Hi,
my NC-server is protected by fail2ban. Now I found out that this protection only works for the main user-authentication, but not for password-protected public links. Is there also a solution for this?
Thanks

Hi,
my NC-server is protected by fail2ban. Now I found out that this protection only works for the main user-authentication, but not for password-protected public links. Is there also a solution for this?
Thanks

Has anybody managed to protect PW-protected public share-links by “special settings” in fail2ban?
I got this Regex-Filter Information
^<HOST> - - .*"POST /s/******ENTER*HASH*******/authenticate/showShare HTTP/2.0" 200
But it did not work for me. Maybe the filter has to be updated?

Here is the solution for the problem. The solution works fine here with the latest version of nextcloudpi:
let’s presume, that the link for the password protected public share is:
https://mynextcloud.dyndns.org/index.php/s/oNrtAVXLQKeqC4M/authenticate/showShare
then oNrtAVXLQKeqC4M in the URL is the share specific hash.
to protect the public share password form with fail2ban you have to do the following steps:
1.create a new fail2ban-Filter:
$ sudo nano /etc/fail2ban/filter.d/ncshareprotection.conf
insert:
[Definition]
failregex = ^<HOST> - - \[.*\] "POST .*/s/oNrtAVXLQKeqC4M/authenticate/showShare HTTP/2.0" 200 .*
datepattern = ^[^\[]*\[(%%d/%%b/%%Y:%%H:%%M:%%S %%z)\]
ignoreregex =
2. Let the jail.local know of the existence of our new filter:
$ sudo nano /etc/fail2ban/jail.local
scroll down to the end and insert:
[ncshareprotection]
enabled = true
port = http,https
filter = ncshareprotection
logpath = /var/log/apache2/nc-access.log
maxretry = 3
Then restart fail2ban:
$ sudo service fail2ban restart
Let’s take a look if it works:
$ fail2ban-regex /var/log/apache2/nc-access.log /etc/fail2ban/filter.d/ncshareprotection.conf
if you want to protect all the password protected public shares in nextcloud, then the following filter should work:
[Definition]
failregex = ^<HOST> - - \[.*\] "POST .*/s/.*/authenticate/showShare HTTP/2.0" 200 .*
datepattern = ^[^\[]*\[(%%d/%%b/%%Y:%%H:%%M:%%S %%z)\]
ignoreregex =
if you have activated and configured e-mail alerts in fail2ban you will receive an email every time an ip is banned.
have fun
I think it makes less sense for fail2ban for an individual link. It is an individual link and not a start-page or port 22 with standard user.
well, it’s less likely that a hacker will find the cryptic URL of a share - password protected or not.
But if he finds the link he could try to brute-force the password and you wouldn’t be alerted.
With the fail2ban protection you are protected and f2b sends you the alert-email, if someone tries to break in.
Hi rebootnow,
a big THANKS for your help and your detailled information ! 
I will test it soon. Although I tested it so far, I am sure you are right.

I think my provider with thousands or millions of users does not need it
https://nc.nl.tab.digital/s/t8YKLcaz8zLTGdH
It seems the time increases on wrong passwords.
Perhaps it is a standard nextcloud feature. I do not know.
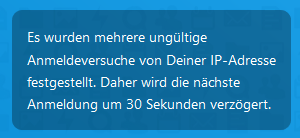
Screenshot from login page but wrong login only from shared link above.
Brute force protection is enabled by default on Nextcloud.
https://docs.nextcloud.com/server/19/admin_manual/configuration_server/bruteforce_configuration.html
After a successfull login the attempts will be cleared.
That’s great! I didn’t know that. Thanks for the info.
Nevertheless you won’t be alerted if someone tries to brute-force the share-password.
Ok. But nobody goes this way to hack your nextcloud.