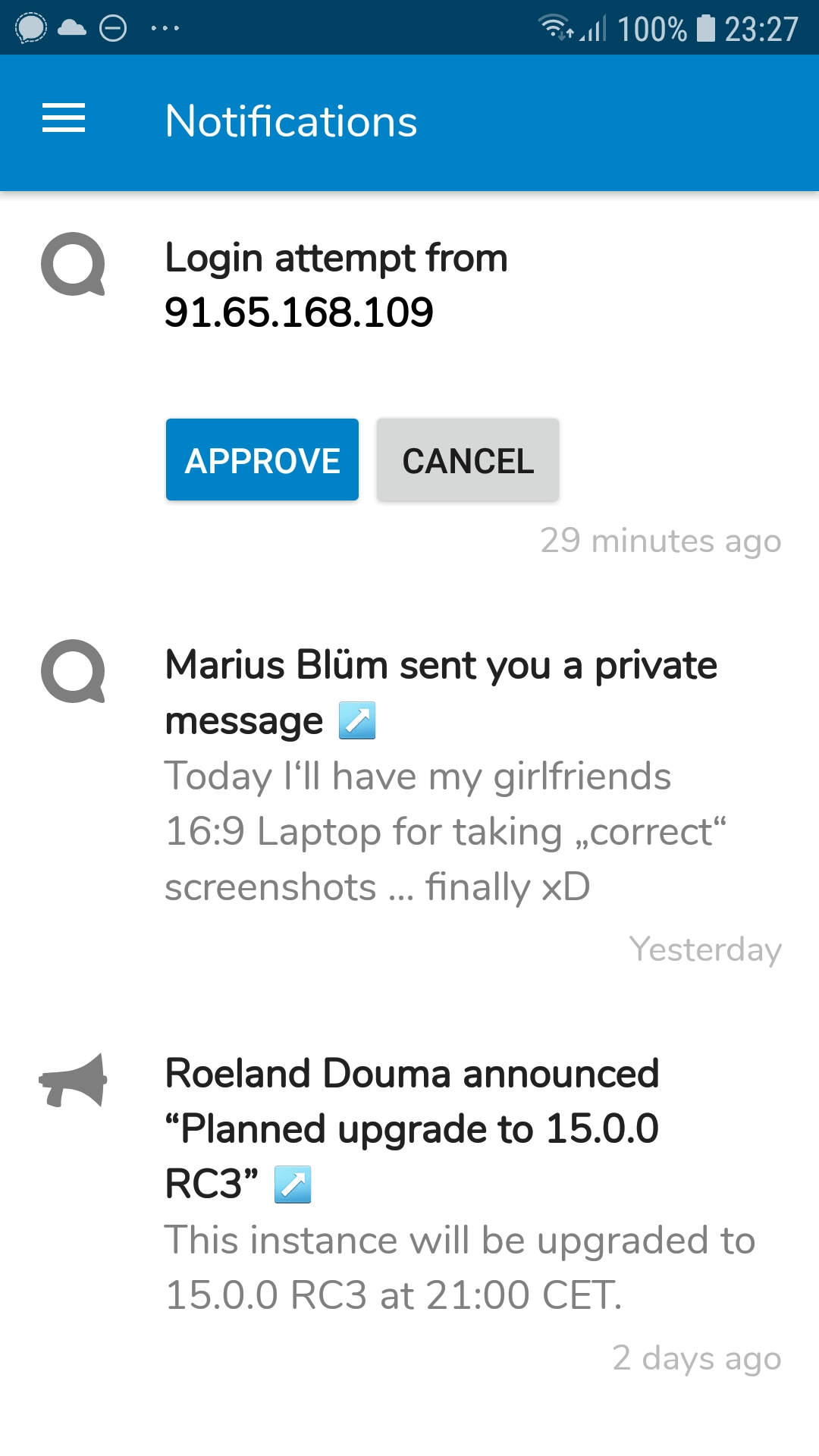
- Notification (just click to approve login on an existing device like phone)
- User backup code (User has to generate these in advance and store them in a safe location)
- Administrator backup code (creating those can be delegated to group admins)
Now, as you can imagine, each of these methods has its downsides and benefits. SMS are quite easy – if you have set it up as administrator and if you trust the telephone network. Signal and Telegram are nice as well, but it is hard to guarantee that all users have these chat apps!
