Hello,
I am new to this community and it’s the first time that I’ll address a question here.
Nextcloud version: 18.0.4
Operating system and version: Ubuntu 18.04.4 LTS
Apache2
PHP version: 7.4.7
What I tried to do:
I create Nextcloud users via the “User provisioning API” by sending an HTTP request. For the new Nextcloud users I only specify userid, email and language, but not the password. Because I like the users to get a welcome email and be able to set their own password.
While testing, I noticed that randomly some users could not be created.
For random users, I received the following error.
<ocs>
<meta>
<status>failure</status>
<statuscode>107</statuscode>
<message>Password needs to contain at least one numeric character.</message>
<totalitems></totalitems>
<itemsperpage></itemsperpage>
</meta>
<data/>
</ocs>
My password policy settings are as follows:
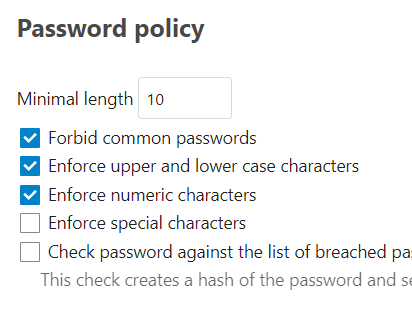
Unfortunately, there was no helpful information or error message in my nextcloud.log file.
When I disable ‘Enforce numeric characters’ everything works successfully.
As a consequence, I had a look at apps/password_policy/lib/Generator.php and apps/password_policy/lib/PasswordValidator.php .
What could be the reason for this behaviour?
And where does apps/password_policy/lib/PasswordValidator.php throw an HintException when for example NumericCharacterValidator would fail?
Thank you very much for your help.
class PasswordValidator {
/** @var IAppContainer */
private $container;
/** @var ILogger */
private $logger;
public function __construct(IAppContainer $container, ILogger $logger) {
$this->container = $container;
$this->logger = $logger;
}
/**
* check if the given password matches the conditions defined by the admin
*
* @param string $password
* @throws HintException
*/
public function validate(string $password): void {
$validators = [
CommonPasswordsValidator::class,
LengthValidator::class,
NumericCharacterValidator::class,
UpperCaseLoweCaseValidator::class,
SpecialCharactersValidator::class,
HIBPValidator::class,
];
foreach ($validators as $validator) {
try {
/** @var IValidator $instance */
$instance = $this->container->query($validator);
} catch (QueryException $e) {
//ignore and continue
$this->logger->logException($e, ['level' => ILogger::INFO]);
continue;
}
$instance->validate($password);
}
}
}
Additional information /config/config.php :
$CONFIG = array (
'instanceid' => '********',
'passwordsalt' => '*****************************************',
'secret' => *****************************************,
'trusted_domains' =>
array (
0 => ‘MY_IP’,
),
'datadirectory' => '/opt/nextcloud/data',
'dbtype' => 'mysql',
'version' => '18.0.4.2',
'overwrite.cli.url' => 'http://MY_IP/nextcloud',
'dbname' => 'nextcloud',
'dbhost' => 'localhost',
'dbport' => '',
'dbtableprefix' => 'oc_',
'dbuser' => 'NEXTCLOUDUSER',
'dbpassword' => '*********',
'installed' => true,
'maintenance' => false,
'mysql.utf8mb4' => true,
'memcache.local' => '\\OC\\Memcache\\Redis',
'logtimezone' => 'Europe/Zurich',
'enable_previews' => false,
'skeletondirectory' => '',
'mail_from_address' => 'EMAIL',
'mail_smtpmode' => 'smtp',
'mail_sendmailmode' => 'smtp',
'mail_domain' => 'DOMAIN',
'mail_smtphost' => 'MY_IP',
'theme' => 'ThemeBlue',
'mail_template_class' => '\\OC\\Mail\\EMailTemplate',
'mail_smtpport' => '3025',
'knowledgebaseenabled' => false,
'allow_user_to_change_display_name' => false,
);