Nextcloud version: 13.0.6
Operating system and version: Ubuntu 18.04
Apache or nginx version: Apache2
PHP version: 7.2
Nextcloud installed with
sudo snap install nextcloud
The issue you are facing:
LDAP connects and I can see users and groups
LDAPS fails to connect
I have copied a .crt version of the (internal private) root CA as a .crt and referenced it in /etc/ldap/ldap.conf
#TLS certificates (needed for GnuTLS)
TLS_CACERT /etc/ssl/certs/ca-certificates.crt
TLS_CACERT /etc/ssl/certs/ca-1.crt
I have tested the .crt file is valid with
openssl x509 -in /etc/ssl/certs/ca-1.pem -text -noout
I tested that the certificate being provided on the LDAP server (2012r2) is valid with
openssl s_client -connect dc.domain.com:636
then taking the certificate portion and validating it in the same way as the root CA certificate to ensure that it has not expired etc.
Is this the first time you’ve seen this error? (N):
Steps to replicate it:
- change URI from ldap:// to ldaps:// and port from 389 to 636
- click “Detect Base DN” button
- see error “Could not detect Base DN, please enter it manually.”
The output of your Nextcloud log in Admin > Logging:
|Warning|user_ldap|Configuration Error (prefix ): login filter does not contain %uid place holder.|2018-10-29T23:27:39+0000|
|---|---|---|---|
|Warning|user_ldap|Configuration Error (prefix ): No LDAP Login Filter given!|2018-10-29T23:27:39+0000|
|Warning|user_ldap|Configuration Error (prefix ): login filter does not contain %uid place holder.|2018-10-29T23:27:39+0000|
|Warning|user_ldap|Configuration Error (prefix ): No LDAP Login Filter given!|2018-10-29T23:27:39+0000|
|Warning|user_ldap|Configuration Error (prefix ): login filter does not contain %uid place holder.|2018-10-29T23:27:37+0000|
|Warning|user_ldap|Configuration Error (prefix ): No LDAP Login Filter given!|2018-10-29T23:27:37+0000|
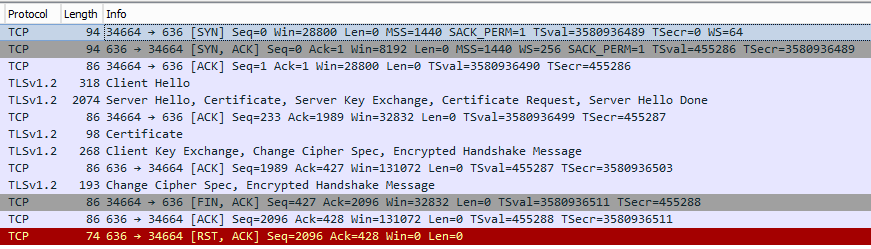
A packet capture on the 2012r2 DC shows the connection.
Several other devices and application connect over LDAPS for user authentication with no issues.
I can also connect with ldapsearch with the following stanza
ldapsearch -d1 -H ldaps://dc.domain.com:636 -b "DC=domain,DC=com" -D "CN=LDAP-Lookup,OU=ldap-accounts,DC=domain,DC=com" -W '(&(|(mail=*)(proxyAddresses=*))(sAMAccountName=*))'
If I remove the line with the private root CA from ldap.conf, the connection fails with
ldapsearch TLS: peer cert untrusted or revoked (0x42)
As ldapsearch will connect when ldap.conf point to a valid certificate, but nextcloud does not, to my untutored eye that at least when installed via snap, nextcloud does not utilise /etc/ldap/ldap.conf
As I had a premise, I then set out to prove it, in one terminal, I setup inotifywait to watch the ldap.conf file
sudo inotifywait -m /etc/ldap/ldap.conf
In another terminal I ran the ldapsearch command, and saw the following output from inotifywait
uadmin@nextcloud-1:~$ sudo inotifywait -m /etc/ldap/ldap.conf
Setting up watches.
Watches established.
/etc/ldap/ldap.conf OPEN
/etc/ldap/ldap.conf ACCESS
/etc/ldap/ldap.conf CLOSE_NOWRITE,CLOSE
I then restarted the nextcloud snap
sudo snap nextcloud restart
inotifywait did not report any further access to the file
I removed the existing server line, and added a new server line, and clicked on the Test Base DN button I still did not see any access to the ldap.conf file.
From
https://docs.nextcloud.com/server/13/admin_manual/configuration_user/user_auth_ldap.html
“The certificate is announced in the system’s LDAP configuration file (usually /etc/ldap/ldap.conf)”
This would appear to be incorrect.