TOTP has many apps available and can be used on many devices but is more complicated, U2F is very secure but expensive. Receiving a code in an email is a familiar method but emails can be intercepted. Notifications are supremely easy to use and secure. That last option should not be missing on Nextcloud installations!
Backup codes are a great way to ensure users don’t get stuck without being able to log in.
Let’s dive deeper into all these methods so you know what their benefits and downsides are, and which you should consider enabling on your Nextcloud server.
(Time-based) One-Time Password
This ‘factor’ is a device-generated code. This code can be used to log in, usually only once. An OTP code can have an expiration date, though often they are quite long. The user has to enter them to log in.
The popular time-based variant changes the code frequently – the most used TOTP standard generates 6 digits every 30 seconds. There are hardware tokens which have a simple display showing the codes. On mobile phones, various apps for implement this standard, from the Google Authenticator app to various free and paid alternatives.
To set up TOTP, users have to give the TOTP device a long code to initiate the connection, in many cases this can be done by scanning a QR code to avoid having to type anything.
During use, a TOTP device does not need to communicate with the service being used, it does not even need to know anything about it. This thus works without connection or on a local, firewalled network.
A downside of TOTP is that it is vulnerable to various forms of man-in-the-middle attacks. A hacker can set up a fake website designed to trick visitors into submitting their credentials. When a user falls into the trap and enters their information, the hacker gains access to their account. This attack is not easy to pull off: users have to visit the site of the attacker and mistake it for their usual website.
When enabled by the admin, users can set up TOTP in their security settings:
Universal 2nd Factor hardware tokens
U2F is a bit similar to OTP, in that a device generates a code. But, unlike OTP, users don’t have to enter it. The process has to be handled by the client, for example a browser, or an application, directly. A U2F device thus has to be connected physically. USB or NFC are the most typically used methods for this.
The service will communicate with the U2F device, using a public key encryption and a challenge-response model, which makes it impossible to ‘attack’ using the man-in-the-middle attack that (T)OTP is vulnerable to.
The downside is the need of support for the devices. Browsers and apps all have to work with this and connecting a phone to a computer via USB or NFC, or connecting a hardware U2F key to a phone can be difficult in some situations.
U2F can also be setup by users in their security settings:

Gateways: SMS, secure messaging apps Telegram, Signal and more
Many users are probably familiar with receiving a code through SMS and entering it into a website login portal. Nextcloud supports connecting to such a ‘SMS gateway’, and can also use Telegram and Signal through this system. While it is not extremely hard to intercept an SMS, Telegram and Signal messages are quite secure. Unfortunately, not many users have these apps installed, so they are not suitable as general solutions for all users.
Another issue is that it takes some work from the system administrator to set up and configure these methods. You can find documentation here.
Code in an email
The fourth method is also rather familiar to users: receiving a code in their email. While email, too, is relatively easy to intercept, this nonetheless makes logging in a lot more secure and it is easy to set up and use.
Notification
Probably the easiest way for users to log into their Nextcloud is through a notification on an existing device or session. Nextcloud will simply create a notification, allowing the user to click ‘approve’ or ‘deny’. This works from a browser session, mobile phone and desktop client and requires no configuration on the side of the user.
User backup code
In the user security settings, a option for creating backup codes is given. This allows the user to generate a series of codes and store them in a secure location. Each of these codes can be used, once, as second factor to log into Nextcloud. If all other methods fail, this gives the user still access to their account…
Administrator backup code
In case all else fails, users can contact their system administrator. If enabled, the admin can create a one-time login code the user can use as second factor. To make it easy for companies to delegate this to personnel in a support team without giving them full administrator access, group admins also have the ability to create second-factor backup codes for their users.
Enable two-factor authentication
Recapping: second-factors are incredibly important to secure accounts. While they typically have some drawbacks, the wide range of options in Nextcloud, including the incredibly user friendly ‘notification’ option, make 2fa a must-have on Nextcloud. Enable it today and leave feedback on your experience below!